 Hash (SHA1):f167e6587a02a65c21d08a3f23ea7669be341deb
Hash (SHA1):f167e6587a02a65c21d08a3f23ea7669be341deb
No.: Lianyuan Security Knowledge No.046
GRASS, also known as Xiaocao in China, is a project that allows users to obtain airdrop tokens by hanging up a web page.
Their concept is interesting: Currently, many large companies are secretly using your network bandwidth, such as the infamous Baidu Cloud Disk. They use your network connection to obtain some information, such as checking prices, viewing ads, etc., which is completely "free" your network resources, and most people don't notice it.
In response to this phenomenon, Grass proposed that they would cooperate with some certified companies and research institutions to share the bandwidth shared by users with these institutions, and GRASS would airdrop bandwidth to users who shared their idle bandwidth with them.
Nearly a year after GRASS launched the project, on October 28, the GRASS project airdropped tokens to all users.
The current price of the airdropped token is 1.5u/$GRASS. Before the market opens, pre-market trading is available on multiple exchanges such as OKX, Gate, HTX, etc. On October 28, it was officially launched on Bitget, Bybit, HXT, Gate and other exchanges.
Hang up
Before talking about GRASS proxy hacking, we first need to talk about GRASS's anti-witch mechanism.
Anti-Witch Mechanism:
GRASS's anti-witch mechanism is to check your computer's "abnormal network activity" to prevent witches. That is, if the IP of your account changes frequently, then the GRASS project party is likely to add your account to the witch list. This mechanism is somewhat accidental, especially for domestic users. Domestic users will use VPN to participate, and some VPN nodes will be very unstable, or users will frequently change connection nodes. Therefore, the project party shows that the IP of domestic users is unstable, so it is easy to include domestic users in the witch list. In order to seek a stable IP, domestic users will run a VPN. The studio builds the platform by itself.
