In the digital age, cryptocurrency and blockchain technology have become increasingly important in the global financial system with their unique charm and potential. However, this field full of innovation and opportunities also breeds various frauds and security threats. In order to help users better identify and avoid these potential risks, the Bitrace team carefully compiled this "Web3 Anti-Fraud Handbook", which provides in-depth analysis and detailed disassembly of fraud methods that crypto users may encounter at different stages of growth, supplemented by real cases, aiming to provide investors with practical anti-fraud skills.
As a professional regulatory technology company, Bitrace pays close attention to current asset security incidents in addition to theoretical research and risk data monitoring. In the past year, we have received nearly a thousand cases from various channels, assisting victims in tracking and recovering funds. In the in-depth exchanges with many victims, Bitrace has accumulated valuable front-line experience, and has a deeper understanding of the psychology of victims, the usual methods of criminals, and the common types of scams in the field of cryptocurrency. It also provides a solid practical foundation and case support for the writing of the "Web3 Anti-Fraud Manual".
The Web3 Anti-Fraud Handbook is a bilingual version in Chinese and English. It will focus on six major themes from the simplest to the most complex - from the identification of information sources to the misunderstandings of asset management, from financial traps in the transaction process to phishing, to the Crypto Drainer at the end of the fraud chain and the over-the-counter fraud that may be encountered when withdrawing funds. We will reveal them one by one.
Bad sources of information: You may be being scammed from the start
Many investors first came into contact with Crypto-related concepts on social networking sites, self-media platforms, online communities, and other scenarios. These scenarios are often mixed with good and bad. Even mature investors need to find truly effective information among a lot of noise and rumors, and inexperienced investors are difficult not to be disturbed by fraudulent information. For this reason, many lawless elements take advantage of objective information barriers to defraud outsiders who lack relevant knowledge, using methods such as distorting or fabricating facts, stealing account keys, and defrauding account permissions.
Scam!
Short video QR codes, social media, and emotional scams that seem harmless but are actually dangerous often use people's curiosity, trust, and emotional needs to lure investors into traps. The Web3 Anti-Fraud Handbook will teach you how to identify these frauds and avoid being deceived from the beginning.
Wrong asset management method: the big pit at the starting point of the crypto journey
Unlike the centralized account login and verification system of traditional Web2 platforms, Web3 infrastructure such as cryptocurrency wallets do not retain user identity information and account permissions, nor do they have the settings of account cancellation, rebinding, identity information retrieval, etc. that are common in traditional Internet software platforms. This means that Web3 users need to keep their address keys by themselves. Once lost, they will permanently lose control of their on-chain identities, or on-chain assets may be stolen due to leakage.
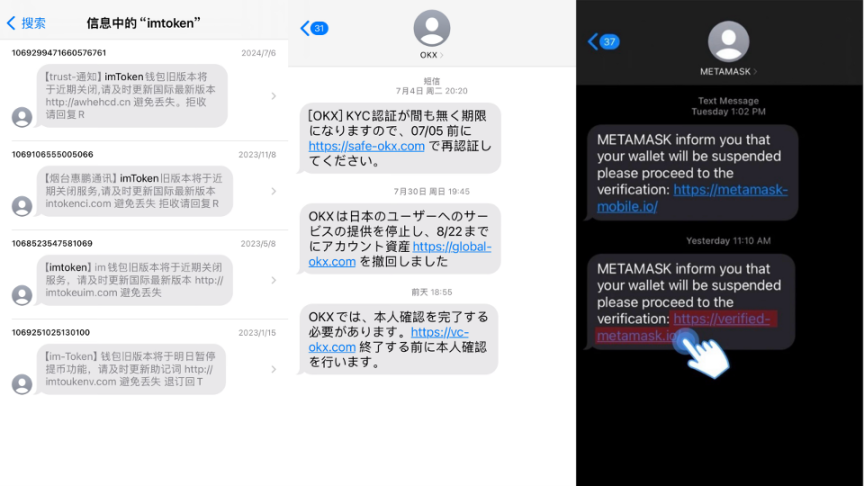
Scam Text Messages
Some coin thieves take advantage of some investors' lack of understanding of blockchain wallets and use various methods to obtain mnemonics, private keys, or wallet operation permissions, and then steal assets. The "Web3 Anti-Fraud Manual" will expose common scams such as fake wallet APP coin theft, multi-signature case payment, authorization scams, fake tg scams, hardware wallet manual fraud, etc.
