Hash (SHA1): 540b80ff028998e26a6e5b85396bb02c467d4dbb1d4d5ddfc8bb94b26f57f8ce
No.: PandaLY Security Analysis No.006
On November 16, dexx had a security incident. So far, the official has not announced the specific amount of money stolen. The types of stolen tokens include but are not limited to SOL, ETH and various Memes. In order to help the users who lost their tokens to protect their rights, we have integrated and analyzed the relevant data.
Hacker theft techniques
Theft Principle:
The culprit for the theft of DEXX assets is "private key leakage". DEXX initially claimed that it was a "non-custodial wallet", but in fact, they themselves own all the private keys of the user group, and when transmitting private key data, they choose to transmit in plain text, which means that after hackers intercept the data related to the private key, they can directly obtain your private key and do evil without decryption.
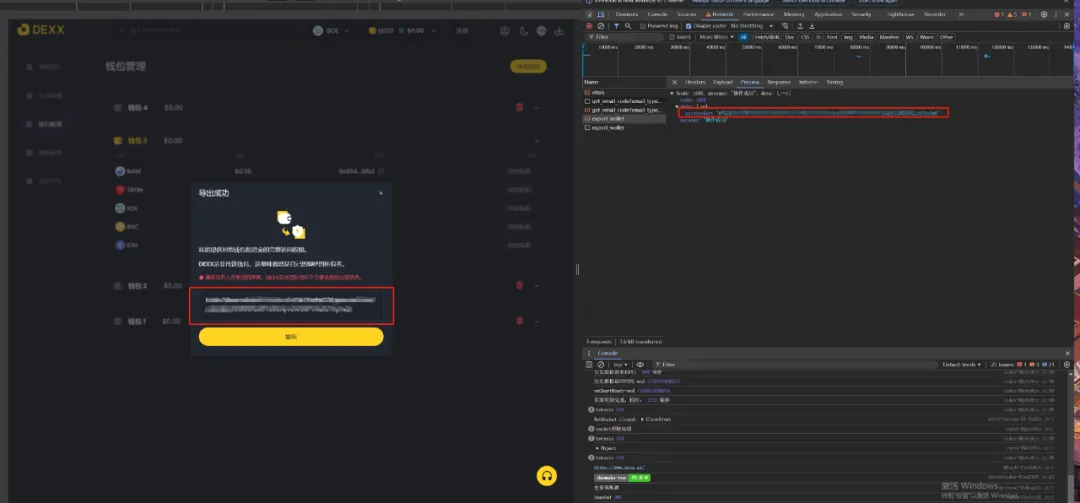
Although DEXX has not disclosed the hacker's theft method, one thing that is clear is that DEXX does not put the private keys in the hands of users, but controls all the private keys of the wallet itself, that is, the wallet private keys are stored in the database of the DEXX server.
Therefore, there are many possible methods for hackers to commit crimes. One is to break into the DEXX server to obtain the private key in the database, and the other is to monitor the private key in the information exchange between users and DEXX. Finally, the possibility of official internal crimes cannot be ruled out.
Transfer method:
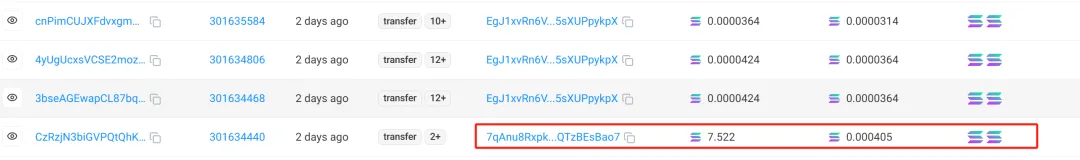
According to our analysis of the on-chain data, the on-chain data has the characteristics of multi-threaded currency transfers, and the addresses currently viewed have the behavior of transferring money in descending order of value. Therefore, we speculate that the hacker controls the private key through a multi-threaded script, and transfers tokens in descending order after conversion based on the victim’s specified token balance.
There are several ways to transfer:
The first one is to distribute GAS + transfer tokens:
As shown in the figure below, first, the hacker generated a batch of new addresses and transferred 0.2 SOL of GAS to each new address. Then, the tokens were transferred to the distributed new addresses.
