Background
On November 25, 2024, we detected an attack on BNB Smart Chain, the project being attacked was DCF . The attack transaction was
https://bscscan.com/tx/0xb375932951c271606360b6bf4287d080c5601f4f59452b0484ea6c856defd6fd
The attack caused a total loss of approximately USD 440,000.
Attack and incident analysis
First, the attacker borrowed a large amount of BUSD from a series of PancakeSwapV3 Pools using flashloan.
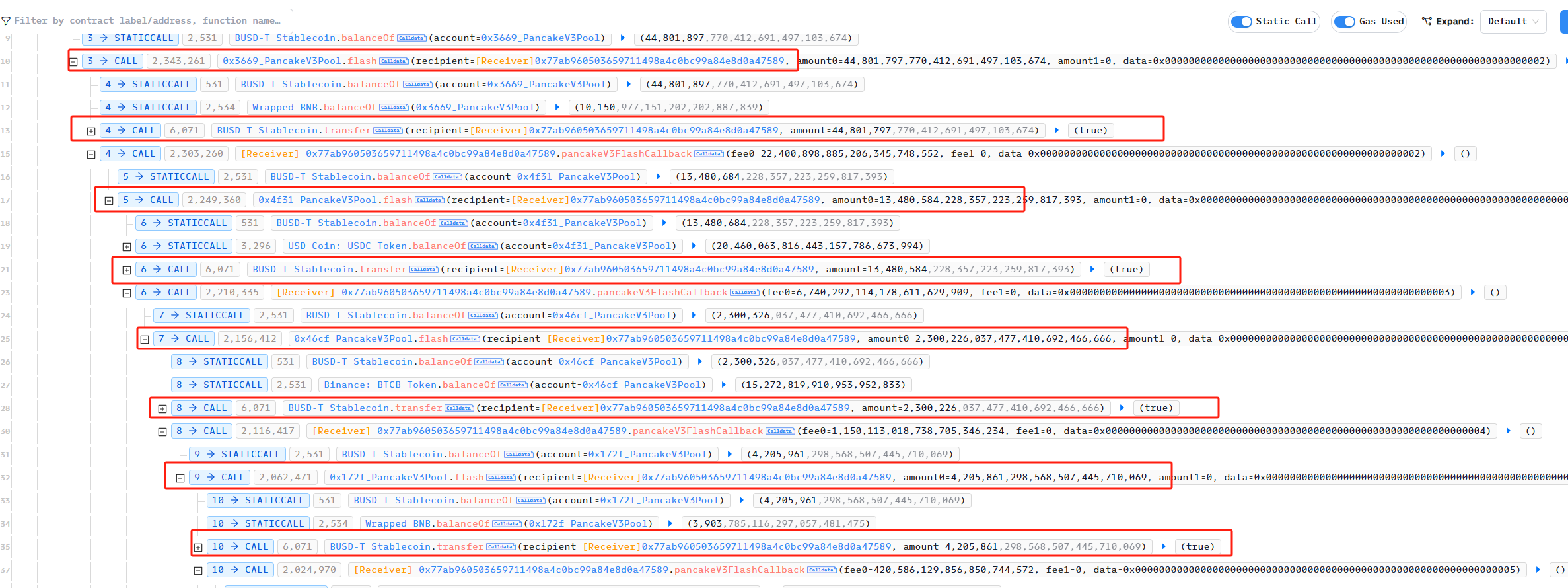
Subsequently, the attacker used PancakeSwap’s swap function to first transfer the exchanged tokens and then pay the tokens in the callback function. Through a series of recursive swaps, he obtained a large amount of BUSD.
