Author | Huo Huo
Produced by|Baihua Blockchain
Last Saturday, the world's second largest CEX Bybit was hacked, and a total of $1.46 billion in ETH was stolen, setting a record for the highest single token theft in history. On February 24, crypto financial card service provider Infini was also hacked, and about $49.5 million in funds were stolen from its Ethereum address. This series of security incidents has made the already sluggish crypto market even worse, not only exposing that crypto platforms are still not rigorous enough in asset security management, but also further weakening market liquidity. Security issues have once again become the focus of industry attention.
It can be said that crypto security incidents have occurred frequently in recent years, involving multiple targets such as CEX, DeFi platforms and cross-chain bridges. According to a report by blockchain analysis company Chainalysis, hackers stole approximately US$2.2 billion in crypto assets in 2024. So far, the cumulative amount of theft has exceeded US$5 billion (approximately RMB 36 billion).
Today, let’s review the top ten crypto security incidents in the past (including the Bybit theft in February 2025). The 36 billion yuan of assets lost in these ten security incidents are a "bloody lesson" for the owners. For individuals, what important tips can we get from them to protect crypto assets?
01. Top 10 Crypto Security Incidents
The figure below shows the top ten crypto security incidents sorted by the amount of loss. These incidents cover a variety of complex attack methods ranging from smart contract vulnerabilities to private key leaks, database attacks, etc.
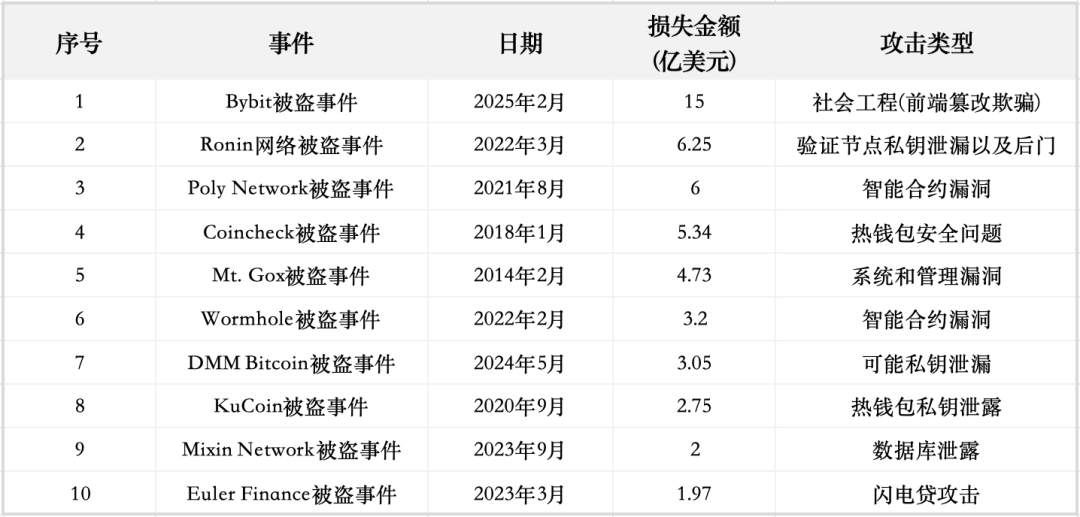
Through analysis, we can see that these thefts not only expose specific security vulnerabilities, but also reflect the weaknesses of the encryption industry in technical protection and risk management.
Next, we will classify and analyze these incidents based on the causes of their occurrence and the lessons they bring, so as to better understand the security risks behind them and provide reference for future prevention.
1) Wallet private key or security issues
- Ronin cyber theft (March 2022): $625 million
The Ronin Network is a scaling solution designed specifically for blockchain games and NFTs, created by Axie Infinity development team Sky Mavis to address Ethereum’s limitations in transaction fees and processing speeds.
In March 2022, the Ronin network was attacked by the North Korean-backed hacker group Lazarus Group, resulting in a loss of approximately $625 million in Ethereum and USDC. The hacker successfully controlled 5 nodes by attacking the network's verification nodes, enabling them to create and sign malicious transactions, ultimately transferring funds to addresses under their control.
- Coincheck theft (January 2018): $534 million
Coincheck is one of the more well-known CEXs in the Japanese crypto market. It was founded in 2012 and is committed to providing safe and convenient trading services.
In January 2018, Coincheck was hacked due to hot wallet security issues, losing approximately $534 million in NEM tokens.
- DMM Bitcoin theft (May 2024): $305 million
DMM Bitcoin is also a Japan-based crypto CEX founded in 2018.
In May 2024, DMM Bitcoin was hacked, resulting in the theft of approximately 4,500 bitcoins (worth approximately $305 million at the time). Although the specific methods of the attack are still under investigation, according to relevant reports, the leaked private key may be the key factor in the hacker intrusion.
- KuCoin theft (September 2020): $275 million
KuCoin is a well-known CEX in Singapore, founded in 2017.
