Author: Bitrace
A hardware wallet is a physical device designed for storing cryptocurrencies and is considered an important means of secure custody of crypto assets. Its built-in security chip stores private keys offline, ensuring that users have full control over their cryptocurrencies. Hardware wallets are usually operated offline, which further reduces the risk of being attacked by Internet hackers.
However, due to the general lack of understanding among investors, there are still a large number of fraud cases targeting novice users, resulting in the loss of their assets stored in hardware wallets. This article will introduce two common methods of stealing coins from hardware wallets - hardware wallet manual fraud and hardware wallet modification and disguise scam.
Hardware wallet manual fraud
The core of this type of money theft is to take advantage of ordinary investors' lack of understanding of how to use hardware wallets, and to mislead victims into transferring money to phishing addresses by replacing false instructions. The victim purchased the hardware wallet from a third-party e-commerce platform, opened the package, and opened the hardware wallet according to the "initial pin code" marked on the "instruction manual". After backing up the "mnemonic phrase" printed on the "instruction manual", he deposited a large amount of funds into the wallet address, which was eventually stolen.
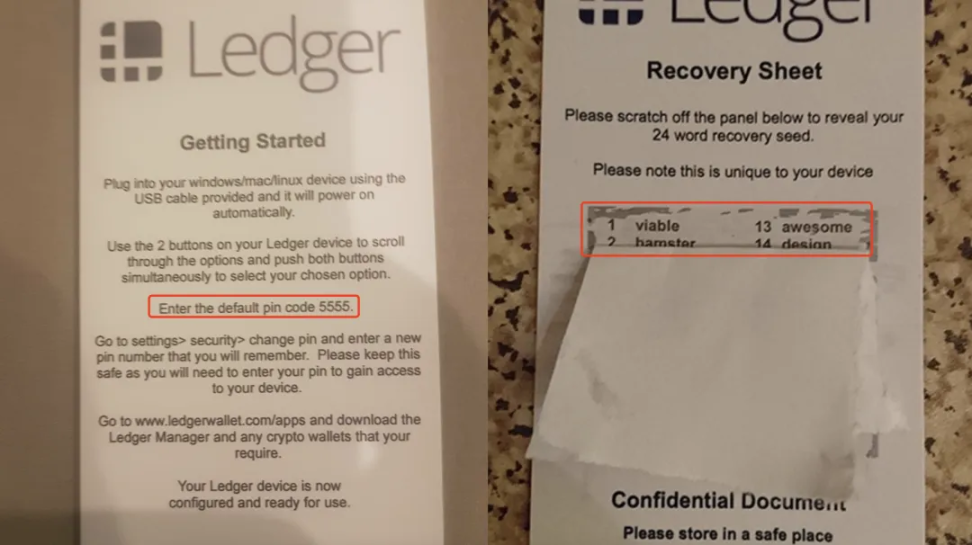
The reason is not that the wallet has been cracked at the hardware level, but that the thieves obtain the address mnemonics by pre-activating it, forging false instructions for secondary packaging, and then selling the activated hardware wallet to the victim through unofficial channels. Once the target object transfers encrypted assets to the address, it will enter the standard fake wallet theft process.
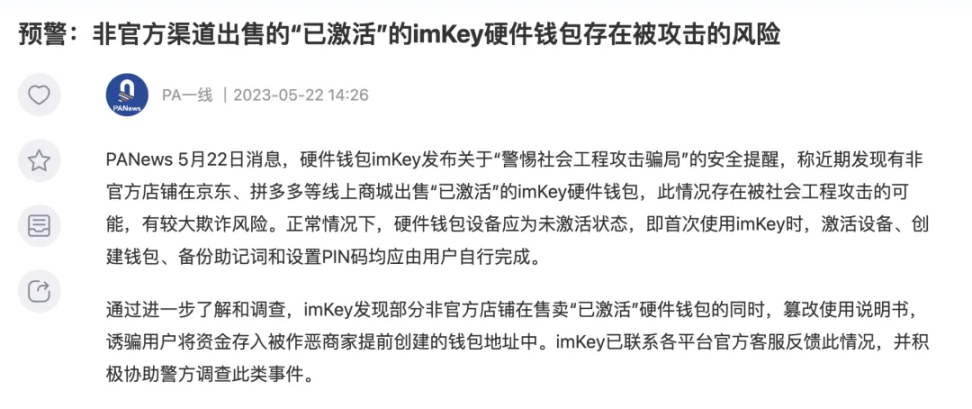
Similar risks also exist in the secondary market in Chinese-speaking regions. Imkey, a well-known hardware wallet manufacturer, once issued a warning that some unofficial stores tampered with the instruction manual while selling "activated" hardware wallets, tricking users into depositing funds into wallet addresses created in advance by malicious merchants. It can be seen that the importance of identifying official e-commerce stores is equivalent to identifying official websites.
