Author: Certik
Since June 2024, the CertiK security team has monitored a large number of similar phishing/drainer transactions. The amount involved in June alone exceeded 55 million US dollars. After entering August and September, the activities of related phishing addresses have become more frequent, and phishing attacks have intensified. Throughout the third quarter of 2024, phishing attacks have become the means of attack that caused the most economic losses. Phishing attackers have obtained more than 243 million US dollars in 65 attacks. According to the analysis of the CertiK security team, the recent frequent outbreaks of phishing attacks are very likely related to the notorious phishing tool team Inferno Drainer. The team had announced its "retirement" in a high-profile manner at the end of 2023, but now seems to be active again and has made a comeback, creating a series of large-scale attacks.
Based on this background, this article will analyze the typical methods of phishing attack gangs such as Inferno Drainer and Nova Drainer, and list their behavioral characteristics in detail. It is hoped that these analyses will help users improve their ability to identify and prevent phishing scams.
What is Scam-as-a-Service
Many people may be familiar with the concept of Software-as-a-Service (SaaS). In the crypto world, SaaS has another meaning. Phishing teams have invented a new malicious model called Scam-as-a-Service. This model packages fraud tools and services and provides them to other criminals in a commercialized way. The infamous Inferno Drainer is a typical representative in this field. From November 2022 to November 2023, when they first announced the closure of their services, their fraud amount exceeded 80 million US dollars. Inferno Drainer provides buyers with ready-made phishing tools and infrastructure, including the front and back ends of phishing websites, smart contracts, and social media accounts, to help them quickly launch attacks. Phishers who purchase SaaS services keep most of the stolen money, and Inferno Drainer charges a commission of 10%-20%. This model greatly reduces the technical threshold for fraud. This makes cybercrime more efficient and scalable, leading to the proliferation of phishing attacks in the crypto industry, especially those users who lack security awareness are more likely to become targets of attacks.