In September 2020, KuCoin was hacked and lost approximately $275 million in various crypto tokens. The hacker successfully stole a large amount of assets by obtaining the private keys of the CEX hot wallet.
Summarizing these four thefts, we can see that they were all stolen because of insufficient security of hot wallets or nodes. Verification nodes and hot wallets are easily targeted by hackers because they are connected to the Internet and are more convenient. There are many ways for hackers to attack, including obtaining private keys through malware, phishing attacks, or exploiting internal vulnerabilities in the platform. Once the attack is successful, hackers can quickly transfer assets, causing irreparable losses. Relatively speaking, cold wallets and other storage places that are not connected to the Internet can effectively avoid the risk of online attacks and become a relatively safer choice for storing encrypted assets.
In addition, for CEX, ensuring the strict management and storage security of private keys is the key to preventing large-scale fund theft; and for individual users, properly keeping private keys also determines the security of assets. Once the private key is lost or leaked, the user will completely lose control of the assets because no third party can help recover the funds. Therefore, both CEX and individuals need to establish more complete key protection measures to reduce security risks.
2) Smart Contract Vulnerabilities
- Poly Network theft (August 2021): $600 million
Poly Network is a cross-chain protocol that allows users to seamlessly transfer and exchange assets between multiple blockchain platforms, enabling cross-chain transactions and collaborative work.
In August 2021, the Poly Network cross-chain bridge was hacked due to a smart contract vulnerability, resulting in a loss of approximately $600 million in various tokens. The hacker exploited the vulnerability to bypass permission control and transferred a large number of tokens to his own address. However, surprisingly, the hacker subsequently negotiated with the platform and gradually returned most of the stolen funds. 
- Wormhole theft (February 2022): $320 million
Wormhole is a decentralized cross-chain bridge protocol that allows users to transfer assets between multiple blockchain networks without relying on the ecosystem of a single chain.
In February 2022, the Wormhole cross-chain bridge was hacked while connecting Solana and the Ethereum blockchain, resulting in the theft of approximately $320 million in wrapped Ethereum (wETH). The attacker exploited a vulnerability in the cross-chain bridge smart contract, bypassed the verification mechanism, minted a large amount of wETH without authorization, and withdrew it to his own address.
The security incidents of Poly Network and Wormhole exposed the vulnerability of cross-chain protocols in the process of asset transfer and verification. Especially in the management and verification of cross-chain assets, loopholes can be easily exploited by hackers, causing huge losses. This reminds us that the design of cross-chain protocols must pay more attention to the permission control in smart contracts to ensure the verifiability of operations, especially in the management and verification of cross-chain assets.
In order to improve security, cross-chain platforms need to conduct comprehensive security audits and vulnerability checks regularly to promptly identify and fix potential problems. At the same time, it is recommended to introduce a multi-signature mechanism and stricter permission management in contract design to avoid single point failures or hackers controlling key permissions. In addition, there should also be a strict process for updating and maintaining cross-chain protocols to ensure that each repair and upgrade is fully tested to improve the security of the cross-chain platform, reduce the risk of attacks, and protect user assets.
3) System vulnerabilities or database leaks
- Mt. Gox theft (February 2014): $473 million
Mt. Gox was once the world's largest Bitcoin CEX, with its trading volume once accounting for about 70% of the global Bitcoin trading volume. It was founded in 2010 and is headquartered in Japan. It played a key role in the early boom of the crypto industry.
However, in 2014, the CEX went bankrupt due to multiple security breaches, which led to the theft of approximately 850,000 Bitcoins (worth approximately $473 million at the time), becoming one of the most sensational scandals in the history of cryptocurrencies. The attack exposed the problem of insufficient monitoring mechanisms and slow response to suspicious activities, and the specific modus operandi of the hackers has not yet been fully identified.
- Mixin Network theft (September 2023): $200 million Mixin Network is a decentralized cross-chain protocol designed to solve interoperability issues between blockchains.
In September 2023, the Mixin Network peer-to-peer trading network was hacked due to a database leak of a cloud service provider, resulting in the theft of approximately $200 million in Bitcoin and Ethereum assets.
These two incidents exposed the serious risks of system vulnerabilities and database leaks in the crypto industry. The Mt. Gox incident highlighted the lack of adequate security monitoring and response mechanisms in crypto CEX, while the Mixin Network incident reminded us that we must be extra careful when relying on third-party cloud services. In order to avoid similar problems, platforms should strengthen multi-level security protection, establish a comprehensive monitoring and emergency response system, and ensure that cooperation with third-party suppliers has sufficient security guarantees.
