Background
On January 4, 2025, we detected multiple attacks on the Ethereum project Sorra. The attack hash is:
https://etherscan.io/tx/0x6439d63cc57fb68a32ea8ffd8f02496e8abad67292be94904c0b47a4d14ce90d
https://etherscan.io/tx/0x03ddae63fc15519b09d716b038b2685f4c64078c5ea0aa71c16828a089e907fd
https://etherscan.io/tx/0xf1a494239af59cd4c1d649a1510f0beab8bb78c62f31e390ba161eb2c29fbf8b
https://etherscan.io/tx/0x09b26b87a91c7aea3db05cfcf3718c827eba58c0da1f2bf481505e0c8dc0766b
The project attacked was Sorra , and the attack caused a total loss of 41,000 USD.
Attack and incident analysis
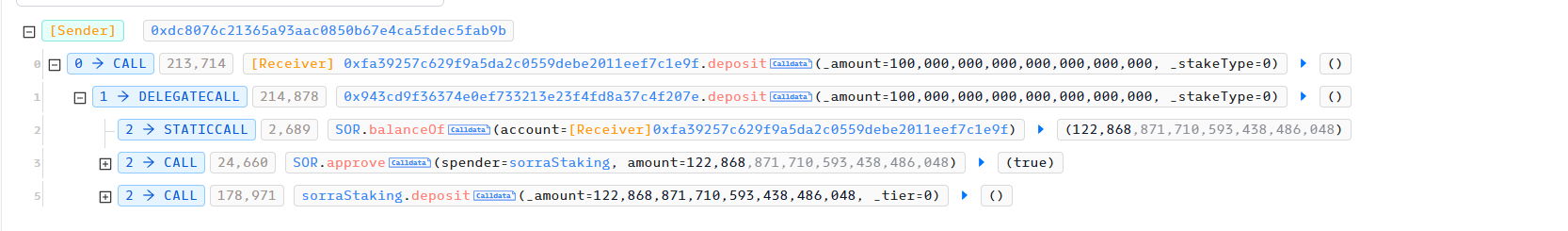
On December 21, 2024, the attacker began preparing for the attack by staking.
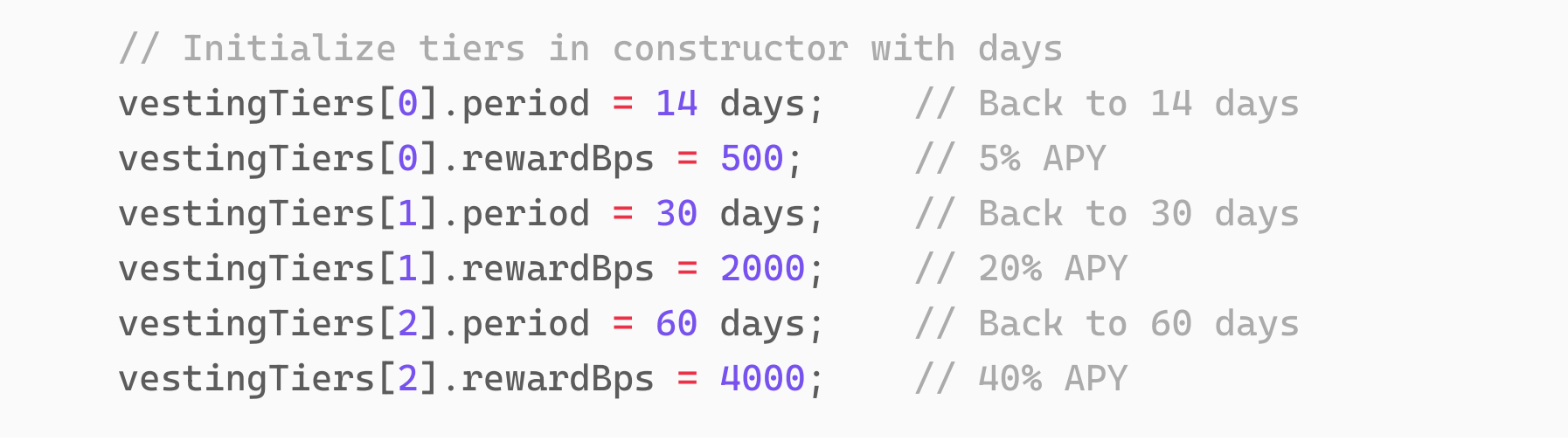
Since the _tier selected for staking is 0, according to the contract, the lock-up period is 14 days.
