Even though Web3 has built powerful tools and infrastructure, the average internet user still lives in Web2.
Written by Figo @IOSG
Preface
Cryptocurrency has come a long way. Layer 2 scaling solutions have been launched, zkVMs have been introduced, and even ETFs have been approved. However, most people still feel that the blockchain space is an isolated world - something they have only read about in the text, but have not actually used.
Why this happened
The answer lies not in the technology itself, but in what it currently cannot touch: our digital lives. Although Web3 has built powerful tools and infrastructure, ordinary Internet users still live in Web2 — browsing, transacting, and socializing on centralized platforms that control their data.
Until we can connect these two worlds in a trustless, privacy-preserving way, mainstream adoption will remain elusive.
Why Web3 Hasn’t Yet Breakthrough
We interact frequently online — through banks, social media, streaming platforms, government portals. But all of this happens within tightly controlled ecosystems. Our digital identities are scattered across platforms, each holding a piece of our lives: a bank statement here, a passport scan there, a job history on LinkedIn.
This fragmentation creates two fundamental problems:
- Data silos: Your online identity is scattered across platforms, each with its own rules and permissions.
- Lack of ownership: You don’t actually own your data. At best, you have access to it — access that can be revoked, restricted, or arbitrarily monetized by others.
These issues manifest in the frictions we face every day. Want to prove your income? You might need to hand over a full bank statement. Need to verify your address? Be prepared to upload your entire utility bill. These systems assume that full transparency is the only way to build trust because there is no infrastructure for selective, verifiable disclosure.
Web3 promised to give users control, but so far it has failed to deliver on that promise — at least when it comes to everyday, Web2-derived data.
The Missing Piece: Verifiable Web2 Data
This is the real bottleneck: enabling Web3 applications to leverage the data we already generate — without compromising user privacy or introducing new trusted intermediaries.
There are two key challenges:
- Verifiability: How can we cryptographically prove that data from a Web2 source is trustworthy without relying on centralized oracles or APIs?
- Privacy: How do we prove only what is necessary — without exposing the full data behind it?
Chainlink and other oracle providers have solved some of the verifiability problem, especially for public data like asset prices or weather conditions. But personal, user-specific data — like financial records, qualifications, identity credentials — requires a different approach. These data points exist behind-the-scenes, within encrypted channels, and they are not designed to be extracted or shared.
This is where zkTLS comes in.
What is zkTLS?
Most of the internet runs on TLS (Transport Layer Security) — the encryption protocol that powers HTTPS. It protects about 95% of web traffic. When you visit a website, TLS ensures that your communications are encrypted and cannot be tampered with.
zkTLS (zero-knowledge TLS) builds on this foundation with something entirely new: it allows users to extract and prove specific facts from Web2 data streams without revealing the full content or having to trust a third party.
This unlocks two key abilities:
- On-chain verifiability: zkTLS can prove that data comes from a specific Web2 source and has not been tampered with.
- Selective disclosure: It’s the ability to prove specific attributes — like “my annual income is over $80,000” — without revealing actual bank statements.

How does it work? In simple terms:
- It captures encrypted TLS sessions between users and websites.
- It generates a zero-knowledge proof that proves a specific claim (such as that a certain value appears in a response).
- This proof can then be verified on-chain — trustlessly and privately.
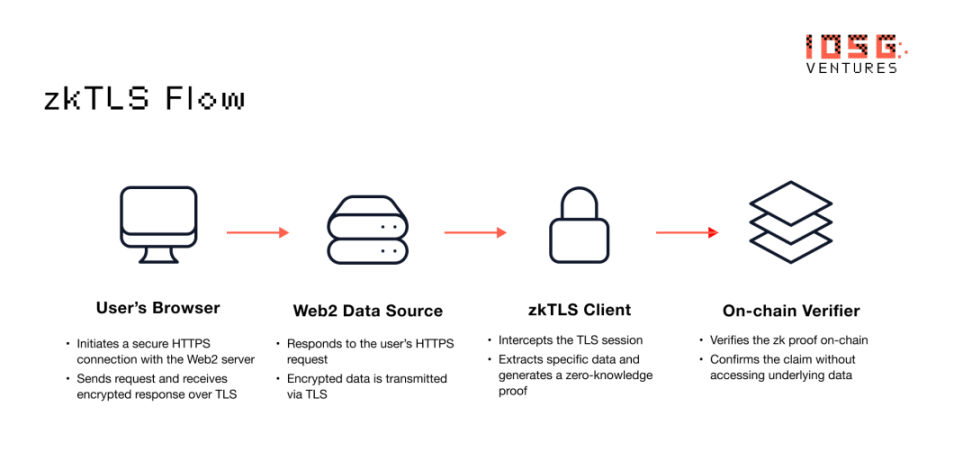
▲ Source: IOSG Ventures
This avoids the need to expose data to a third party or trust a centralized server to prove the data. Instead, trust is embedded in the cryptographic proof itself.