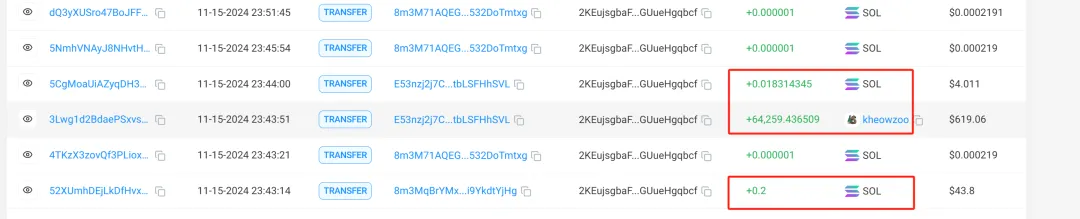
The second method is to directly transfer tokens and SOL:
The hacker generates a batch of new addresses, first transfers out the tokens from the victim's address, and then transfers out the SOL from the victim's address without distributing GAS.
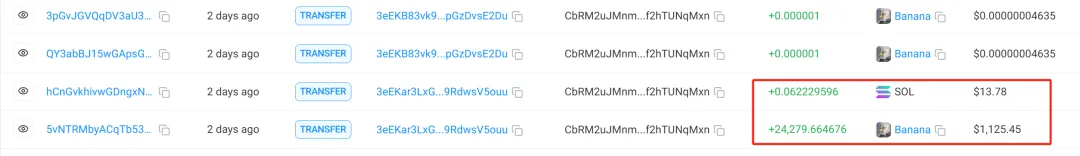
The third method is to transfer only SOL:
The hacker generates a batch of new addresses and only transfers the SOL of the victim's address.
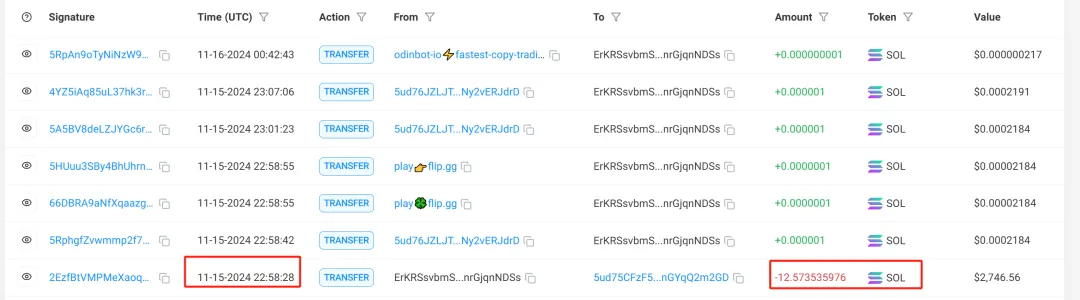
Distribute 0.2SOL
What is more interesting is that the hacker address 8m3MqBrYMxrQGv6QnxiTFDTYzz5gpfEAHki9YkdtYjHg, after transferring the victim's tokens, transferred 0.2SOL to each victim, and then transferred it to a new address. As shown in the figure below, the scammer first transferred the victim's wallet SOL address. After 3 hours, the scammer deposited 0.2SOL into the victim's wallet and transferred it to the new address of the stolen wallet after 5 seconds.
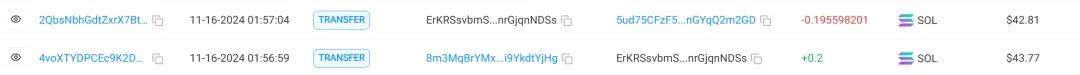
It was found that most transfers in and out took about 5 seconds, and a small number of transfers in and out took about 1 hour.
We speculate that the reason for this operation is to ensure that the stolen wallet has enough GAS to transfer the money out.
track
So far, the hacker's wallet has not been collected. The assets are all in new addresses. We tracked the address where the hacker distributed GAS.
We found that the source of SOL funds for hackers to distribute GAS all came from the victim's address.
Among them, the red address on the far right is the hacker's address, the blue address is the victim's address, and the yellow address is the hacker's address. The hacker has the following addresses except the top red address:
The victim addresses of HbPnGmn1cuBXWUnMzEk5vcCKTk2P6rrgankhaknsHETm all performed the above-mentioned operation of transferring 0.2SOL.