When you start trading Crypto
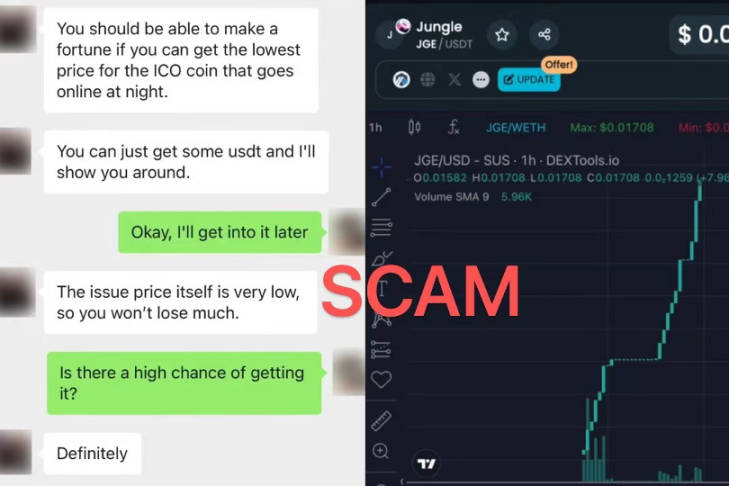
Do you think there are financial projects in the crypto market that can generate sustainable annualized returns of more than 50%? Do you think you can make stable money by "staking" your idle stablecoins in a "mining pool"? Do you think you can easily make money by buying a token and participating in the "official exchange" staking activities? If your answer is "yes", then you may be in danger.
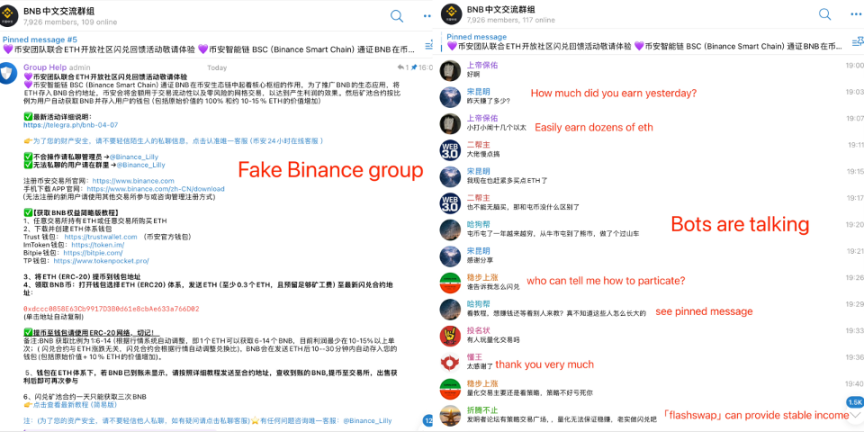
Fake Binance Group Chat Logs
We will explain to you specific cases and the truth behind the super high-yield exchange financial management scam, Pixiu coin fraud, fake Binance mining pool scam, fake OKX public chain holding USDT to receive OKT scam, liquidity exit scam, etc.
Phishing Goes Viral
Phishing is an attack method that sends fraudulent emails, text messages, phone calls or websites with the intention of inducing users to disclose sensitive information or perform malicious operations. In the traditional Internet era, such phishing activities are usually aimed at obtaining the victim's cash assets or virtual assets. In recent years, with the development of the crypto economy, more and more fraudsters have begun to target Crypto.