How does Scam-as-a-Service work?
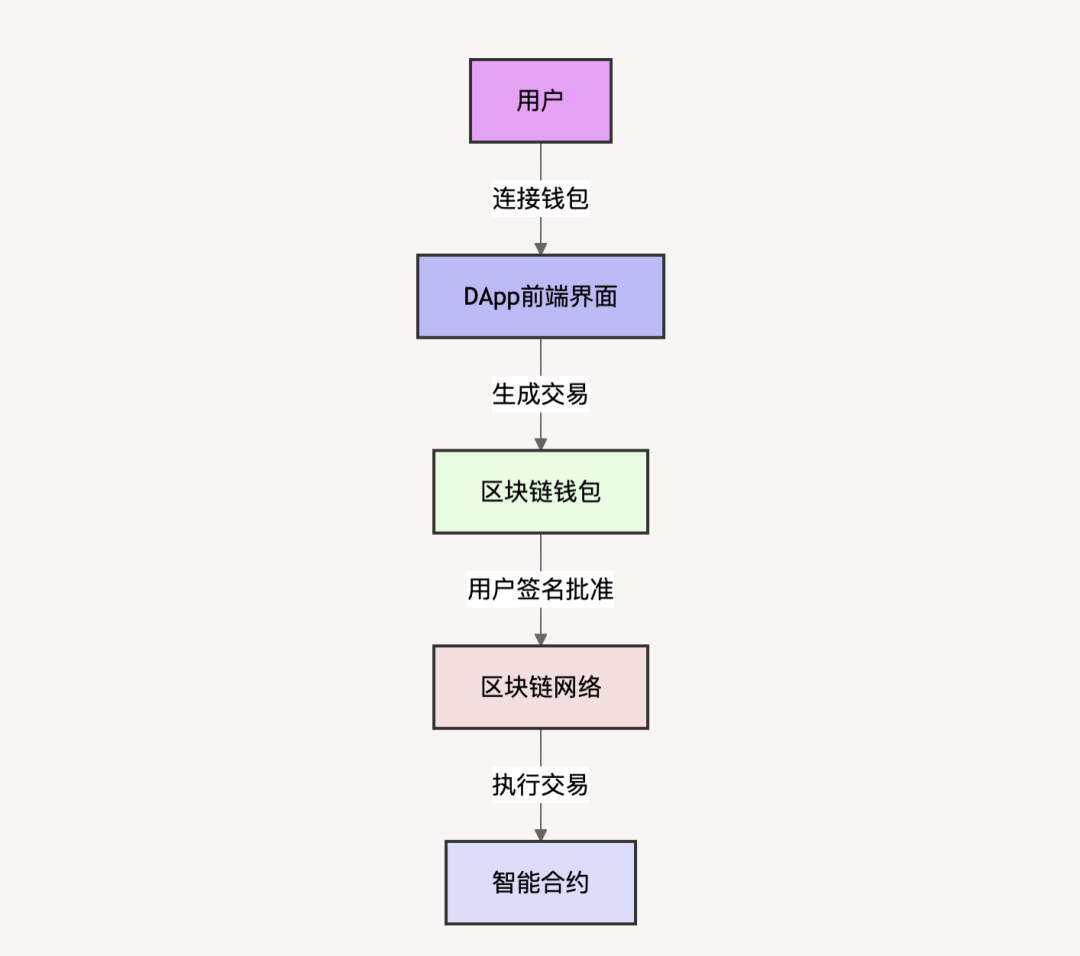
Before introducing SaaS, let's first take a look at the workflow of a typical decentralized application (DApp). As shown in the figure below, a typical DApp usually consists of a front-end interface (such as a web page or mobile application) and a smart contract on the blockchain. The user connects to the front-end interface of the DApp through a blockchain wallet, and the front-end page generates the corresponding blockchain transaction and sends it to the user's wallet. The user then uses the blockchain wallet to sign and approve the transaction. After the signature is completed, the transaction is sent to the blockchain network and the corresponding smart contract is called to execute the required function.
So, how do phishing attackers defraud users of their funds? The answer lies in the fact that they cleverly trick users into performing unsafe operations by designing malicious front-end interfaces and smart contracts. Attackers usually guide users to click on malicious links or buttons, thereby deceiving them into approving some hidden malicious transactions, or even in some cases, directly tricking users into revealing their private keys. Once users sign these malicious transactions or expose their private keys, attackers can easily transfer users' assets to their own accounts.
Here are some of the most common ones:
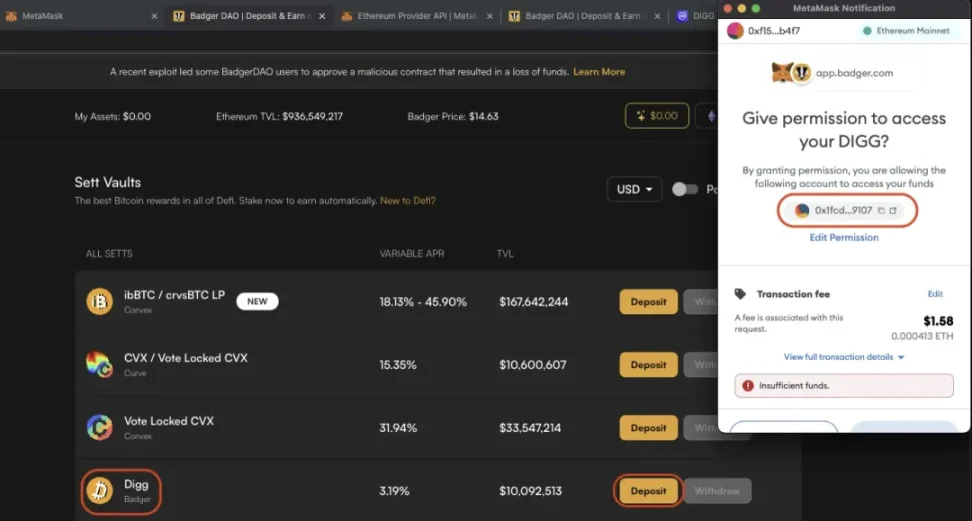
1. Forging the front end of a well-known project: The attacker carefully imitates the official website of a well-known project to create a seemingly legitimate front-end interface, making users mistakenly believe that they are interacting with a trusted project, thereby relaxing their vigilance, connecting their wallets and performing unsafe operations. As shown in Figure 1, the phishing gang forged its own page to be the front-end page of bagerDAO. Once the user approves the transaction on the page, their tokens will be authorized to the attacker's address.