14 days later, on January 4, 2025, the attacker begins the attack. The attacker sets _amount to 1 in withdraw. Let's take a look at the specific implementation of the withdraw function.
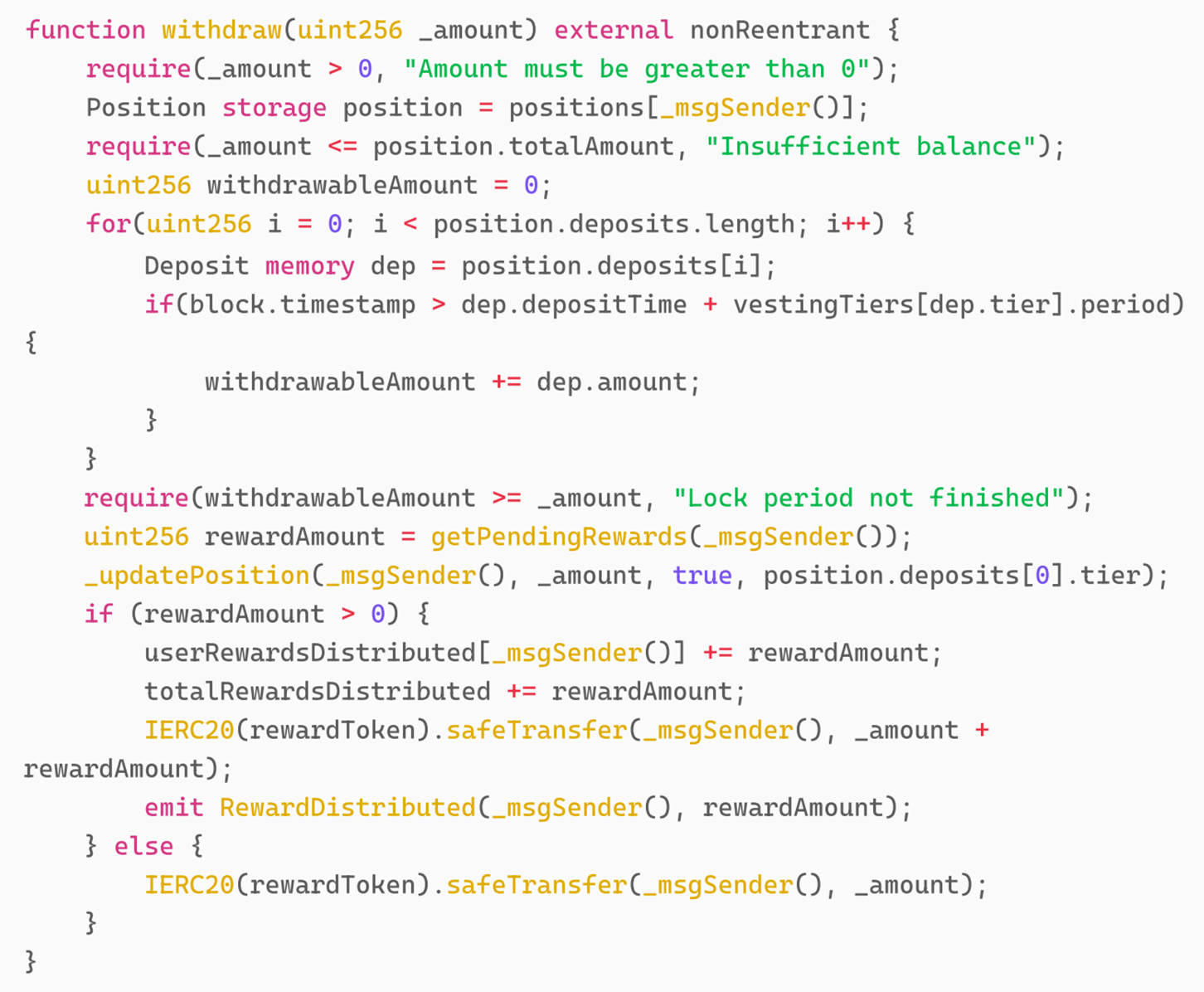
The overall logic of the above code is as follows: first determine whether the user's deposit assets have expired, then calculate the reward, and finally subtract the position.