This isn’t just theory. Implementations of zkTLS are already being tested and deployed in consumer and DeFi use cases, heralding a time when verifiable Web2 data will become the default input for Web3 applications.
How zkTLS works
Not all zkTLS implementations are created equal. Different approaches excel in different contexts, depending on what matters most — speed, decentralization, or simplicity. Here are three common architectures:
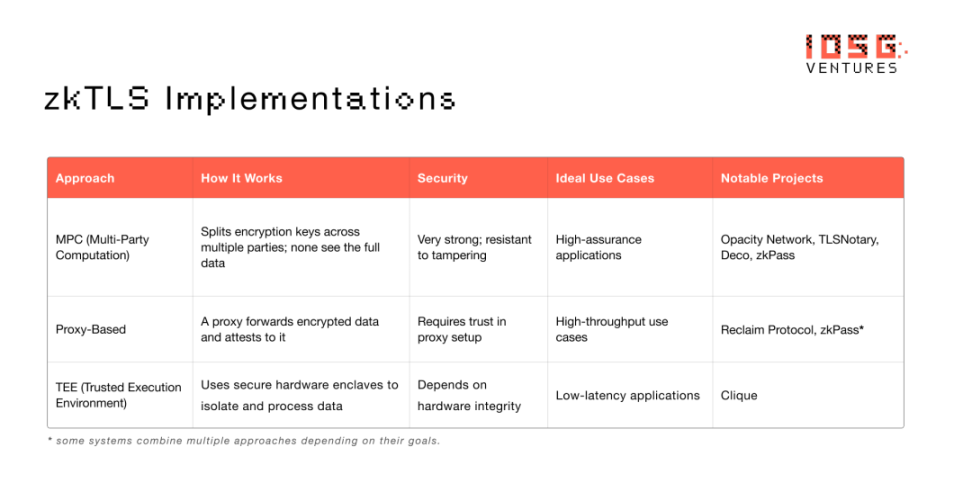
▲ Source: IOSG Ventures
Real-world applications: where zkTLS changes everything
zkTLS doesn’t just optimize data processing — it redefines the boundary between Web2 and Web3. By enabling trust-minimized, private access to off-chain data, it allows applications to integrate real-world context without compromising privacy or decentralization.
Here’s how it’s currently being used in different areas.
Financial Services
Most DeFi protocols still rely on overcollateralization due to the lack of trusted identities and on-chain financial data. zkTLS makes it possible to verify income, cash flow, or account history — without exposing sensitive documents.