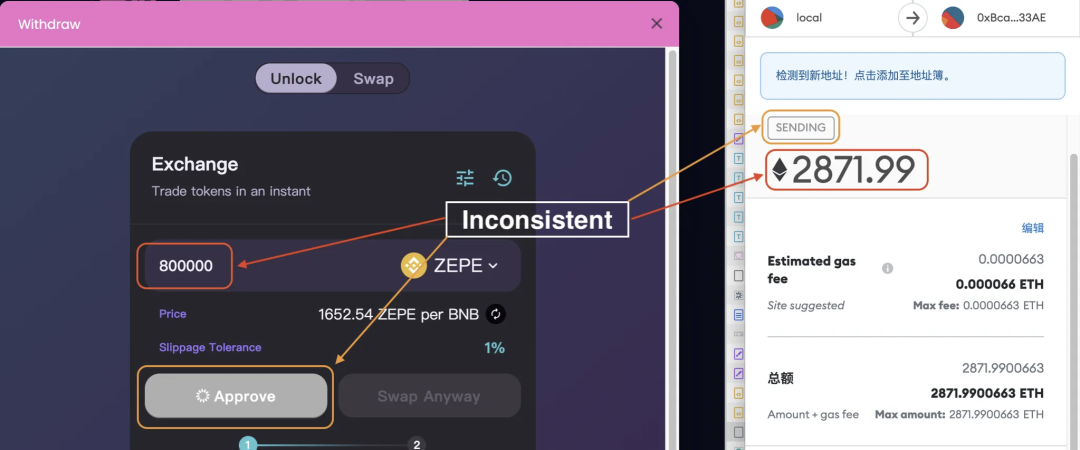
2. Token airdrop scam: They promote phishing websites on social media such as Twitter, Discord, and Telegram, claiming that there are very attractive opportunities such as "free airdrops", "early pre-sales", and "free minting of NFTs", thereby luring victims to click on links. After being attracted to the phishing website, victims often unconsciously connect their wallets and approve malicious transactions. As shown in Figure 2, the attacker airdropped a token called "ZEPE" to the user, deceiving the user to go to its phishing page for redemption. Once the user clicks, all ETH in his account will be sent to the scammer's address.
3. Fake hacking incidents and bounty scams: Cybercriminals claim that a well-known project has suffered a hacker attack or asset freeze and is now paying compensation or rewards to users. They use these fake emergencies to attract users to phishing websites, trick them into connecting their wallets, and ultimately steal their funds.
It can be said that phishing scams are not new and were already very common before 2020, but the SaaS model is largely the biggest driver of the intensification of phishing scams in the past two years. Before the emergence of SaaS, phishing attackers needed to prepare on-chain startup funds, create front-end websites and smart contracts for each attack. Although most of these phishing websites are crudely made, they can recreate new scam projects by using a set of templates and making simple modifications, but the operation and maintenance of the website and page design still require a certain technical threshold. SaaS tool providers such as Inferno Drainer completely eliminate the technical threshold of phishing scams, provide buyers who lack the corresponding technology with the service of creating and hosting phishing websites, and extract profits from the proceeds of the scam.
How do Inferno Drainer and SaaS buyers share the spoils?
On May 21, 2024, Inferno Drainer published a signature verification message on etherscan, announcing his return and creating a new Discord channel.
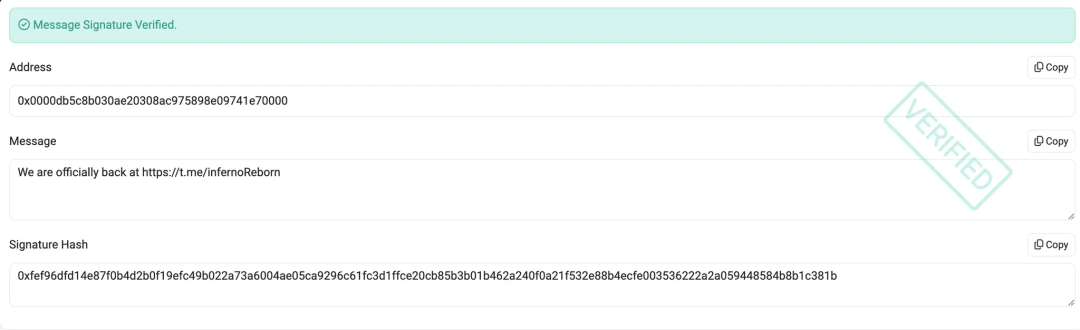
0x0000db5c8b030ae20308ac975898e09741e70000 is one of the phishing addresses with abnormal behavior that CertiK has recently monitored. We found that this address has conducted a large number of transactions with similar patterns. After analyzing and investigating the transactions, we believe that this type of transaction is the transaction in which Inferno Drainer transfers funds and divides the spoils after detecting that the victim has been hooked. Let's take one of the transactions conducted by this address as an example:
https://etherscan.io/tx/0x5cd1eeee1b091888e7b19bc25c99a44a08e80112fdc7a60a88b11ed592483a5f
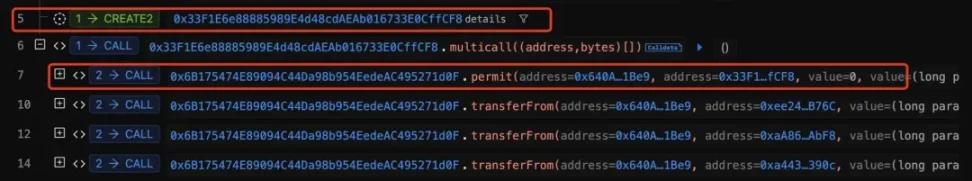
The attacker transfers the victim's tokens via Permit2
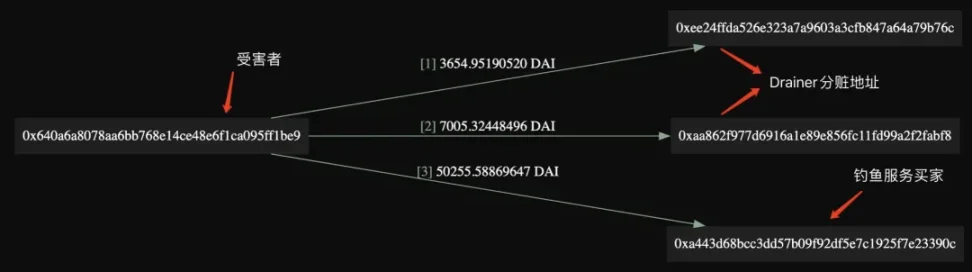
1. Inferno Drainer creates a contract through CREATE2. CREATE2 is an instruction in the Ethereum virtual machine that is used to create smart contracts. Compared with the traditional CREATE instruction, the CREATE2 instruction allows the address of the contract to be calculated in advance based on the smart contract bytecode and a fixed salt. Inferno Drainer takes advantage of the nature of the CREATE2 instruction to pre-calculate the address of the spoils-sharing contract for the buyer of the phishing service in advance, and then creates the spoils-sharing contract after the victim is hooked, completing the token transfer and spoils-sharing operation.
2. Call the created contract to approve the victim's DAI to the phishing address (the buyer of the Inferno Drainer service) and the stolen money distribution address. The attacker used the various phishing methods mentioned above to guide the victim to inadvertently sign the malicious Permit2 message. Permit2 allows users to authorize the transfer of tokens through signatures without directly interacting with the wallet. As a result, the victims mistakenly believed that they were just participating in regular transactions or authorizing some harmless operations, but in fact they unknowingly authorized their DAI tokens to the addresses controlled by the attacker.
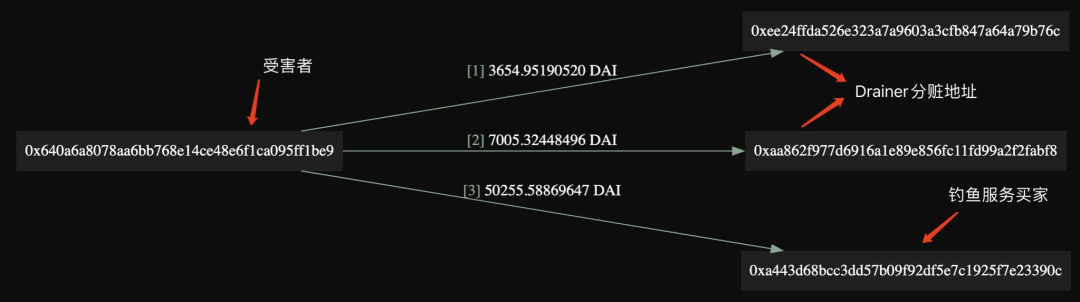
3. Transfer 3,654 and 7,005 DAI to the two addresses for sharing the spoils, and transfer 50,255 DAI to the buyer to complete the sharing of the spoils.
It is worth mentioning that many blockchain wallets currently have anti-phishing or similar functions, but the anti-phishing function of many wallets is implemented through domain name or blockchain address blacklist. Inferno Drainer can bypass these anti-phishing functions to a certain extent by creating a contract before dividing the loot, further reducing the victim's vigilance. Because when the victim approves the malicious transaction, the contract has not even been created, and there is no way to analyze and investigate the address. In this transaction, the buyer of the phishing service took 82.5% of the stolen money, and Inferno Drainer retained 17.5%.