First, let’s look at how to calculate the reward;
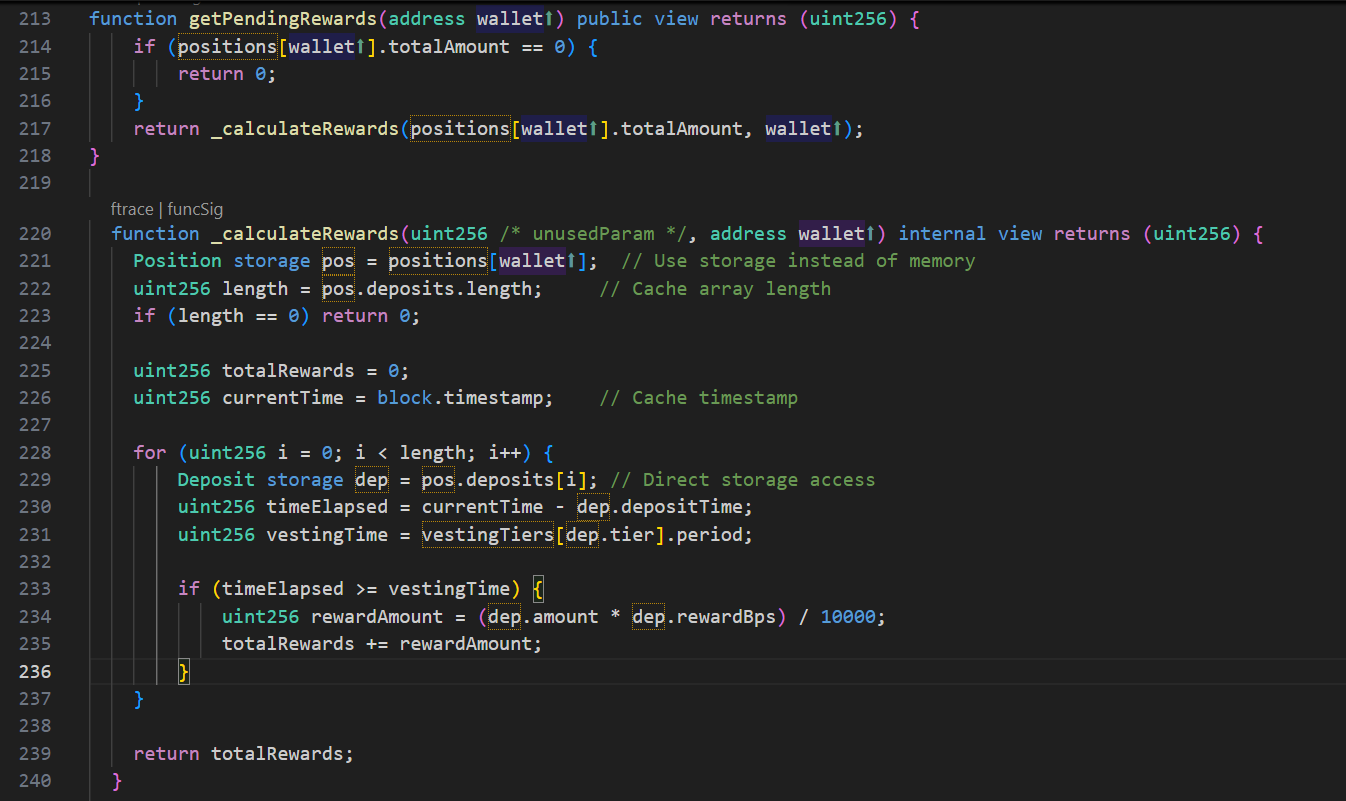
From the code, we can see that the reward calculation is the calculation of the rewards of all matured deposits, which seems to be no problem.
