Compiled by: SafePal
The "Dark Forest", a cosmic sociological law derived from "The Three-Body Problem", is also the most naked summary of the current Web3 security track: there is enough room for imagination and innovative gameplay on the chain, but at the same time it is like a "dark forest", full of bloody and cruel zero-sum games, and ordinary investors are more likely to play the information asymmetric role of "hunted".
On November 16, many community users reported that the on-chain transaction terminal DEXX was stolen. Subsequent analysis showed that there were obvious loopholes in the management of DEXX private keys, and it was even transmitted and stored in plain text. As of now, the total loss according to incomplete statistics is more than 20 million US dollars.
In this context, how ordinary users can improve their on-chain self-protection mechanisms has become an important topic of concern to everyone. Veronica, co-founder and CEO of SafePal, also participated in the 𝕏 Space event hosted by 137Labs, "Security Thinking Triggered by the DEXX Incident: How to Avoid the "Pits" in Crypto Investment", and discussed the DEXX security incident with BlockSec founder Andy, senior trader Huisuo Ge, 137Labs researcher OneOne, and others, and provided practical security advice for crypto investors.
This article is a summary of the wonderful sharings of the guests in Twitter Space, which is specially compiled for readers.
The "unbearable burden" of preemptive bot tools
In crypto investment, high returns and absolute security are often difficult to strike a balance. Although Trading Bot tools such as DEXX and Unibot have won the favor of users with one-click copy trading and fast fund transfers, this convenience is built on a centralized architecture and requires users to authorize funds or provide wallet access rights, resulting in a significant increase in asset risks.
It’s just that users generally underestimate the security requirements of these trading tools. They are accustomed to trusting large exchanges, but ignore the risks of smaller tool platforms. The DEXX incident exposed the fatal loopholes of some trading tools in private key management. A true "non-custodial wallet" should ensure that private keys are only stored on user devices, rather than relying on centralized servers. Even if the private keys are encrypted, the lack of technical support for memory-level security protection (such as TEE or enclave) still cannot avoid the possibility of theft.
At the same time, the attack method was complex, and the hackers dispersed the funds to increase the difficulty of tracking. This not only made it more difficult to recover the funds, but also indicated that similar incidents in the future might be more complicated and difficult to prevent. This gave rise to two possibilities: either the platform was breached due to technical loopholes, or there was internal embezzlement or deep infiltration. If it is the latter, the future risks might be more serious.
Dune data shows that the top five bots in terms of trading volume are: Trojan, BonkBot, Maestro, Banana Gun, and Sol Trading Bot. Their 7-day trading volume is over US$100 million, and their cumulative number of users is over 300,000. Because of this, the mentality of "either make huge profits or lose everything" has caused most users to ignore the huge potential risks.
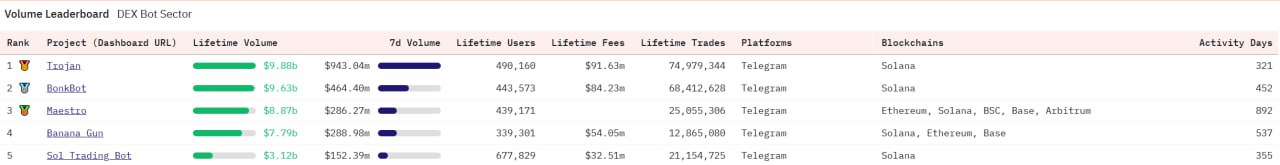
Image source: Dune
Veronica believes that almost all such “front-running” trading tools may face similar security risks. The reason why such bots can achieve ultra-fast on-chain transactions and avoid manual signatures every time is that they sacrifice some security and non-custodial features:
Usually, whether using a hardware wallet, APP wallet or browser plug-in wallet, users need to spend a few seconds to manually sign and confirm. However, in order to increase transaction speed and optimize user experience, these bots usually compromise and minimize the security of some private keys to achieve faster transactions.