Hardware wallet devices modified
A Ledger user received a package without placing an order, which contained a brand new Ledger X hardware wallet and an attached letter. The letter stated that due to the cyber attack on Ledger, user data was leaked, and new hardware wallet devices were sent to affected customers. The letter also asked users to replace their devices for safety.

However, the authenticity of the letter is questionable, and Ledger CEO Pascal Gauthier has made it clear that the company will not make any compensation for the accidental disclosure of personal data. The user also said that this is a scam, and he shared more pictures and opened the device to show the inside of the hardware wallet plastic box, which clearly showed signs of tampering.
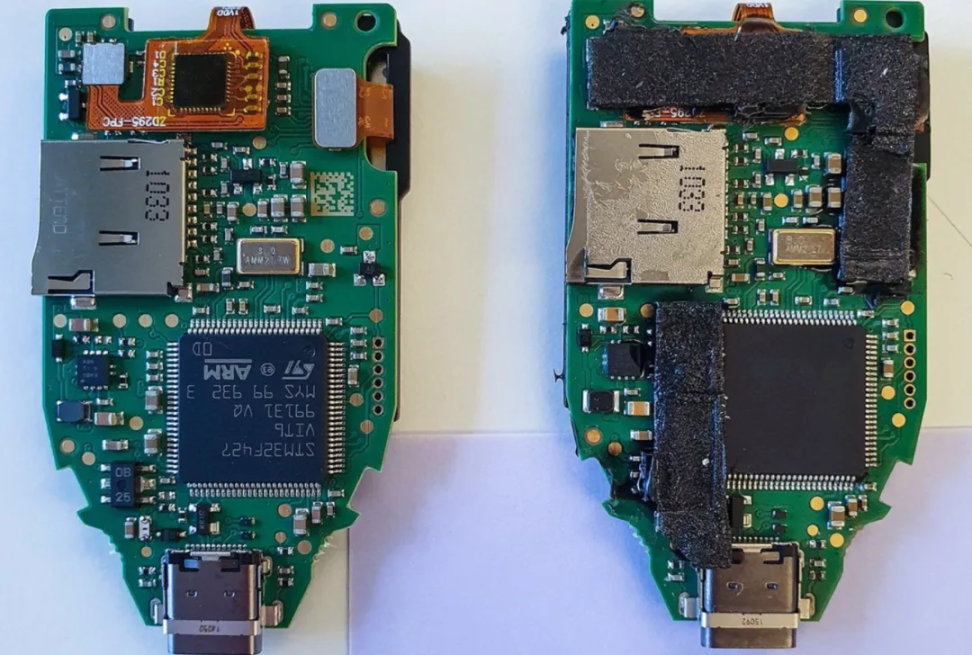
In addition, Kaspersky Security Team also reported a case of counterfeiting Trezor hardware wallet. The victim purchased a Trezor Model T from an unofficial channel, but the internal firmware of the device had been replaced by the attacker, who was able to gain access to the user's encrypted assets and steal the coins.
Last words
From the above cases, it is not difficult to see that supply chain attacks on hardware wallets have become very widespread, and ordinary investors and hardware wallet manufacturers should be vigilant. The correct use method will effectively avoid the risk of currency theft:
- Purchase hardware devices from official channels Any hardware wallet purchased from unofficial channels is not safe.
- Make sure the wallet is in an inactive state. Officially sold hardware devices must be in an inactive state. If investors find that the machine has been activated after turning it on, or even the manual prompts an "initial password" or "default address", please deactivate the device in time and provide feedback to the official hardware wallet.
- Ensure that the address is generated by the user. In addition to the device activation process, the user also needs to set the PIN code, generate the binding code, create the address and back it up. Any operation by a third party will bring financial risks to the user. Under normal circumstances, the hardware wallet device should be in an unactivated state, that is, when using the hardware wallet for the first time, the user should activate the device, create a wallet, back up the mnemonic and set the PIN code.














