Background
Recently, we have monitored an on-chain attack on the DCFToken project on BnbSmartChain.
https://bscscan.com/tx/0xa88b907960c3c5a9dfcfd28aff12136359034653e34fa6d7bb9a6ef9c7a0532f
The attacked project was DCFToken, and the attacker made a profit of approximately 8,800 USD through this attack.
Attack and incident analysis
First, the attacker created a new contract and then called it.
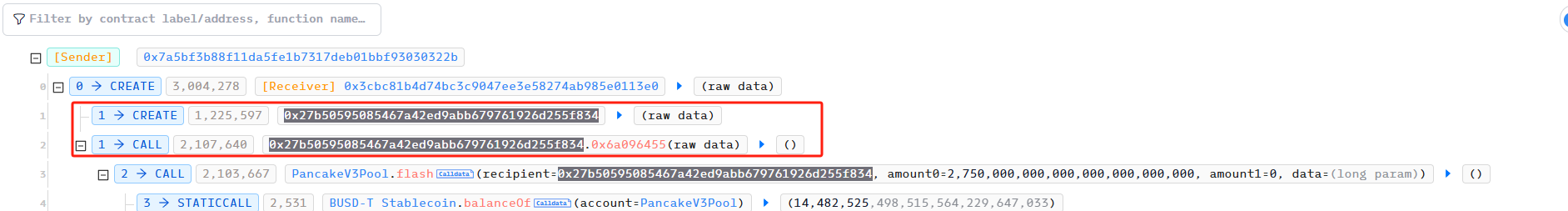
Next, the contract borrowed 2,750,000 BUSDT from PancakeSwapV3Pool using flash.
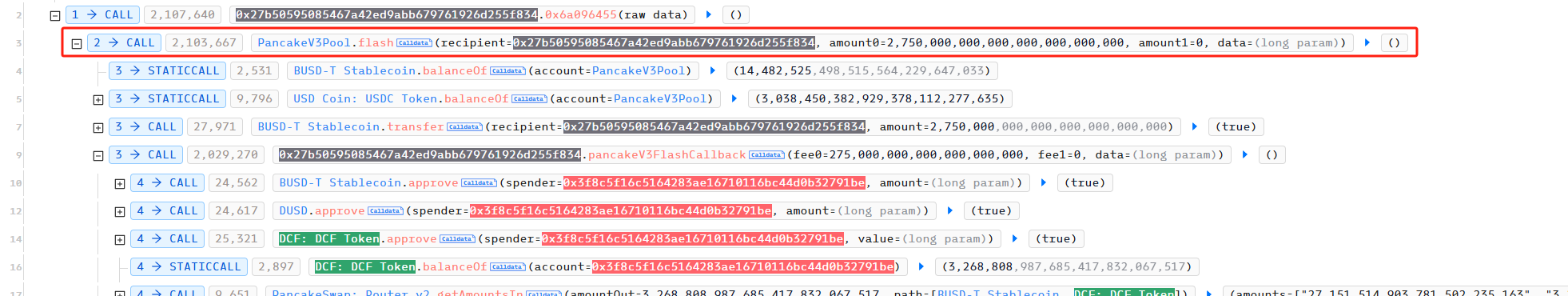
Subsequently, the attacker used the initial funds borrowed from the flash to launch an attack against DCFToken. In the first step, the attacker used the exchange function of the project's unopened contract (BUSDT exchange for DUSD) to exchange all DUSD of the contract with BUSDT. The signature of this function is 0xabb81c12.