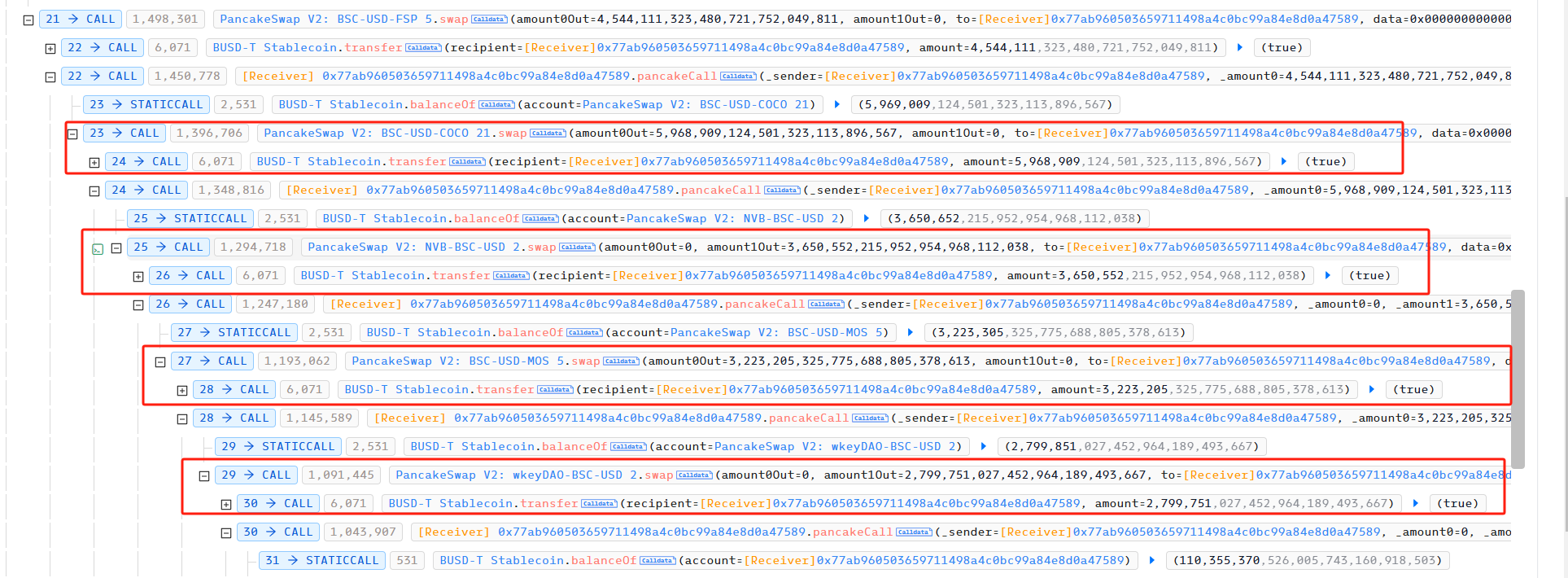
Then, after the attacker obtained the principal used to carry out the attack, he began to attack the DCF project.
first step:
The attacker transfers all DCF he holds to the attack contract.
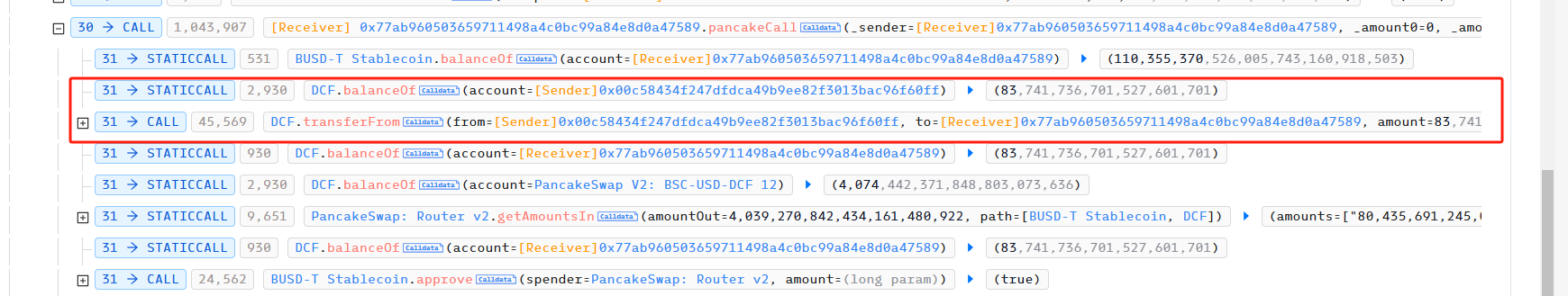
Step 2:
The attacker used 80,435,691 BUSD to exchange 4,039 DCF to 0x16600100b04d17451a03575436b4090f6ff8f404.
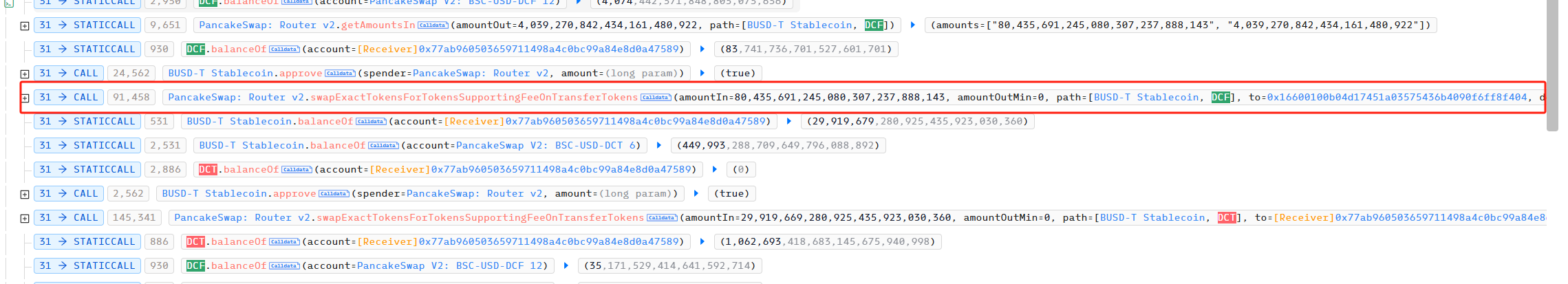
Step 3:
The attacker used the remaining 29,919,679 BUSD to exchange 1,062,693 DCT for the attack contract.