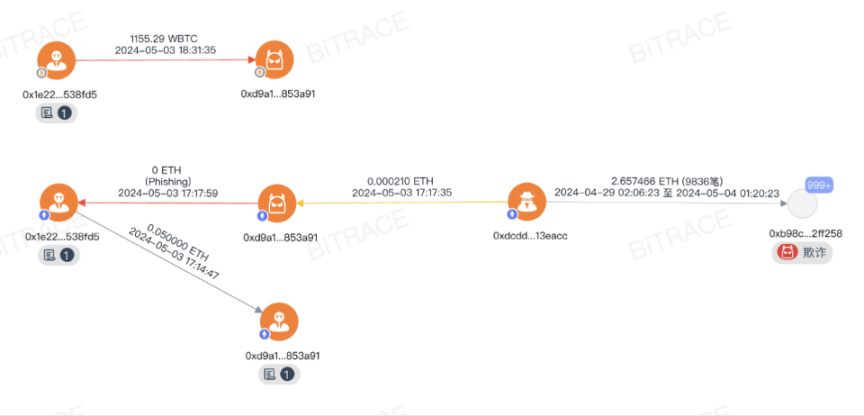
Analysis of the Address Poisoning Case
Address poisoning, advertising tokens, and withdrawal SMS are three common online fraud methods that target the crypto assets of unspecified objects. The "Web3 Anti-Fraud Manual" will discuss these in detail.
The End of Industrial Division: Crypto Drainer
Drainer is a type of malware designed to illegally empty or “drain” cryptocurrency wallets, and the software is offered for rent by its developers, meaning anyone can pay to use the malicious tool.
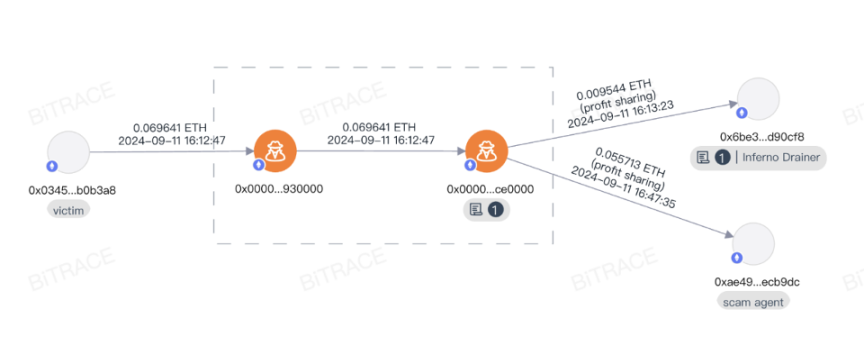
Drainer's Sharing Model
Crypto Drainer conducts reverse analysis on mainstream cryptocurrency wallet software and modifies specific codes to obtain target mnemonics. In order to help agents manage a large number of mnemonics, a special management backend is also developed, allowing agents to transfer the victim's funds or multi-sign the victim's address with one click. Behind the phishing fraud methods such as address poisoning, fake official social accounts, arbitrage scams, etc. to defraud victims of token permissions, professional Crypto Drainer is also providing technical and even operational support.
OTC fraud: the weakest link
In some countries or regions, over-the-counter (OTC) transactions are the most commonly used method for cryptocurrency investors to convert fiat currency and Crypto. Such OTC activities can occur in a variety of scenarios, such as centralized platforms, online groups, and offline. However, no matter what the scenario, OTC activities are subject to the risk of fraud, including but not limited to the fraud of fiat currency, the fraud of encrypted funds, and even threats to personal safety.

Bad Check Fraud
The "Web3 Anti-Fraud Manual" lists some common fraud methods: exchange currency fraud, offline transaction fraud, and offline multi-signature fraud.
Last words
Compared with other fields, the Web3 industry has higher barriers to entry, including the understanding of technical principles, the cost of using infrastructure, and the threshold for obtaining accurate information. Newcomers who blindly ignore these barriers often fall into traps. At the end of the Web3 Anti-Fraud Manual, we list some security suggestions and what victims should do after being defrauded.
Before you begin this learning journey, we want to emphasize that anti-fraud is an ongoing process. Fraud methods are constantly evolving, so staying vigilant and constantly learning are the keys to protecting yourself from fraud. We encourage you to use this manual as a starting point to continuously explore and update your knowledge base. At the same time, Bitrace will continue to share and analyze the latest security incidents and interpret the fraud methods involved.
If you need the PDF version of the Web3 Anti-Fraud Manual, please go to https://bitrace.io/en/blog to download it.