When dealing with such incidents, first of all, do not put all your "eggs" in one basket; secondly, we also need to pay attention to whether this "basket" has sufficient compensation capacity when problems occur. Especially in the field of encryption, when choosing CEX or other platforms, you must ensure that they have sufficient reserves and financial health to cope with potential large losses. At the same time, it is also necessary to evaluate the platform's risk response mechanism, insurance policy and historical compensation record. After all, risks are sometimes unavoidable, and choosing a platform that can take responsibility in times of crisis is also responsible for yourself.
4) Front-end tampering fraud
- Bybit theft (February 2025): $1.5 billion
Bybit is a crypto CEX founded in 2018 and headquartered in Singapore, mainly providing crypto derivative products.
After being hacked on February 22, 2025, about $1.5 billion of Ethereum and other related pledged assets were lost. The incident involved cold wallet transaction manipulation. The hacker displayed the correct address through a deceptive signature interface and changed the underlying smart contract logic to transfer funds to an unauthorized address. This attack method shows that even cold wallets are not absolutely safe.
Although cold wallets are safer than hot wallets, we also see from the Bybit theft that security awareness is always the most important. In addition to choosing a CEX with a good security record, wallet management, transaction verification, and secure operation procedures are also crucial, because cold wallets are not omnipotent.
It is reported that the root cause of the Bybit theft is attributed to the Safe multi-signature problem and attack methods. The attacker launched a malicious disguised transaction against Bybit through the damaged signing wallet Safe developer machine, which shows that due to the insufficient security protection of developer devices and credentials, even if there is no obvious smart contract vulnerability or source code problem, it will be hacked.
This reminds us that in addition to choosing a CEX with a good security record, wallet management, transaction verification and safe operation procedures are crucial, and developers' machines, credential management and every step of the operation should strengthen security awareness. At the same time, users need to be extra cautious when signing transactions and remain highly vigilant to ensure that there is no negligence in every step of the operation.
5) Flash Loan Attack
- Euler Finance theft (March 2023): $197 million
Euler Finance is a decentralized financial platform built on Layer 2 networks such as Ethereum and Optimism, dedicated to providing seamless and efficient lending and borrowing services.
In March 2023, the Euler Finance decentralized lending platform suffered a flash loan attack, resulting in the theft of approximately $197 million in various tokens. The attacker exploited a vulnerability in the platform's smart contract, manipulated market prices through flash loans, triggered the platform's liquidation mechanism, and illegally stole funds.
This incident once again reveals the potential loopholes in the smart contract design and market mechanism of decentralized financial platforms. Flash loan attacks usually rely on manipulating market prices and triggering liquidation mechanisms, exposing the platform's weaknesses in price prediction and market stability. In order to deal with such attacks, the platform should focus on reviewing the code of smart contracts, especially those involving market manipulation and liquidation mechanisms, and strengthen security protection.
In addition, security audits and historical reputation are key factors in assessing the reliability of a project. Even if a project promises high returns, do not ignore the potential risks and avoid falling into traps. Whether you hand over your funds to a centralized platform or use a decentralized application, you need to be cautious and do not take it lightly.
02. What security suggestions do you provide to individual currency holders?
Looking back at these security incidents, it is not difficult to find that CEX’s security vulnerabilities, mistakes in private key management, and the upgrading of hacker methods are constantly threatening the security of encrypted assets.
These events not only reveal the hidden risks in the world of digital assets, but also provide us with valuable experience. Learning how to identify potential threats and adopt safer storage and transaction methods is a topic that every crypto user needs to pay attention to.
Next, we will summarize several key security recommendations from these cases, hoping to provide practical references for everyone when managing digital assets, help reduce risks, and avoid becoming the next victim.
1) Choose a reputable platform
Choosing a CEX or platform with a good security record and transparent disclosure of security measures is the first step to protecting personal assets.
2) Use cold storage to protect assets
Storing important digital assets in cold wallets is an important means of preventing hacker attacks.
3) Enable two-factor authentication (2FA)
By binding a mobile phone, email or dedicated authenticator, users can add an extra layer of security when logging in, which can effectively prevent unauthorized access to the account. Regularly checking and monitoring account activities is an effective means to promptly detect suspicious transactions and potential threats.
5) Diversify investments to reduce risks
Spreading assets across multiple platforms or wallets can spread risks. For example, users can keep most of their assets in cold wallets and use a small amount of funds for daily transactions, or spread them across different trusted CEXs to reduce the overall loss caused by problems on a single platform.
6) Trustlessness
The most important feature of crypto assets is that they are verifiable. Do not trust any third party to ensure your crypto security by default, including software and hardware provided by wallet developers. At the same time, do not default to operating personal Internet devices as "non-fully secure devices". You must personally verify that every transaction information you submit and sign is accurate.
03. Summary
It can be said that security prevention is not only a response to problems, but also a proactive strategic layout. Crypto asset management is not only about dealing with immediate risks, but also about ensuring long-term stable development. By cultivating daily safety habits, gradually strengthening protection capabilities, and preventing risks at every stage, we can effectively minimize risks.













