
Background
On November 18, 2024, we detected an attack on BNB Smart Chain. The project attacked was BTB . The attack transaction was
https://bscscan.com/tx/0xfb6df4053c2f1000cb03135064af19a79a87cf25efe612ae5f3468390d6be216
The attack caused a total loss of approximately USD 5,000.
Attack and incident analysis
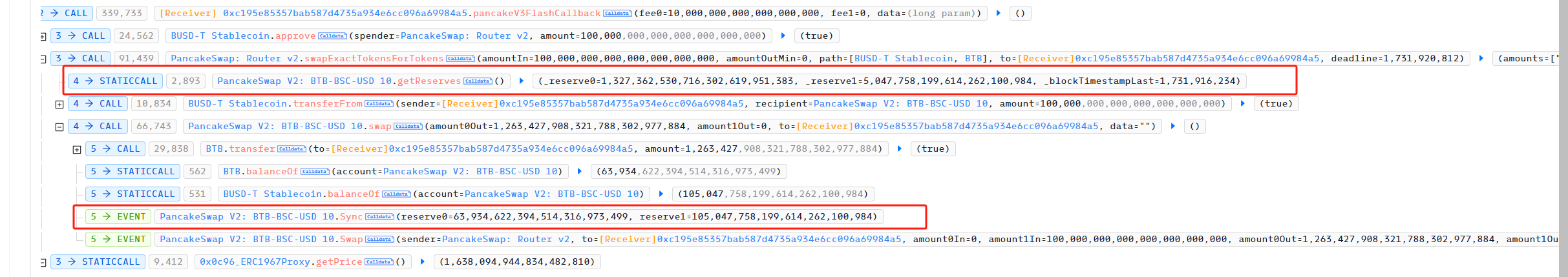
First, the attacker used flashloan to borrow 100,000 BUSD from pancakeSwapV3