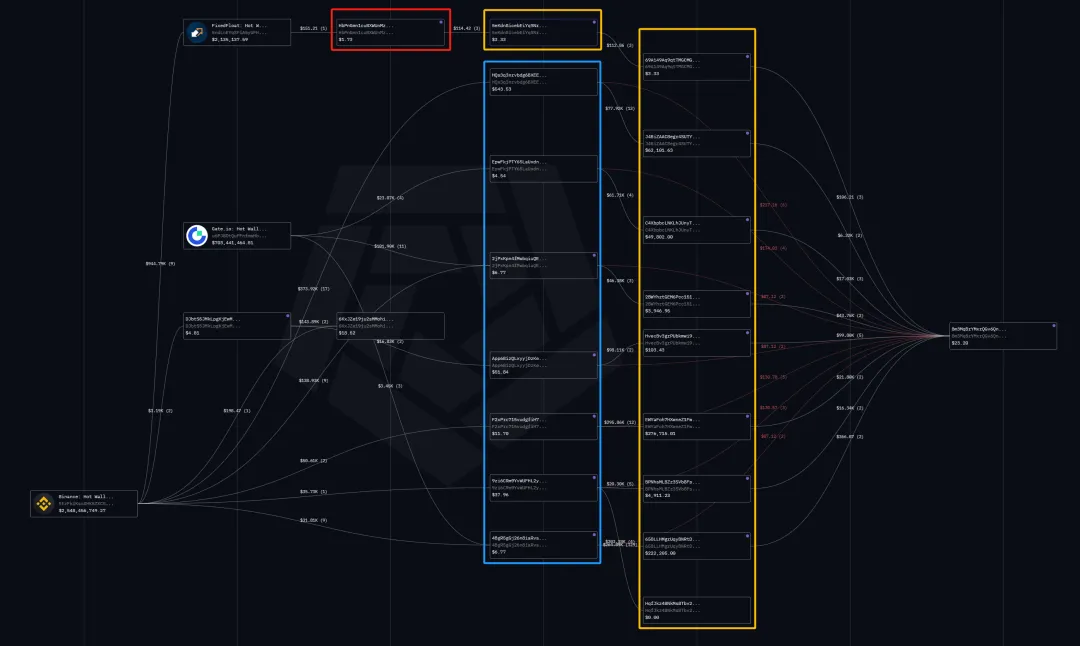
According to the on-chain data analysis, the top address was first put on the chain at 2024/11/13 21:51:20, and SOL came from FixedFloat. After the funds were received, SOLDOGE, USDT, and RAY were bought, among which USDT, RAY, and SOL were all transferred to the address distributed by the hacker. According to the on-chain behavior analysis, the address is most likely still a user address.
Retrieve
DEXX stated that some assets were isolated to a safe address. However, according to the on-chain data analysis, the isolation method is exactly the same as the hacker theft method, and users cannot determine whether their addresses are isolated or stolen.
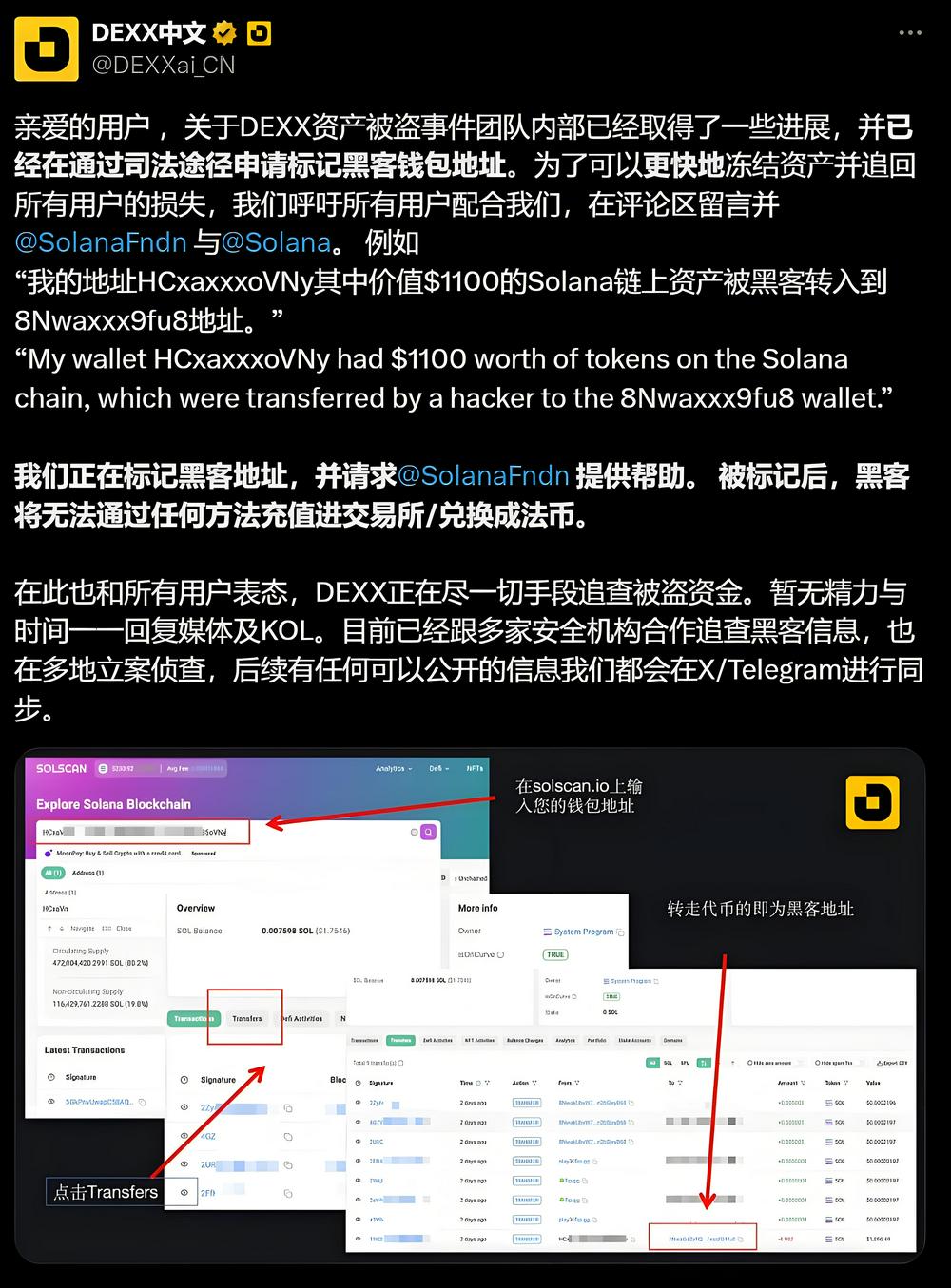
So far, DEXX has only issued a statement, claiming to cooperate with multiple security agencies, and published an English tweet hoping to negotiate with the hacker and hope that SolScan will help mark the hacker's address. However, there is a logical loophole in that DEXX has not used any method to collect the addresses of users' stolen assets, nor has it announced the stolen amounts and information. On the contrary, only security companies are constantly working hard to collect information and follow up on hacker addresses, and security companies have not officially issued a statement to cooperate with DEXX to retrieve the assets, but only help the community to organize information for public welfare purposes.
At present, the judicial department has not intervened in the DEXX incident. Only after the judicial department intervenes can the security company cooperate to provide detailed user stolen information, and the judicial department can use this as evidence to help users recover it.
Conclusion
Currently, there are many types of bots and websites. As long as the website obtains your private key, please do not put large amounts of funds in the wallet whose private key has been obtained.
Here is a strategy for you. Although it is a little troublesome, it is a simple and effective way to prevent theft.
Create a new wallet as a safe wallet, import the private key to the bot's wallet as a "dog-beating" wallet, and when you buy a large-capital meme to hold it for a long time or make a large-capital profit, transfer the meme or profit to the safe wallet. In this way, even if the "dog-beating" wallet is stolen, only a small amount of assets are lost, not all.
We will continue to follow up on the DEXX case. We have monitored the address where the form was submitted to us. Although we cannot guarantee a good outcome, we will do our best. If you are a victim and have not yet filled out the form, please click the following link, or follow the official account "链源安全" and click "Dexx Registration" on the main page to fill out the form.