Through decompilation, we get the specific implementation of this function as follows:
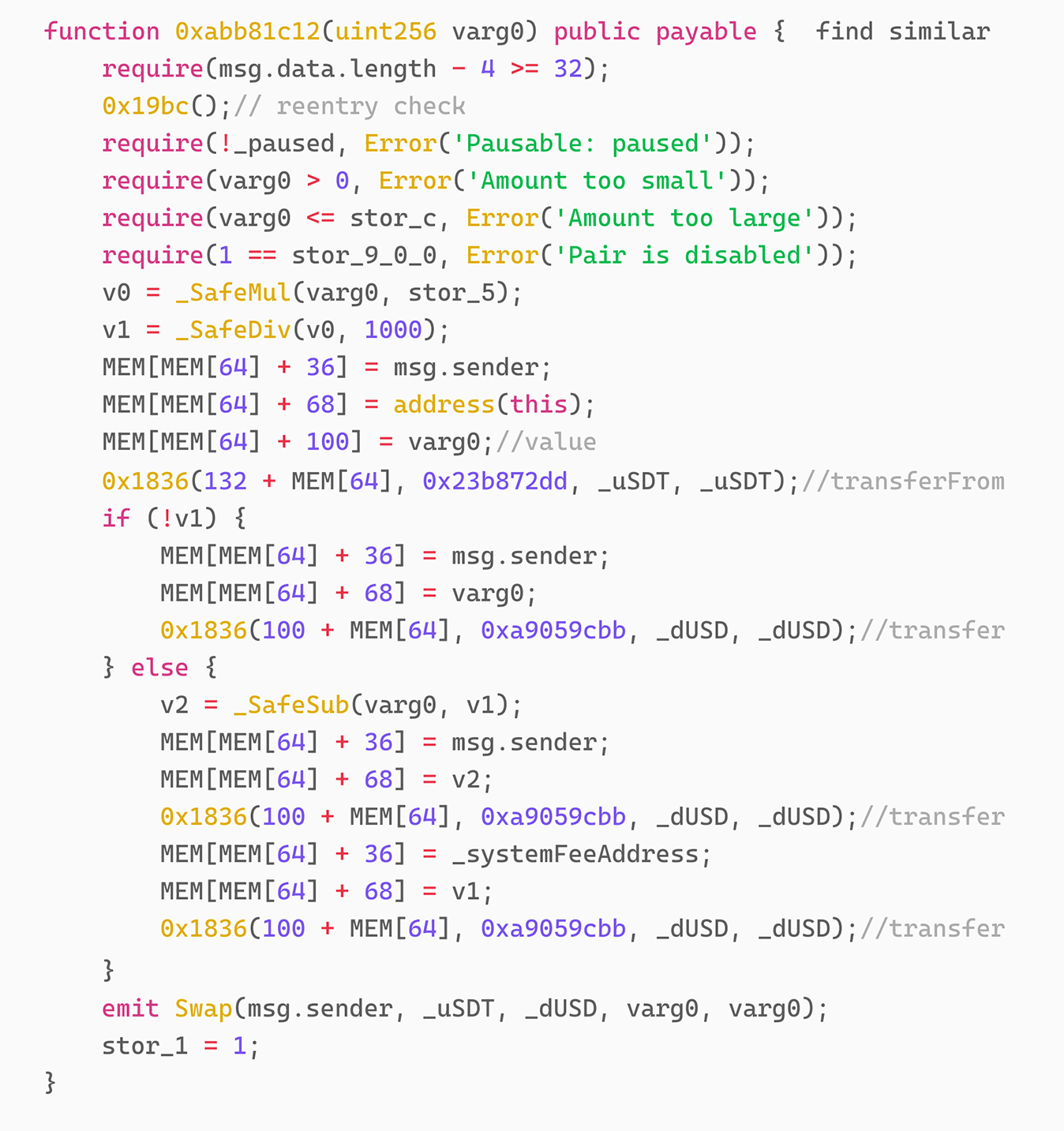
first step:
From the code, we can see that the exchange ratio of BUSDT and DUSD is controlled by stor_5. Since stor_5 was 1000 during the attack, the exchange ratio of BUSDT and DUSD was 1:1. Therefore, the attacker used 10,927 BUSDT to exchange all the DUSD in the contract.
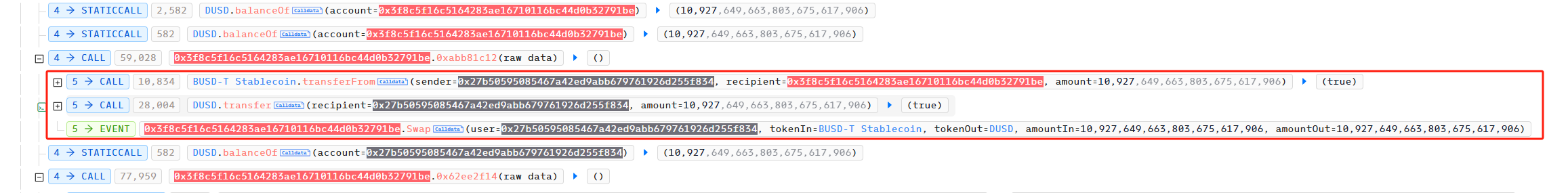
Step 2:
Use DUSD to buy DCFToken. The signature of this function is 0x62ee2f14. Through decompilation, we can see that the specific implementation is as follows:
In simple terms, this function implements the function of using DUSD to purchase DCFToken, where the purchase price is determined by the price of BUSDT and DCFToken in PancakeSwapV2. This means that in the logic of this function, the price of DUSD and BUSDT is 1:1.