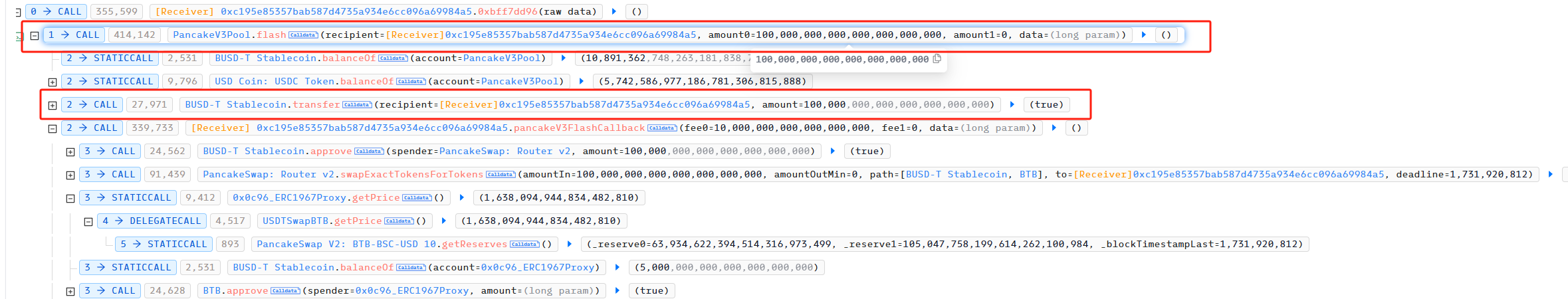
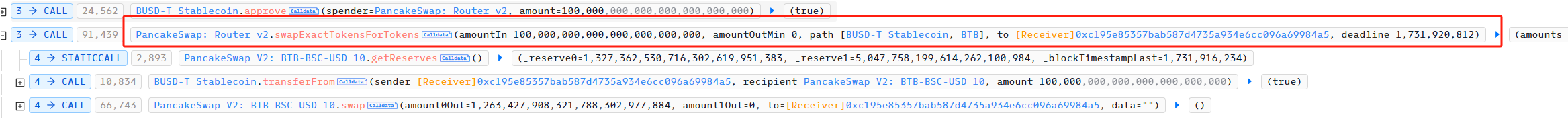
The attacker then used pancakeSwapV2 to convert the 100,000 BUSD loan into 1,263,427 BTB
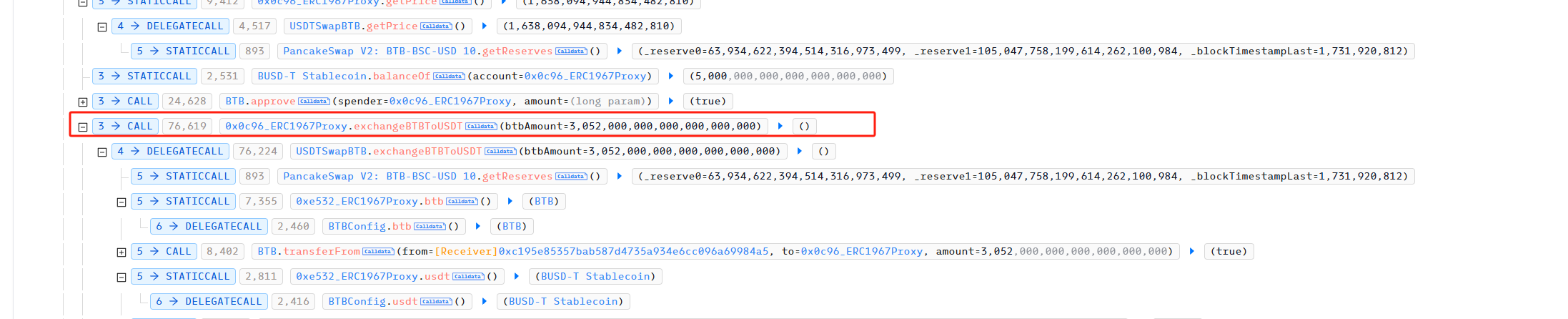
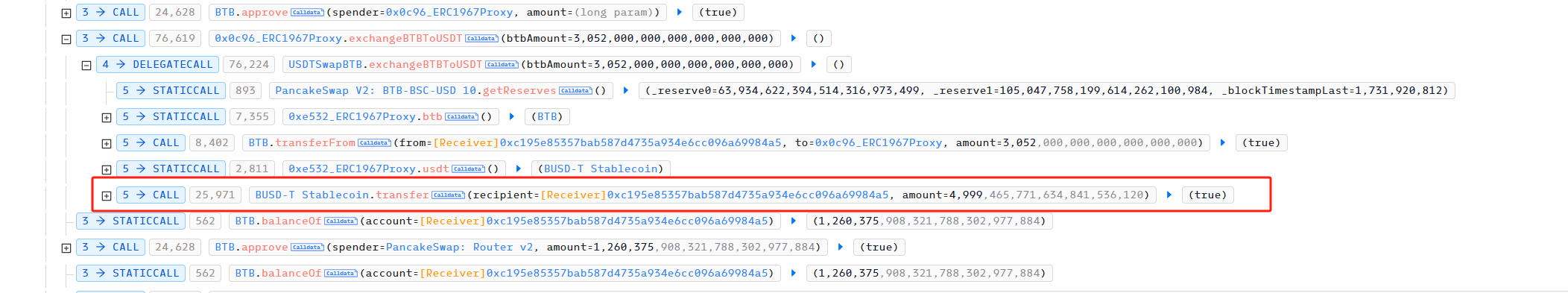
The attacker then used BTB’s exchange BTBToUSDT to convert 3,052 BTB into 4,999 BUSD.
Let’s take a look at the code of the exchangeBTBToUSDT function of the attacked smart contract.