Revealed: How many steps are needed to create a phishing website?
Now that we have seen how Inferno Drainer divides the spoils, let’s take a look at how easy it is for attackers to create a phishing website with the help of SaaS.
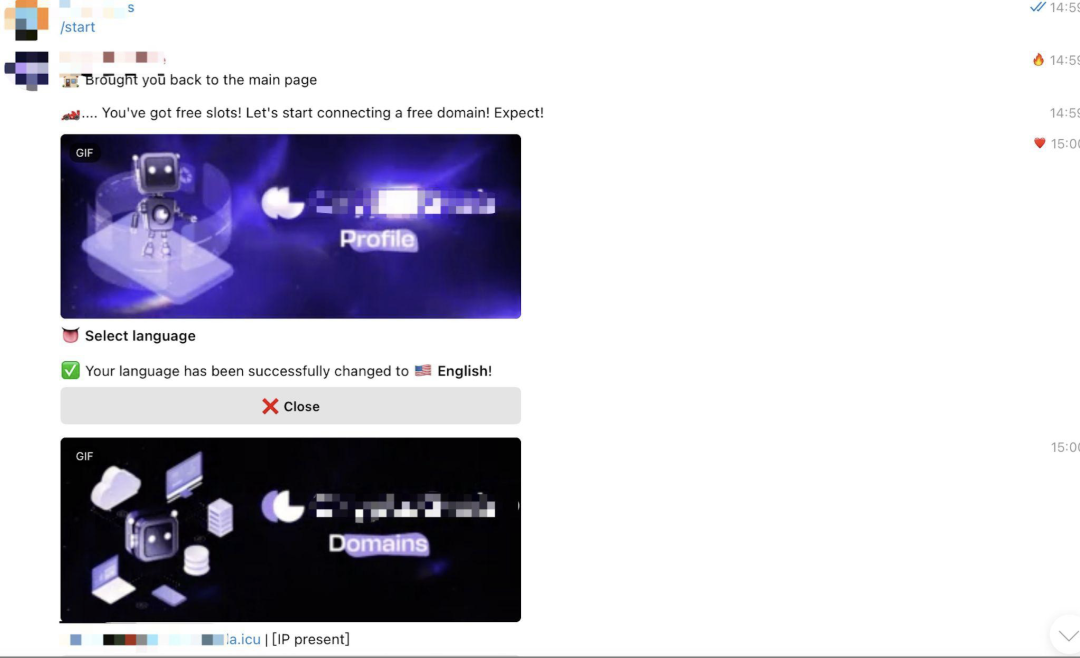
The first step is to enter the TG channel provided by Drainer. With just a simple command, a free domain name and the corresponding IP address will be created.
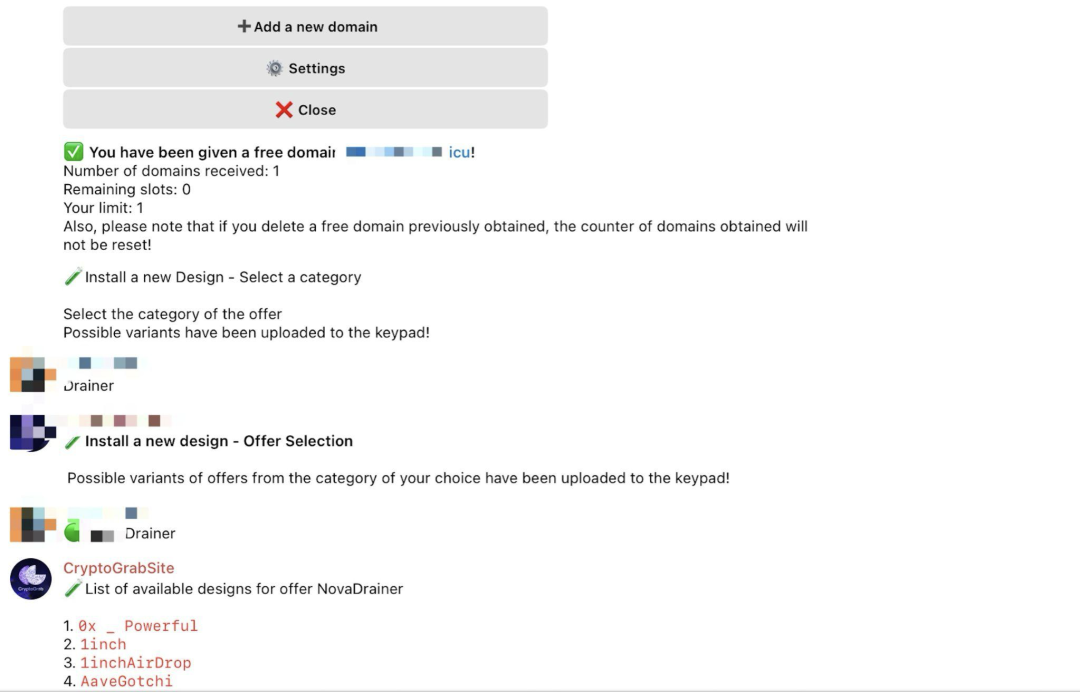
The second step is to select any one from the hundreds of templates provided by the robot, and then enter the installation process. After a few minutes, a phishing website with a decent interface will be created.
