Bitcoin has once again broken through its all-time high, approaching $99,000 and approaching the $100,000 mark. Looking back at historical data, scams and phishing activities in the Web3 field emerged one after another during the bull market, with total losses exceeding $350 million. Analysis shows that hackers mainly attack the Ethereum network, with stablecoins as the main target. Based on historical transaction and phishing data, we conducted in-depth research on attack methods, target selection, and success rates.
Cryptographic Security Ecosystem Map
We have broken down and categorized the crypto security ecosystem projects in 2024. In the field of smart contract auditing, there are veteran players such as Halborn, Quantstamp, and OpenZeppelin. Smart contract vulnerabilities are still one of the main attack vectors in the crypto space, and projects that provide comprehensive code review and security assessment services also have their ups and downs.
The DeFi security monitoring section has professional tools such as DeFiSafety and Assure DeFi, which are specifically designed for real-time threat detection and prevention of decentralized financial protocols. It is worth noting the emergence of AI-driven security solutions.
Meme trading has been very popular recently, and security checking tools such as Rugcheck and Honeypot.is can help traders identify some problems in advance.
USDT is the most stolen asset
According to bitsCrunch data, Ethereum-based attacks account for about 75% of all attacks, and USDT is the most attacked asset, with a theft of $112 million, and the average value of each attack on USDT is about $4.7 million. The second most affected asset is ETH, with a loss of about $66.6 million, followed by DAI, with a loss of $42.2 million.

It is worth noting that the number of attacks on tokens with lower market capitalization is also very high, indicating that attackers will take advantage of opportunities to steal less secure assets. The largest incident was a complex fraud attack on August 1, 2023, resulting in a loss of $20.1 million.
Polygon is the second most targeted chain by attackers
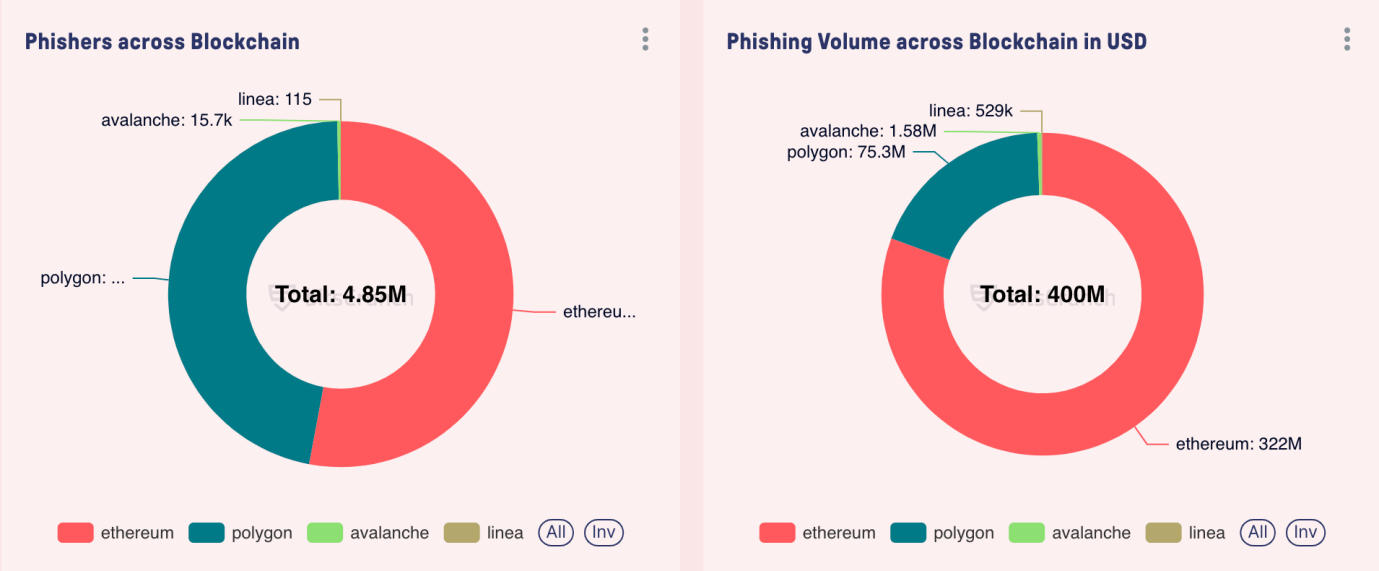
Although Ethereum dominates all phishing incidents, accounting for 80% of phishing transactions, thefts have also been observed on other blockchains. Polygon became the second largest target chain, accounting for about 18% of transactions. Often thefts are closely related to the TVL and daily active users on the chain, and attackers will judge based on liquidity and user activity.