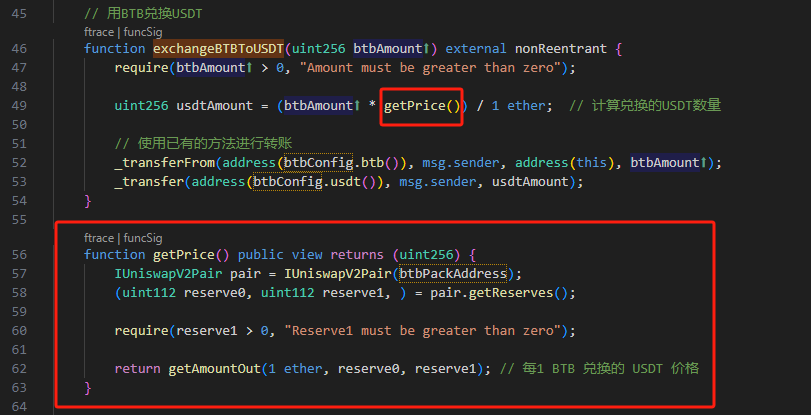
As you can see, the exchange price is determined by the reserve of the BTB and BUSD pair of pancakeSwapV2. In this way, the attacker can use pancakeSwap to exchange large amounts of BTB or BUSD to manipulate the price of BTB. We can see that the attacker exchanged BTB with 100,000 BUSD borrowed from flashloan.
Therefore, before the attacker uses pancakeSwapV2 to exchange large amounts of BUSD for BTB
reserve0 is:
1,327,362,530,716,302,619,951,383,
reserve1 is:
5047758199614262100984 ,
After redemption, reserve0 is:
63934622394514316973499 ,
reserve1 is:
105047758199614262100984 .
Through the implementation of getAmountOut in getPrice, we can calculate the change in BTB price before and after the attacker's exchange.
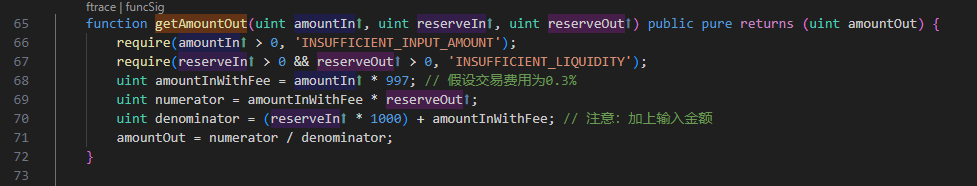
We calculated that the price of BTB increased from 1BTB=0.00379143964708692 BUSD to 1 BTB=1.6381204893766859 BUSD, which is more than 400 times higher.
Therefore, the attacker used 3052 BTB to exchange for 4999 BUSD.
Finally, the attacker used the remaining 1,260,375 BTB to redeem 99,964 BUSD from pancakeSwapV2.
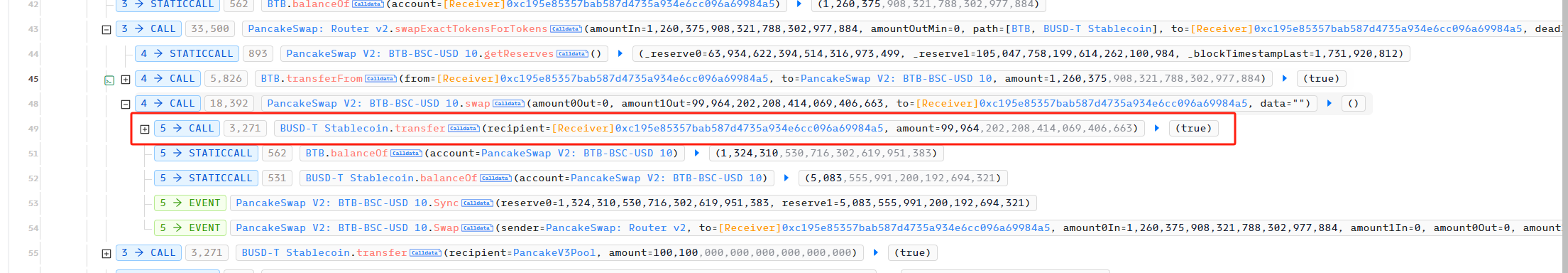
After the attacker repaid the flashloan loan and interest of 100,100 BUSD, he made a profit of 4,863 BUSD.
Summarize
The cause of this vulnerability is that the project party used an outdated price oracle when completing the exchange of BTB to BUSD, which allowed the attacker to easily manipulate the price of BTB, first buy a large amount of BTB, and then sell it after driving up the price of BTB. Finally, arbitrage was completed. It is recommended that the project party should conduct multi-party verification when designing the price oracle and code operation logic, and try to select multiple audit companies for cross-audit when auditing the contract before it goes online.