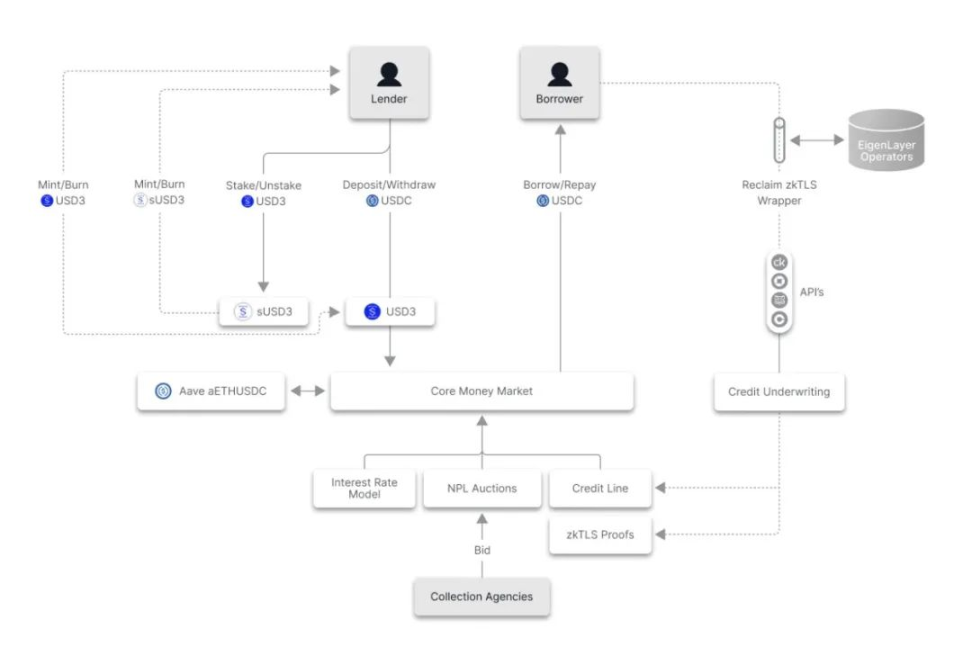
▲ Source: 3Jane
- 3Jane (3jane.xyz) is building a peer-to-pool credit protocol that provides real-time, unsecured USDC credit lines to traders, farmers, and businesses. Borrowers connect their wallets and Web2 financial data through Plaid to unlock credit based on verifiable proofs in DeFi, CEXs, and banks — no collateral required.
- Stormbit (stormbit.finance) supports a flexible peer-to-peer lending market where borrowers can privately prove income or account activity and unlock funds using zkTLS.
- The RWA (real world asset) tokenization project has begun using zkTLS to verify land or property ownership through government portals to achieve compliant on-chain assetization.
- zkP2P (zkp2p.xyz) is building a decentralized fiat-to-crypto on-ramp that lets users prove payments from Venmo, Wise, or Revolut using zkTLS — no KYC, no intermediaries, and instant settlement.
These systems expand access to capital, bring credit value on-chain, and build a compliant bridge between TradFi and crypto.
Consumer Platform
In Web2, access to digital goods, subscriptions, and purchase histories is locked behind centralized APIs. zkTLS makes this data portable and provable — without asking the platform for permission.
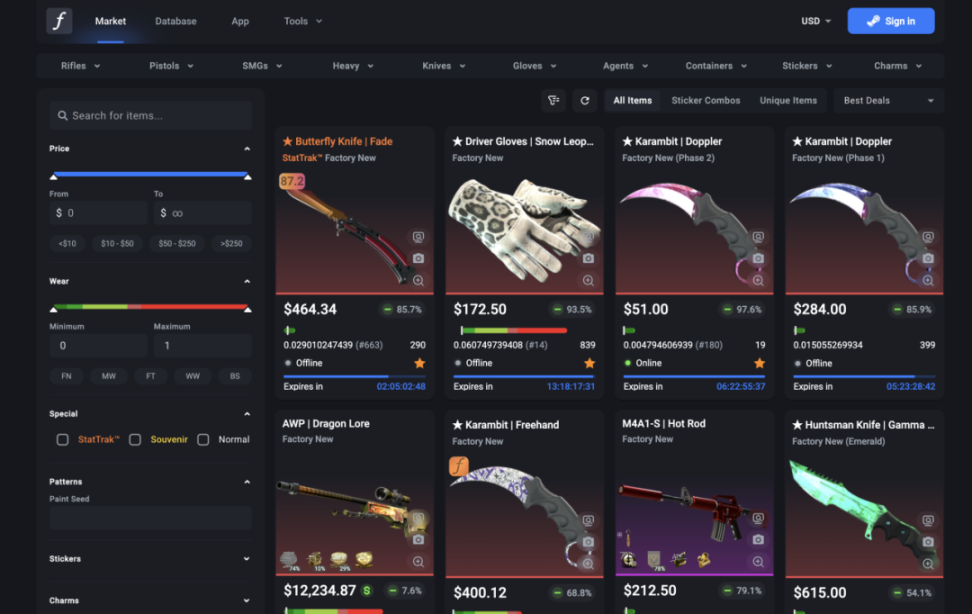
▲ Source: CSFloat
- CSFloat (csfloat.com) allows users to verify ownership of Counter-Strike skins and collectibles through Steam data, enabling secure peer-to-peer transactions without the need for platform intervention.