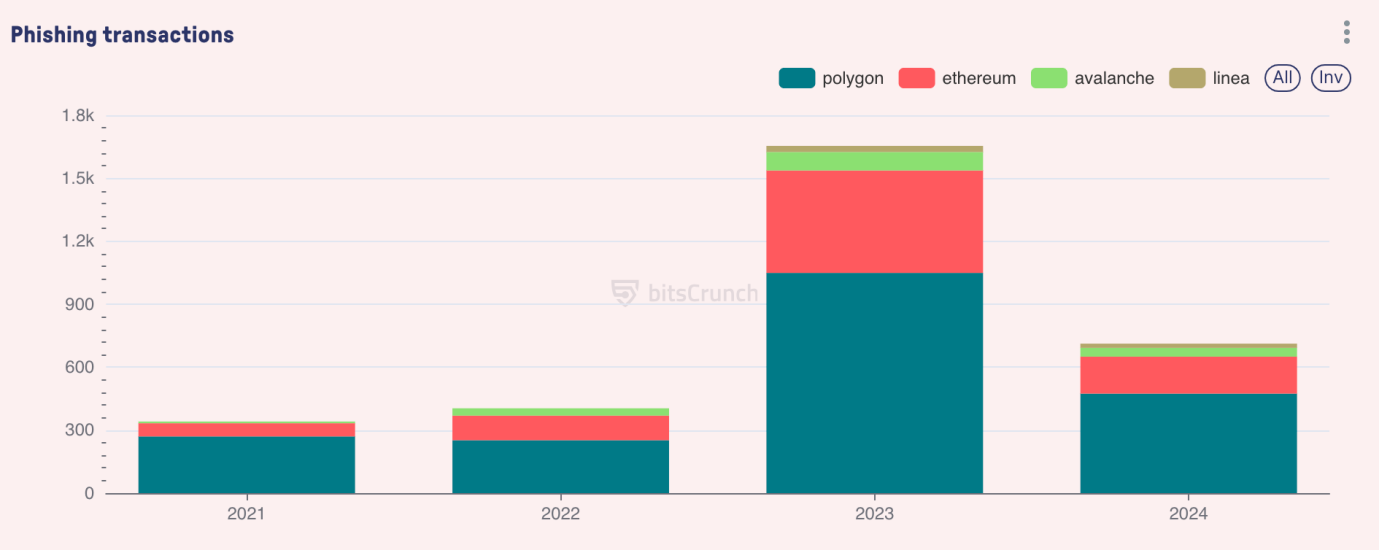
Temporal Analysis and Attack Evolution
There are different patterns in the frequency and size of attacks. According to bitsCrunch data, 2023 is the year with the highest concentration of high-value attacks, with multiple incidents valued at more than $5 million. At the same time, the complexity of attacks has gradually evolved, from simple direct transfers to more complex approval-based attacks. The average time between major attacks (> $1 million) is about 12 days, mainly concentrated around major market events and new protocol releases.
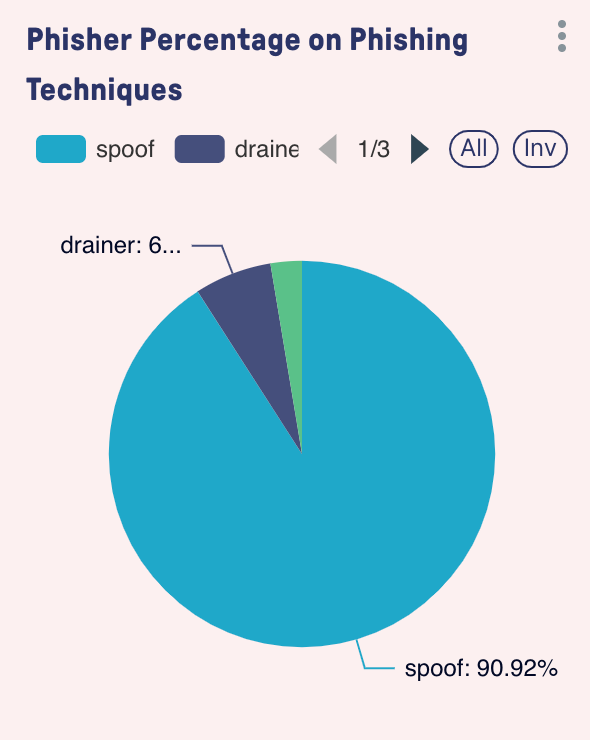
Types of Phishing Attacks
Token Transfer Attack
Token transfer is the most direct attack method. The attacker will manipulate the user to transfer their tokens directly to an account controlled by the attacker. According to bitsCrunch data, the single value of this type of attack is often extremely high, using user trust, fake pages and fraudulent words to persuade victims to voluntarily initiate token transfers.
This type of attack usually follows the following pattern: through similar domain names, completely imitating certain well-known websites to establish a sense of trust, while creating a sense of urgency when users interact with them and providing seemingly reasonable token transfer instructions. Our analysis shows that the average success rate of this type of direct token transfer attack is 62%.