Node proxy:
Although most users will choose VPN as a transit node, some users who want to get more airdrops will choose to use proxy nodes.
First of all, the IP address of the node is pure, and the effect of increasing points every day is very good, which is much more than the amount obtained by personal VPN nodes.
Secondly, node proxy can prevent witches, because some project parties will check that if there are multiple accounts for one IP, then it is very likely that multiple accounts will be included in the witch list.
The last point is convenience. You only need to pay a part of the money and let others do things for you. You can collect the money without performing any extra operations.
Some people use fingerprint browsers to hang nodes. They obtain multiple IP addresses through fingerprint browsers and hang them in batches. Even if the computer is turned off, the nodes are still running.
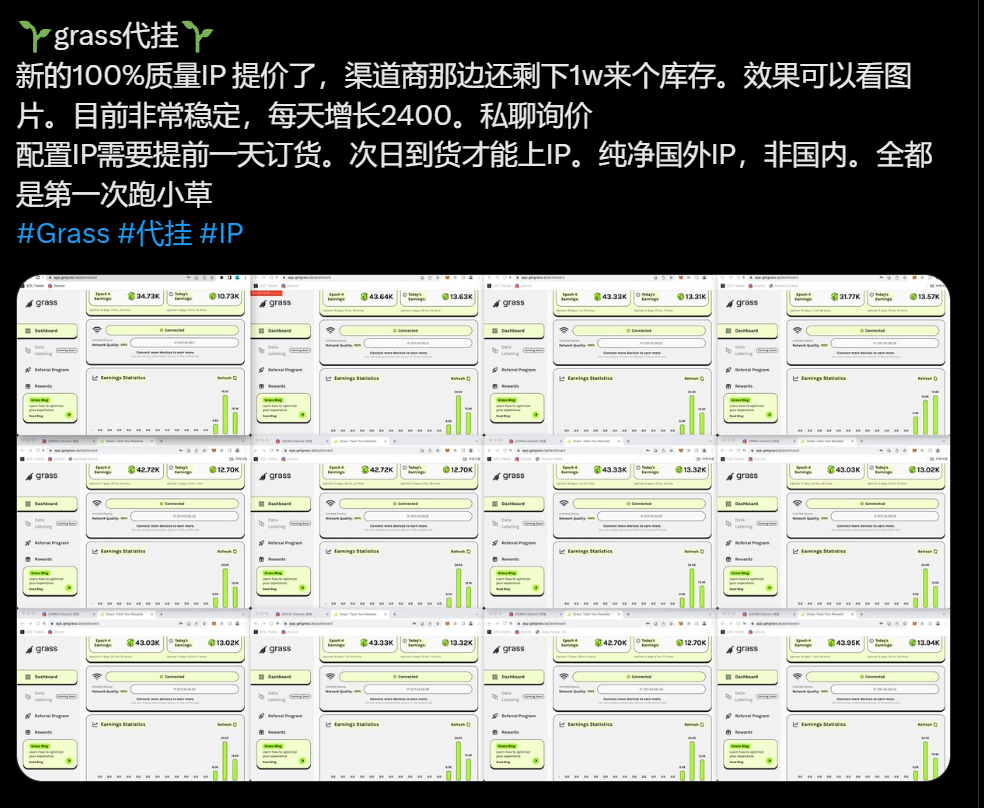
Due to the large amount of airdropped by the GRASS project, many studios and individuals who made a lot of money through proxy hacking made a lot of money. However, there are still some people who participated in the whole process but lost nearly 300,000 RMB.
Node proxy scam:
The victim was Yuyue, a KOL on Twitter. On November 2, Yuyue posted a tweet as shown below:
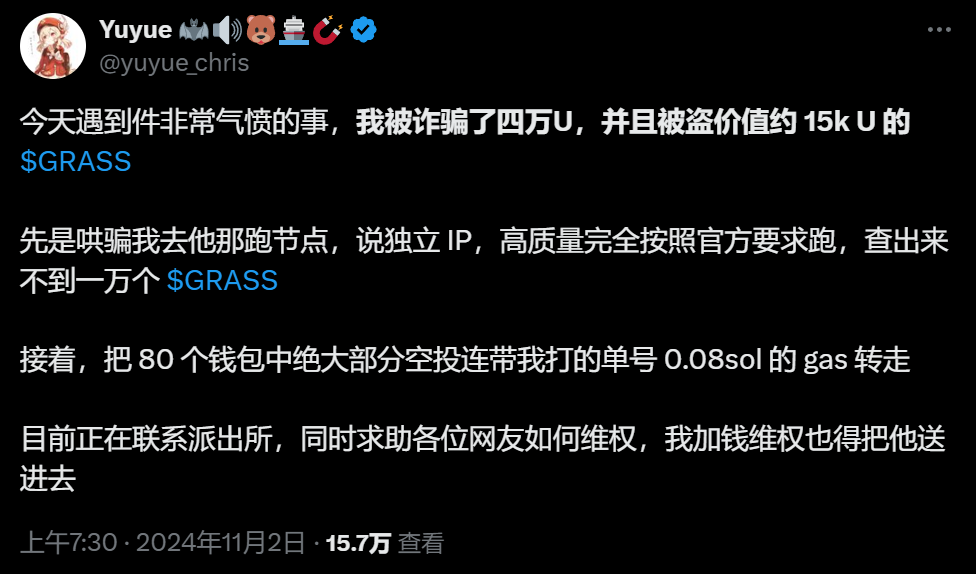
Yuyue participated in the GRASS project at the beginning of its release. Due to the good narrative and high popularity of the project, many proxy studios emerged. During this period, Yuyue's friend "Big Knife Brother" recommended a studio to Yuyue, claiming that it had an independent IP and extremely high quality that could fully meet the official requirements for nodes. So, Yuyue contacted this studio for help, and since GAS was not required for interactive operations in the early stage, the wallets used for proxy were also empty wallets. This is one of the reasons why Yuyue did not worry too much at the beginning.