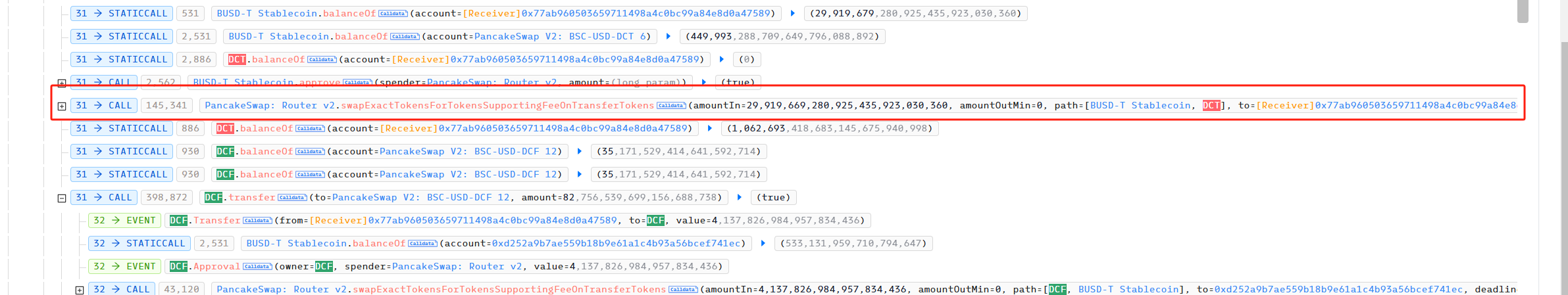
Step 4:
The attacker used transfer to transfer 82 DCF to PancakeSwap Pair BUSD-DCF. Let’s take a look at the specific implementation of DCF transfer.
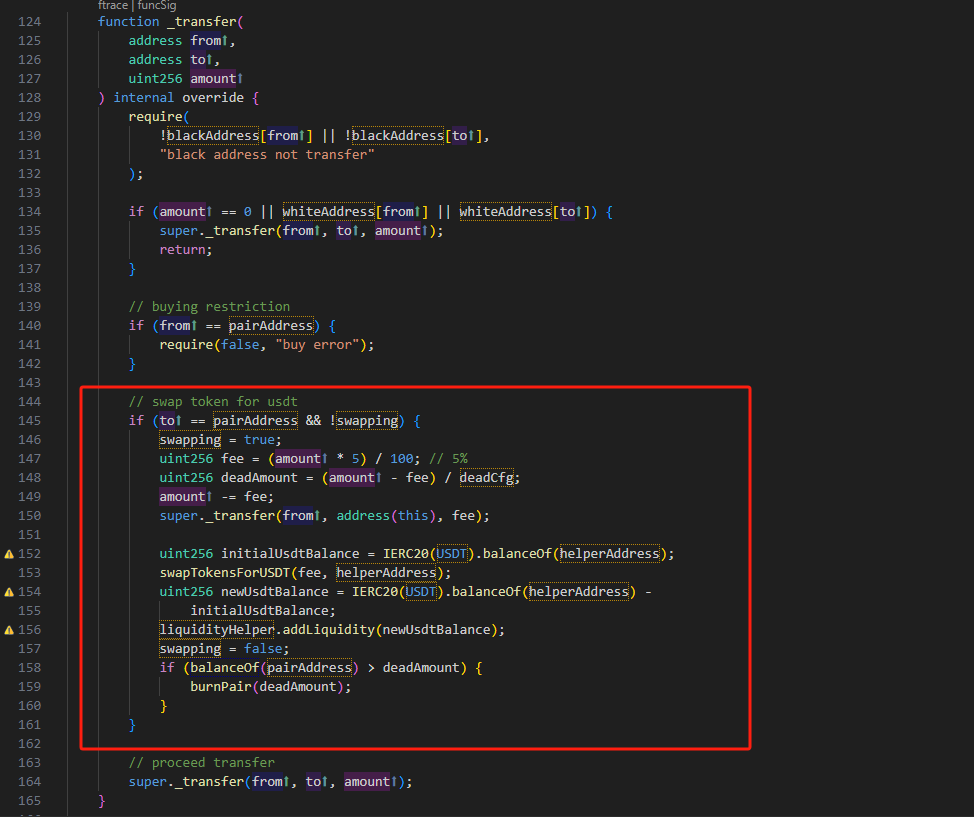
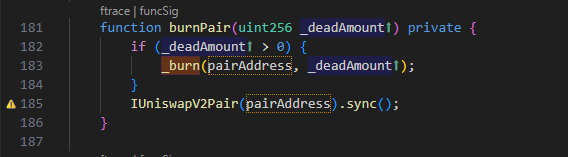
It can be seen that when to is the address of PancakeSwap Pair, the code in the red box is executed, and the vulnerability appears here. Since deadcfg is 2, the code will destroy about half of the DCF of the transfer amount from PancakeSwap Pair, and then sync. This operation will cause the number of DCF in PancakeSwap Pair BUSD-DCF to decrease significantly, and the price of DCF to rise sharply. Through this operation, the price of DCF increased from 171 BUSD to 1,708,540,682,977,674 BUSD, an increase of 9,991,465,982,325 times. Since the code liquidHepler.addLiquidity in the transfer function of DCF consumes part of the DCT in PancakeSwap Pair BUSDDCT, it also increases the price of DCT.