Approve Phishing
Approval phishing is a technically more complex attack method that mainly exploits the interaction mechanism of smart contracts. In this method, the attacker tricks users into providing transaction approval, thereby granting them unlimited spending rights on specific tokens. Unlike direct transfers, approval phishing creates a long-term vulnerability and the victim will gradually drain the funds.
Fake Token Addresses
Address poisoning is a comprehensive and multifaceted attack strategy where an attacker creates transactions using tokens with the same name as legitimate tokens but with different addresses. These attacks exploit users' negligence in address checking to gain benefits.
NFT Zero Dollar Purchase
Zero-dollar purchase phishing attacks specifically target the digital art and collectibles market of the NFT ecosystem. Attackers manipulate users to sign transactions, thereby selling their high-value NFTs at a significantly reduced price or even for free.
Our research uncovered 22 significant NFT zero-purchase phishing incidents during the analysis period, with an average loss of $378,000 per incident. These attacks exploited the transaction signing process inherent in NFT marketplaces.
Distribution of stolen wallets
The data in this chart reveals the distribution pattern of stolen wallets in different transaction price ranges. We found a clear inverse relationship between transaction value and the number of victim wallets - as the price increases, the number of affected wallets gradually decreases.
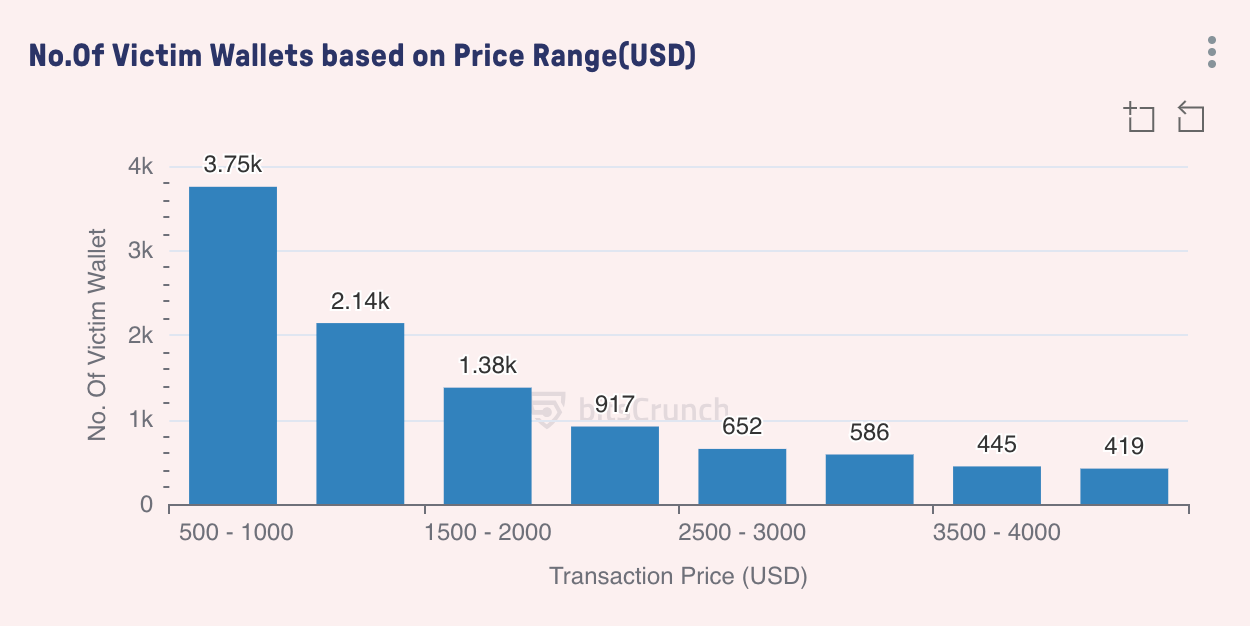
The number of victim wallets with transactions of $500-1000 per transaction was the largest, with about 3,750, accounting for more than one-third. Victims of small transactions often do not pay attention to the details. The number of wallets with transactions of $1000-1500 per transaction dropped to 2,140. Wallets with transactions of more than $3,000 only accounted for 13.5% of the total number of attacks. This shows that the larger the amount, the stronger the security measures, or the victims have to consider more carefully when it comes to large amounts.
By analyzing the data, we reveal the complex and evolving attack methods in the cryptocurrency ecosystem. With the arrival of the bull market, the frequency of complex attacks will increase, the average loss will increase, and the economic impact on project owners and investors will be great. Therefore, not only do blockchain networks need to strengthen security measures, but we ourselves should also pay more attention when trading to prevent phishing incidents.