When each account confirmed the number of orders, Yuyue found that all the accounts combined did not even have 10,000 $GRASS tokens. Here is another data for everyone. There was an account that was idle from January to November and received a total of 2,600 $GRASS tokens. And this node was a personal node, not idle all the time. So this is one of the reasons why Yuyue was dissatisfied with the studio.
On October 28, when Yuyue was ready to claim the airdrop, since the "Claim" operation required a certain amount of GAS to claim the airdrop, Yuyue deposited 0.08SOL (based on the market price of November 4, it was 12.69USDT) into each wallet. When he was ready to contact the agency studio to help claim the airdrop, Yuyue found that the studio had run away and even the 0.08 SOL with the order number had been transferred away.
Because of the introduction by a friend, the investment was relatively small, it did not involve his main wallet, and the studio also really had nodes running. So Yuyue relaxed her vigilance.
According to statistics, Yuyue was defrauded of 40,000 USDT in this incident, including the agency fee, GRASS airdrop, and 0.08 SOL for GAS.
Node-hanging scams are not uncommon. The scam that Yuyue encountered is unavoidable because the studio is really helping you hang the nodes. You can check it and they also communicate with you on a daily basis. It is actually very difficult to imagine that the other party will run away with the money.
Some people say that it is easy for agents to run away, so can I use a fingerprint browser to set up my own hack? In fact, it is possible, but fingerprint browsers actually have risks and have been stolen.
Fingerprint Browser:
The essence of the fingerprint browser is a browser running in the server, and you access it remotely. In this way, you can purchase many server nodes in the fingerprint browser and operate multiple nodes in batches on your computer.
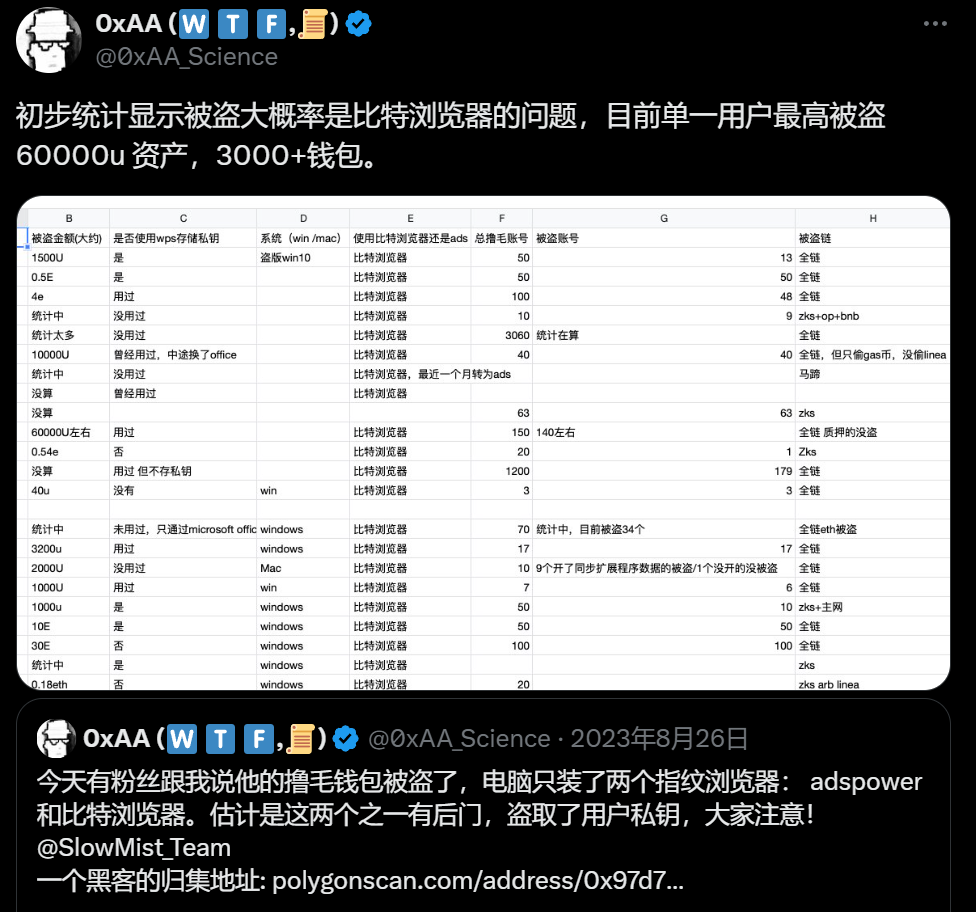
Many "money-grabbing" KOLs have noticed this and used it as the main tool for airdrops. Among fingerprint browsers, the most famous one is BitBrowser. It was this browser that caused the theft of a large number of assets.