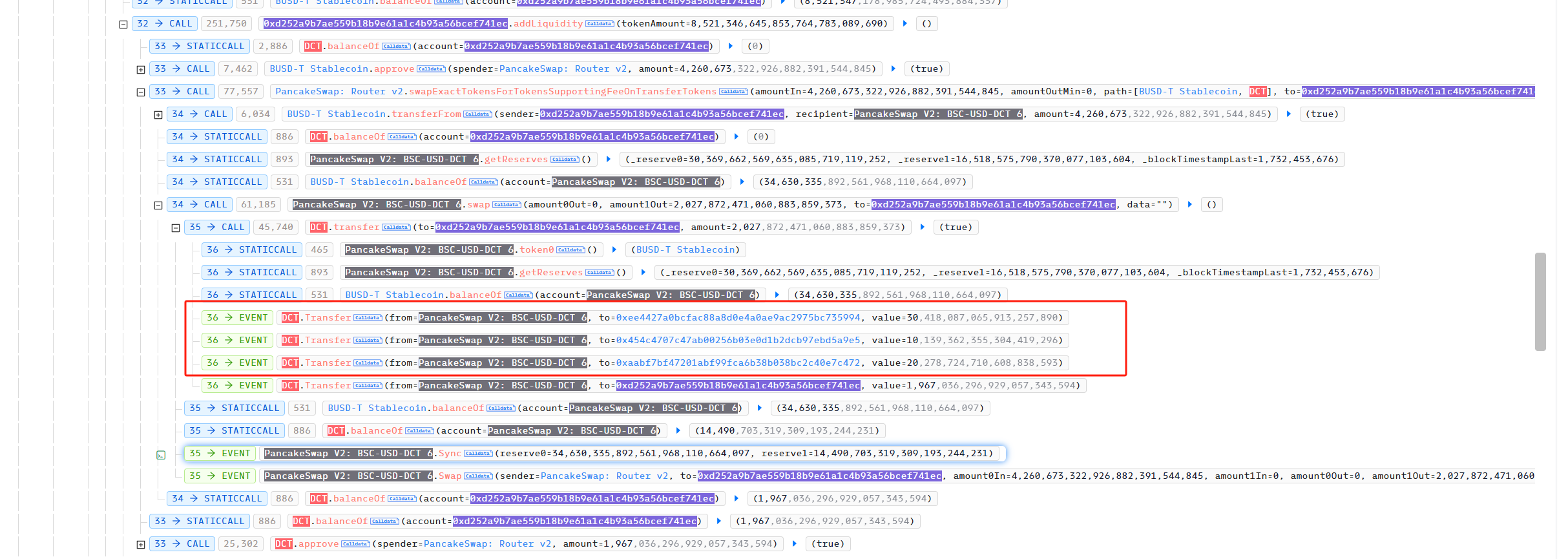
Finally, the attacker used the remaining DCF to empty the 72,612,978 BUSD in the PancakeSwap Pair BUSD-DCF. Since the above operation also raised the price of DCT, the value of DCT that the attacker previously exchanged with 29,919,679 BUSD became 38,302,987 BUSD. Finally, after the attacker returned the BUSD borrowed in the flashloan, he made a profit of 442,028 BUSD.
Summarize
The cause of this vulnerability is that the project side wrote incorrect logic when implementing the DCF transfer function. As a result, the attacker destroyed the DCF in the pair after transferring it to the swap pair, which made it easy to manipulate the price of DCF. Finally, arbitrage was completed. It is recommended that the project side try to select multiple audit companies for cross-audit when auditing the contract before it goes online.