Next, 1% of the purchased DCFToken will be transferred to the system address.
The attacker then used all the DUSD purchased in the first step to purchase DCFToken.
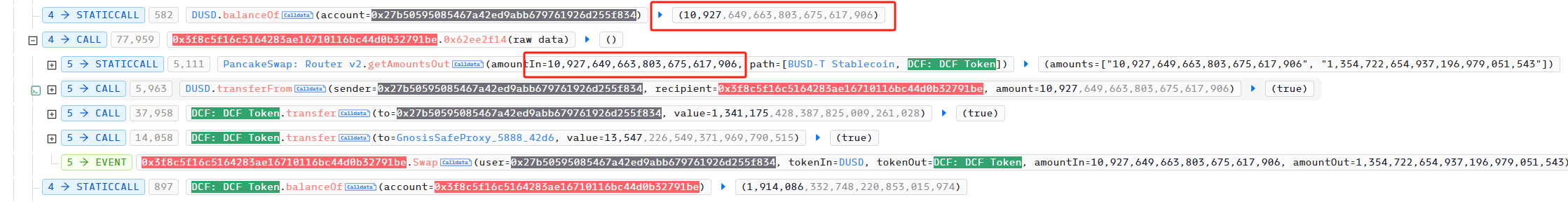
Then, the attacker repeated the above steps until he bought out the DCF in the contract used by the project to exchange DUSD and DCFToken. Afterwards, the attacker used the exchange function of PancakeSwapV2 to exchange the DCFToken in his hands for BUSDT to manipulate the price of DCFToken. After this exchange, the price of DCFToken rose from 1 BUSDT = 126 DCFToken to 1BUSDT = 3 DCFToken.
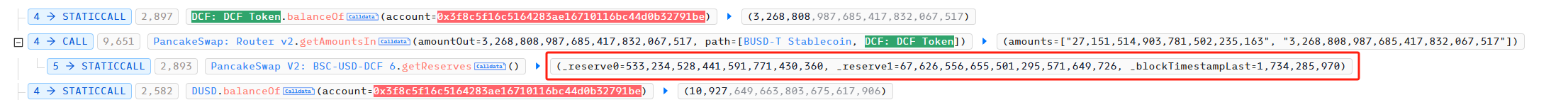
Before redemption:
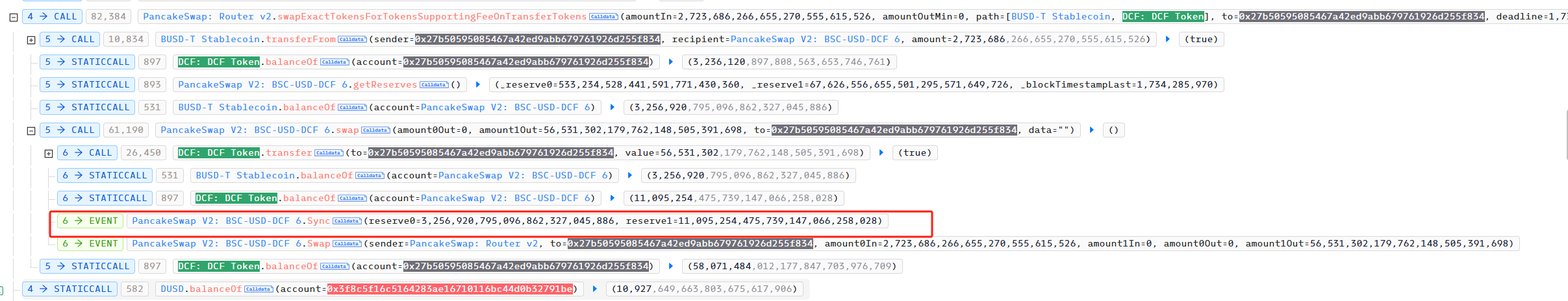
After redemption:
Step 3:
After the attacker emptied the DCFToken in the project contract, he used the DCFToken in the contract to exchange DUSD. The signature of this function is 0xd5088d27, which is similar to using DUSD to purchase DCFToken in the second step. Similarly, the purchase price is determined by the price of BUSDT and DCFToken in PancakeSwapV2. This means that in the logic of this function, the price of DUSD and BUSDT is 1:1. Then, 1% of the purchased DUSD will be transferred to the system address.