- zkTLS is also being used to prove access to closed communities, subscriptions, or premium content — without requiring account linking or API access.
- In e-commerce, users can prove past purchases or loyalty program activity to unlock cashback, token rewards, or resale marketplaces.
Now imagine proving you have a Spotify subscription — or a luxury brand purchase — without exposing your full account. That’s the power of zkTLS.
Identity and reputation
Today’s digital identities are fragmented and overexposed. Proving your identity often means sharing everything. zkTLS changes this by allowing selective disclosure from trusted sources.
▲ Source: zkMe
- zkMe (zk.me) acts as a privacy-preserving identity oracle that converts files and data from Web2 platforms into selective on-chain proofs.
- Zeru (zeru.finance) supports zScore, a cross-app reputation layer on Base. It verifies things like credit score, location, or Uber history — no KYC required — so users can build verifiable profiles that can be used across apps and ecosystems.
- Icebreaker (icebreaker.xyz) lets professionals create trusted, verifiable job profiles based on employment history and social graphs.
Now imagine someone builds a Web3 version of Uber or DoorDash. Drivers show up with their resume verified by zkTLS — no onboarding friction, no need to rebuild reputation.
Social and Content
The content we watch, play, and interact with says a lot — but this data is trapped in platforms. zkTLS unlocks this data, making participation portable and programmable.
▲ Source: EarnOS
- EarnOS (earnos.com) lets users prove they’ve seen or interacted with an ad — without revealing who they are. Advertisers reach real people, users get rewarded, and data stays private.
- Showdown (showdown.win) uses zkTLS to verify game profiles and performance data through FACEIT. Players can prove their skills and claim game-based rewards — no screenshots required.
This unlocks the next wave of attention marketplaces and engagement-driven rewards — ultimately portable across platforms.
Influence and Behavior
Behavioral systems — whether for fitness, sustainability, or rewards — require data that is often private and difficult to verify. zkTLS makes it possible to prove actions without surveillance.
- Daylight (https://linktr.ee/godaylight) uses IoT and registry data to verify ownership and usage of solar panels — without exposing user identity or location.
- Fit Club (x.com/fitclubonbase) ties exercise rewards to verified Strava activity without revealing fitness or GPS data.
Other applications are exploring the use of zkTLS to prove public transportation usage, recycling, or participation in environmental projects — enabling transparent, privacy-secure incentive systems.
With zkTLS, we can finally prove real-world actions — without being spied on.
Emerging Frontiers
At the edge of AI, proxying, and decentralized orchestration, zkTLS provides critical infrastructure for attestation and trust.
- ElizaOS (elizaos.ai) is building autonomous agents that generate zk-backed logs of their actions — making AI decisions verifiable and auditable.
- Ketl (ketl.xyz) enables whistleblowers and experts to prove affiliation or insight without revealing their identity — bringing credibility to anonymous communications.
- zkTLS is also used to verify training data for machine learning — ensuring authenticity while protecting contributors’ privacy.
As agents and AI become more autonomous, zkTLS anchors them to facts.
From credentials to ownership
zkTLS doesn’t just make Web2 data available in Web3 — it makes it ownable. Credentials that were once siloed in platforms become portable, programmable, and private.
As more applications adopt zkTLS, we’ll see a compounding effect: more verifiable data leads to more powerful applications, which in turn gives users greater control — and more reasons to unlock their data on their own terms.
It’s not about replacing existing systems. It’s about giving users control over them — and building a path where trust, privacy, and composability scale together.
The road ahead
If crypto is going to go mainstream, it needs to meet the needs of users — on the internet they already use. zkTLS provides the infrastructure to make this happen.
It implements:
- Cryptographic trust in data from Web2 services
- No third-party privacy protection verification is required
- User-controlled composable identity layer
- New applications based on verifiable real-world interactions
As more of our online lives become accessible through verifiable claims, a new generation of applications will emerge — applications that empower users with greater control, reduce friction, and unlock real value. zkTLS is more than just another protocol — it’s a new way of thinking about how information moves between platforms and how trust is established on the internet.