This design is not completely wrong, nor can we simply say that these projects are unsafe. However, it does place extremely high demands on the security protection capabilities of the development team. In order to achieve a smooth experience, if the development team cannot ensure strong security attack and defense capabilities, once an attack occurs, the consequences will be extremely serious, and both users and project parties may face huge losses.
In addition, the design of most current trading bots does face a significant security risk - in order to achieve automated trading, they usually generate and keep private keys for each user. Although this method is convenient for users to perform automated follow-up, it also brings extremely high security risks. If an attacker breaks into the platform, all stored user private keys may be leaked, resulting in asset loss.
Image source: DEXX " Wallet Management " page
However, there is actually a more secure trading architecture that can achieve automated trading without using the user's private key:
This architecture relies on smart contracts. By creating a "PDA account" associated with the user account, transactions can be completed without the user's private key signature. The platform can execute transaction instructions through a restricted "operation account", but the permissions of this operation account are strictly controlled. It can only perform transaction operations and cannot transfer user assets at will.
This smart contract-driven design can significantly improve security because the user's private key is always in their own hands and will not be stored on a centralized server. Although this design is more complex and requires higher engineering capabilities and security technology from the team, it is completely feasible and safer.
Currently, most users are not clear about the difference between these two design patterns, or they ignore security in pursuit of convenience. However, with the frequent occurrence of security incidents, users and development teams may pay more and more attention to more secure architectures. This advanced design solution is expected to gradually become popular in the future and reduce the occurrence of similar DEXX incidents.
Web3 security chain from transaction authorization to private key protection
OneOne believes that on-chain security risks can currently be divided into two categories, covering aspects ranging from transaction authorization to private key protection.
The first common attack method is "Approve deception". For example, a small amount of encrypted assets or airdropped NFTs are sent through a "dust attack" to trick users into clicking and authorizing transactions. This operation may allow attackers to obtain the user's wallet permissions and steal the user's assets (including cryptocurrencies and NFTs). Users should be cautious when handling tokens and airdrops from unknown sources and avoid authorizing easily.
There are several common ways that private keys can be stolen:
The first is "malware attack", for example, some attackers pretend to invite users to test new projects and trick users into downloading executable files carrying Trojan viruses. Once the user is infected, the user's private key and account password will be easily stolen;
The second is "clipboard", where attackers gain access to the user's clipboard through phishing websites. When users copy and paste private keys, these sensitive information will be intercepted and used by attackers;
In addition, there are some cases of "remote control attacks", such as controlling the user's computer through malicious remote software, or even stealing the private key directly when the user is resting. For example, the "fingerprint browser" commonly used by airdrop users usually involves cloud storage functions. If it is cracked, the user's assets will be easily stolen. Many users do not set up two-factor authentication (2FA) when using these tools, which further increases the risk;
Finally, there is the "input method hidden danger". Many users like to use smart input methods, but these input methods may collect users' input data and store it in the cloud, which also increases the possibility of private key leakage. It is recommended that users try to use the input method that comes with the system. Although it has fewer functions, it is more secure;
In general, users need to take additional security precautions when trading on the chain, especially when using DeFi applications or trading tools. Among them, authorization management is an issue that needs to be highly valued. Since Ethereum's mechanism requires users to grant token authorization to smart contracts, attackers can use this authorization mechanism to perform malicious operations. Therefore, users should frequently check the authorization list of their wallets and revoke authorizations that are no longer needed in a timely manner, especially those early authorizations that may have been forgotten, to reduce risks.
In addition, when users choose a DeFi platform, they should review the platform's security measures, including whether there are comprehensive audit reports, continuous automated security monitoring, and whether the platform is regularly upgraded and vulnerabilities are fixed. When using Trading Bot, users are advised to manage their assets in a decentralized manner and not to store large sums of money in accounts controlled by trading robots. After making a profit, the funds should be transferred to a safer wallet as soon as possible to reduce possible losses.
Brother Huisuo said that as a trader, it is crucial to be familiar with the trading tools and platform mechanisms. In the current dog trading environment, many people only focus on the excitement of skyrocketing and plummeting, and ignore the potential safety hazards of trading tools. Users should set up security alerts, such as pool drain or liquidation warnings, to control risks at any time.