On August 26, 2023, many KOLs and members of the crypto community posted that their wallets used in the Bit Browser were stolen. Most of the funds were transferred as GAS, and they were funds from the entire chain, not just a single chain. According to statistics, the total stolen value was 1.5 million US dollars.
Judging from the on-chain data, all theft types are private key leaks.
BitBrowser claimed that the assets were stolen because the server cache was hacked. User wallets that have enabled extended data synchronization are at risk of theft. Hackers would obtain the user's wallet private key synchronized to the server through the server cache, and then transfer the funds in the user's wallet.
So we can see that fingerprint browsers are also unsafe. After all, what you buy is just the right to use a server, and others can obtain and monitor your personal information and information stored in the browser at any time.
So how should we prevent the above two types of theft?
Prevention
Before airdropping, you can judge whether you need an independent node or a pure node based on the type of project. If not, you can use Google's multi-opening method, that is, open multiple Google browsers on the same computer at the same time, and different browsers correspond to different social media accounts, wallets, etc.
However, if you need an independent node or a pure node, you can choose to rent an overseas server, build your own network environment, or build your own VPN. We will not go into details here, and you can check the specific methods yourself.
Although the above operations are more troublesome, they are indeed safe and stable.
But if you still want to keep things simple and save trouble, or want to find a proxy or use a fingerprint browser, then you need to pay attention to the following points:
Research on the agency studio
First, get reviews of the corresponding studio through social media such as communities and Twitter. If no one mentions the studio, don't touch it.
Second, contact the studio to check if it has an offline address. If you can find the offline address of the studio, you can prevent it from losing contact to a large extent.
Third, when transferring money, confirm the contact’s identity information and make sure the contact’s phone number and WeChat account match the name used in the transfer.
IP sources of proxy studios
First, understand the service provider from which the IP address comes and check whether the quality provided by the service provider is satisfactory.
Second, you can ask the proxy studio for the IP address and use the Whois tool to query the IP to see whether it belongs to the computer room IP or a personal pure IP. If the project party has high requirements for the IP, it is likely that the computer room IP will be protected from witch operations.
Third, you can compare the IP information you find with the information provided by the studio to see if it matches what was promised.
Signing a contract
If the agency fees involved are large, a contract can be signed to make the agency work legally effective and prevent the studio from running away.
Fingerprint Browser
First, check whether the official Fingerprint Browser has permission to view your private key or wallet password.
Second, enter the settings of the fingerprint browser, check the data synchronization options, and turn off data synchronization to avoid unnecessary sensitive information being uploaded to the cloud.
Third, do not store too many assets in the fingerprint browser wallet. Only store necessary GAS fees, and transfer them when you need to use them.
Conclusion
Airdrops are a small-scale investment for a big gain. It is not worthwhile to lose a lot of money on something that should be done with a small amount of money. If you are technically savvy, you can use a server to divide the nodes. If the airdrop does not check the IP, you can Google it. If you check the IP and you are too lazy to do it, then you must be very careful in choosing a studio and using a fingerprint browser. Please follow our methods to ensure the safety of your funds. For more security content, please follow our gzh: chain source security.