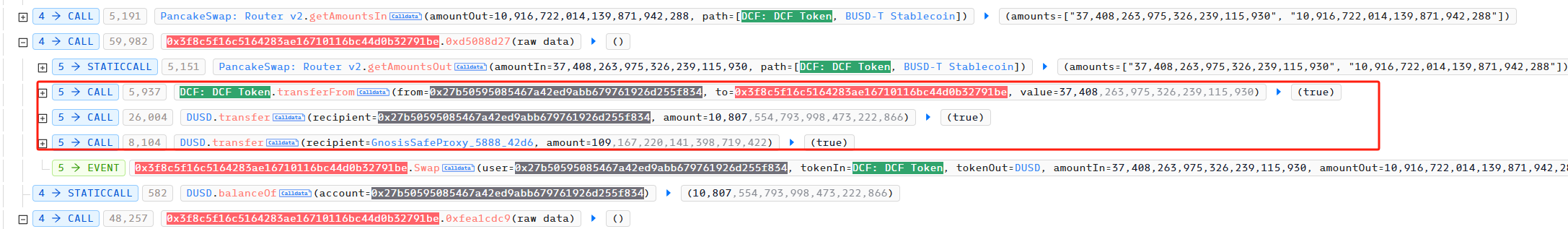
Step 4:
The attacker then used the DUSD to exchange BUSDT function in the project party’s contract. The signature of this function is 0xfea1cdc9, and the exchange ratio is 1:1, but 1% of the BUSDT will be transferred to the project party’s address.
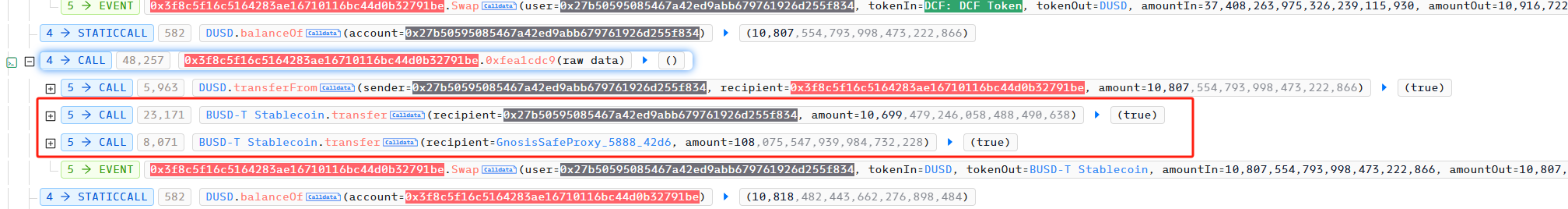
The attacker continues to repeat steps 3 and 4 until all the BUSDT in the project contract is emptied.
Finally, the attacker used the remaining DCFToken to exchange all of it for BUSDT using PancakeSwapV2, and then repaid the flash loan and interest, making a profit of 8,763 BUSDT.
Simply put, the vulnerability of this project appears in the calculation of the exchange price. The price of DCFToken depends on PancakeSwap, but the exchange using the project contract does not affect the price of DCFToken. Therefore, the attacker first uses BUSDT to exchange DUSD and then exchange it for DCF(99%) to empty DCFToken, then uses PancakeSwap's swap to increase the price of DCFToken, and finally uses DCFToken to exchange DUSD(99%) and then exchange it for BUSDT(99%) to complete the profit.
Summarize
The main cause of this vulnerability is that the DCFToken project contract uses a single source, PancakeSwapV2, to calculate the price of DCFToken, which causes the price to be manipulated by the attacker, and ultimately arbitrage using the price difference. It is recommended that the project party conduct multiple verifications when designing the economic model, price calculation mechanism, and code operation logic, and try to select multiple audit companies for cross-audits before the contract goes online.
