Veronica emphasized a simple but important principle: there is always a compromise between efficient pursuit of profits and comprehensive security, so the most critical advice is to isolate funds. If you find yourself unable to sleep and frequently checking your phone because of anxiety caused by large investment positions, it is likely that your capital allocation has exceeded your risk tolerance.
What are some practical on-chain security query tools?
Veronica recommends that users use the built-in security tools of non-custodial wallets such as SafePal, such as the function of regularly checking authorizations - users can scan all their authorization records on multiple chains and revoke unnecessary authorizations with one click to reduce the risk of being exploited by hackers.
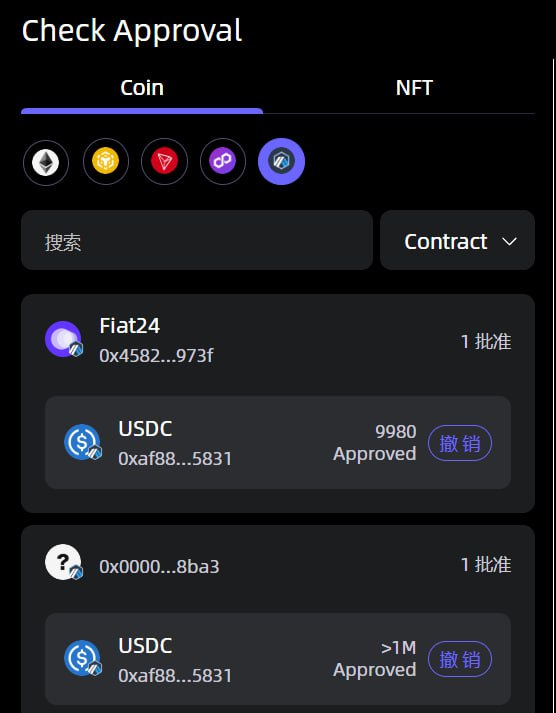
Image source: SafePal "Approval Manager" function
In addition, scammers often disguise themselves as users' transfer addresses through small transfers to defraud funds. Currently, mainstream wallets such as OKX Web3 Wallet and SafePal have added risky transaction interception services for "head-to-tail attacks". At the same time, hardware wallet + passphrase is also a lesser-known but very practical function, especially for users with multiple cryptocurrency trading accounts:
The passphrase is the 13th word and is combined with the original 12 mnemonics to generate a new wallet address. Even if someone obtains your mnemonics, they cannot access your assets without the passphrase. This means that users can create multiple wallet accounts in this way to ensure security.
This method not only increases the security of private keys, but also allows users to flexibly manage assets between multiple accounts, and the passphrase can only exist in the user's mind, further improving security.
Andy also emphasized that many times when users encounter security incidents, in addition to the risks of the project itself, it may also be related to the users' own lack of security habits. Even if users are aware that they hold a large amount of crypto assets or know that investment transactions are risky, they often expose their assets to danger due to bad habits.
It is recommended that users maintain isolated security awareness and habits, such as storing large assets in cold wallets, which are only used for interaction and not for direct transfer of funds. At the same time, use a dedicated mobile phone (such as iPhone) to manage encrypted assets, and only use it for cryptocurrency transactions or private key management. Do not install other software unrelated to transactions or conduct other activities on this device. This can significantly reduce the risk of private key leakage.
Conclusion
The DEXX security incident reveals the core dilemma in the field of on-chain trading tools: how to find a balance between convenience and security?
While pursuing efficient transactions and user experience, the platform's security design cannot be sacrificed. Whether it is the centralized storage of private keys or the technical shortcomings of lacking memory-level protection, user assets will be exposed to high risks.
"There is always a compromise between high returns and absolute security." For investors, understanding the risk logic behind trading tools and cultivating good safety habits are the basis for crossing the "dark forest" on the chain. In this decentralized and uncertain ecosystem, only by controlling your own private keys can you truly control your assets and promote a healthier development of the entire chain ecosystem.