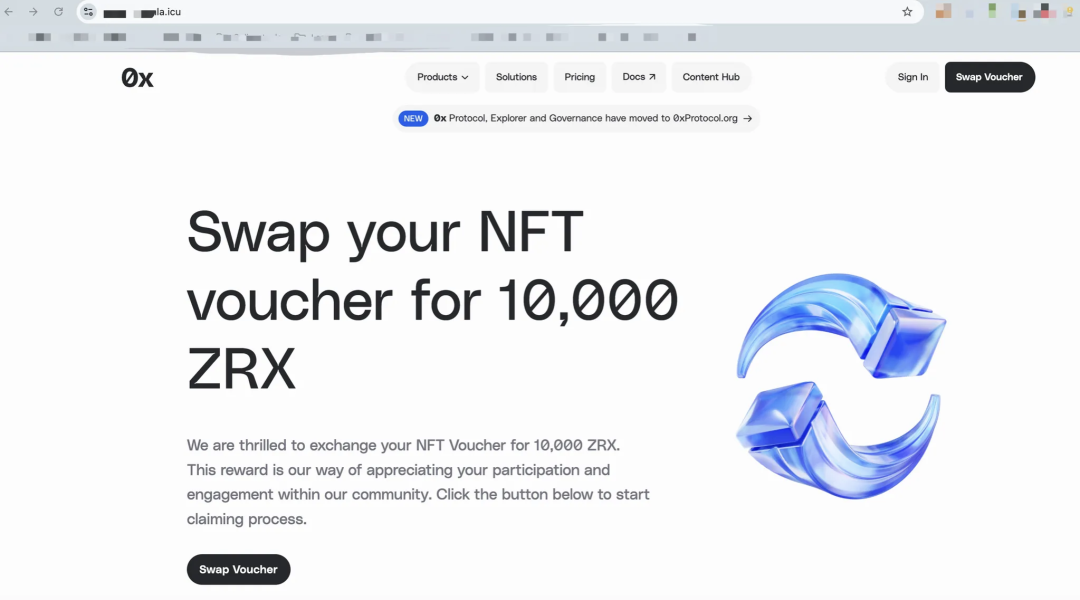
The third step is to find victims. Once a victim enters the website, believes the fraudulent information on the page, and connects to the wallet to approve the malicious transaction, the victim's assets will be transferred. With the help of SaaS, the attacker only needs three steps to create such a phishing website, which takes only a few minutes.
Summary and inspiration
As one of the most threatening "Drainers" in the cryptocurrency world, the return of Inferno Drainer undoubtedly brings huge security risks to industry users. With its powerful functions, hidden attack methods, and extremely low crime costs, Inferno Drainer has become one of the preferred tools for cybercriminals to carry out phishing attacks and fund theft.
When users participate in cryptocurrency transactions, they need to be vigilant at all times and keep the following points in mind:
- There is no free lunch in the world: Don’t believe any “pie in the sky” propaganda, such as suspicious free airdrops, compensation, and only trust official websites or projects that have received professional audit services.
- Always check network links: Before connecting your wallet to any website, carefully check the URL to see if it imitates a well-known project, and try to use the WHOIS domain name query tool to check its registration time. Websites with too short a registration time are likely to be fraudulent projects.
- Protect privacy information: Do not submit your mnemonic phrase or private key to any suspicious website or app. Before the wallet asks you to sign any message or approve a transaction, carefully check whether the transaction is a Permit or Approve transaction that may result in fund loss.
- Pay attention to scam updates: Follow CertiK Alert and other official social media accounts that regularly release warning information. If you find that you have accidentally authorized tokens to a scam address, withdraw the authorization in time or transfer the remaining assets to other safe addresses.