Next, let's look at how to update the position;
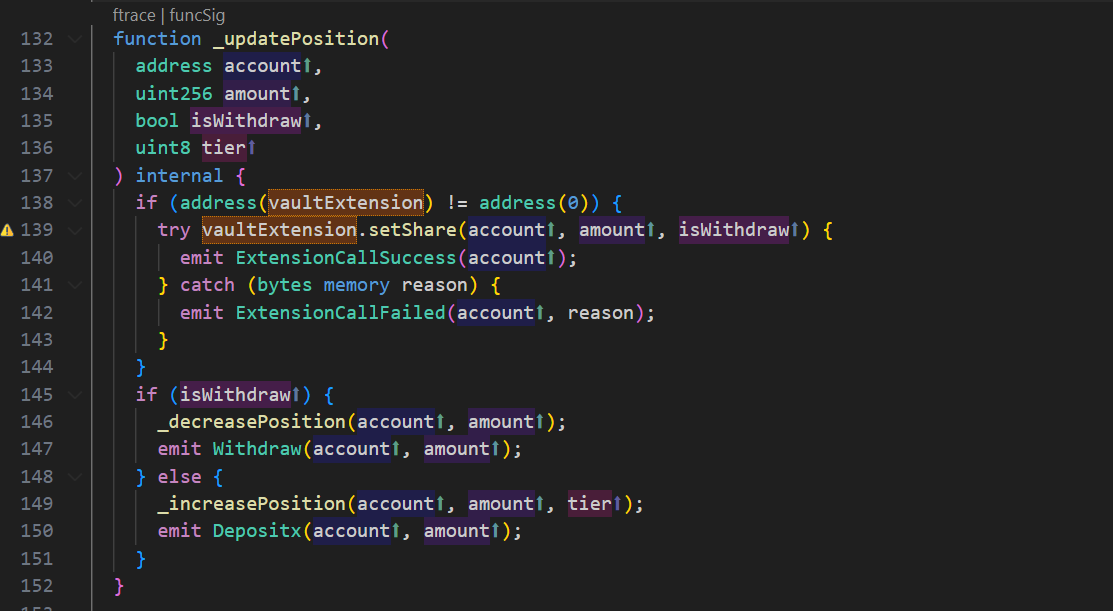
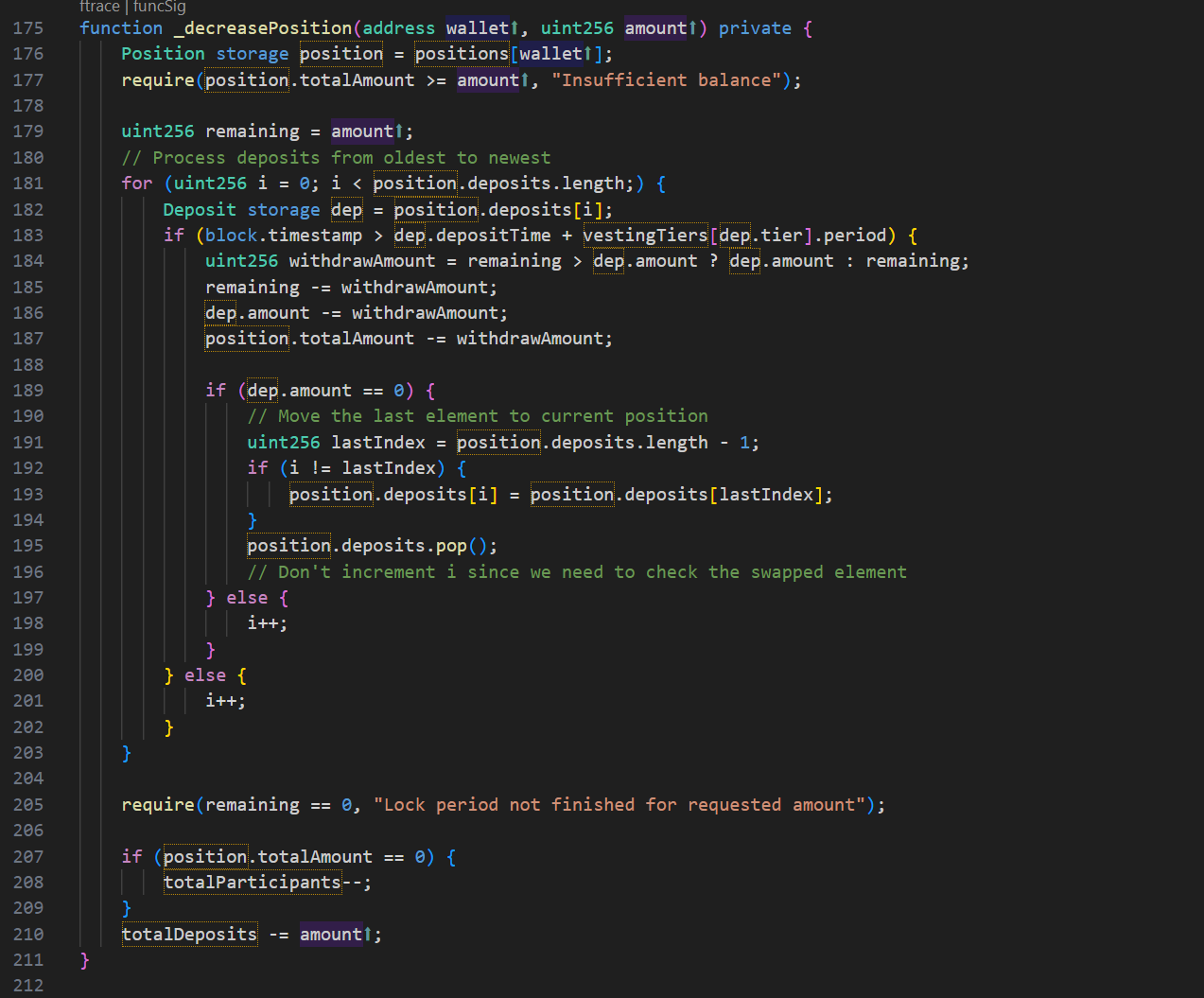
In updatePosition, since vaultExtension is not set, it goes directly to _decreasePosition function. In _decreasePosition function, only the position reduction operation of withdrawal amount is performed. Therefore, the vulnerability appears here. When the user's deposit expires, any amount of deposit can be withdrawn, and the rewards of all expired deposits will be withdrawn at the same time. However, since there is no judgment on whether the reward has been withdrawn, the reward will be withdrawn repeatedly.
Summarize
The cause of this vulnerability is that the Sorra project did not determine whether the user had already withdrawn the reward when the user withdrew, which allowed the user to repeatedly withdraw the reward through a large number of operations. The attacker used the above vulnerability to initiate multiple transactions and withdraw all the SOR Tokens in the Sorra project. It is recommended that the project party should verify multiple parties when designing the code operation logic, and try to select multiple audit companies for cross-audit when auditing the contract before it goes online.












