
零时科技每月安全事件看点开始了!据一些区块链安全风险监测平台统计显示,2024年12月,各类安全事件损失金额较11月大幅下降。12月发生较典型安全事件超23起,因黑客攻击、钓鱼诈骗和Rug Pull造成的总损失金额达2860万美元,较11月下降约55%。
黑客攻击方面
典型安全事件7 起
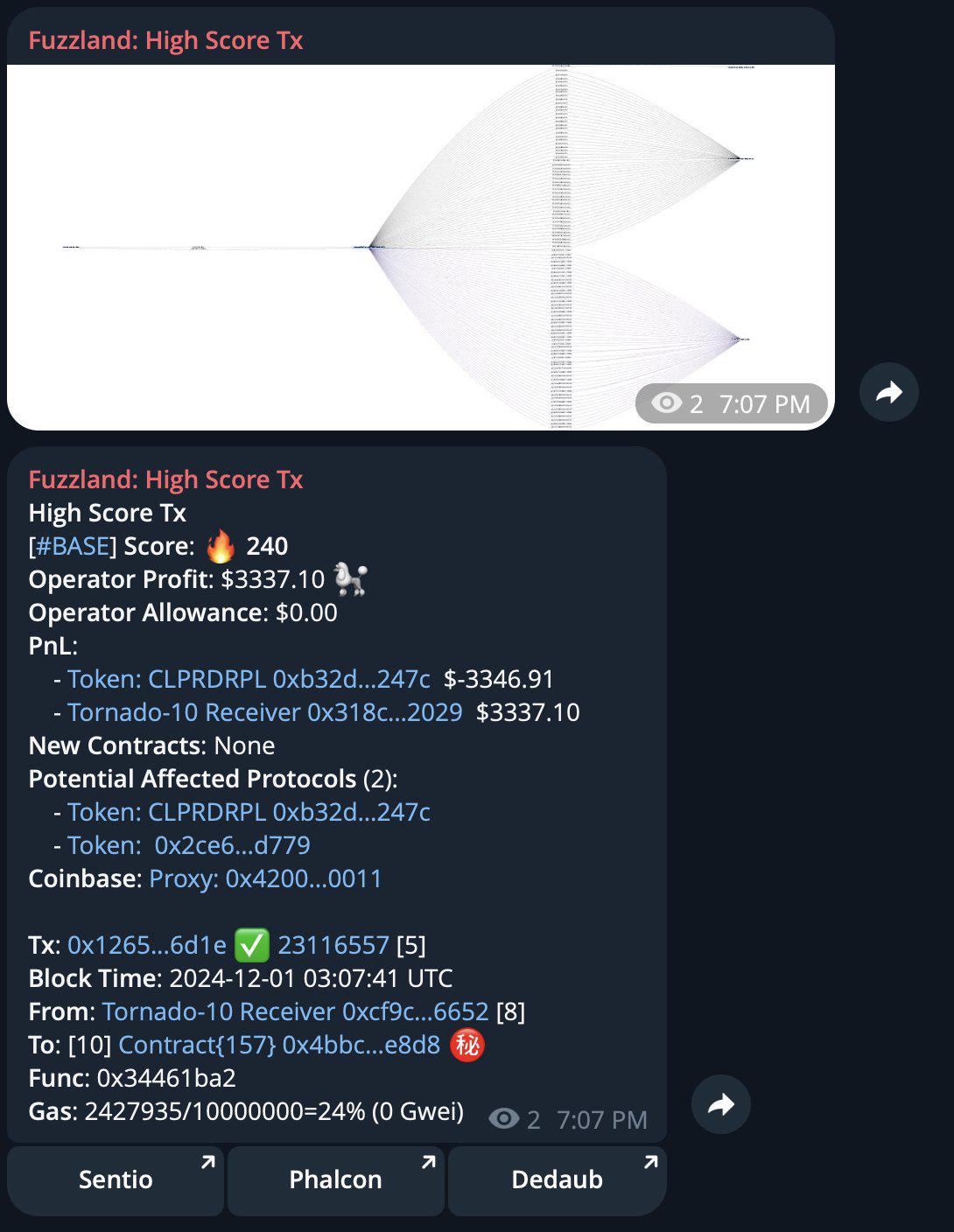
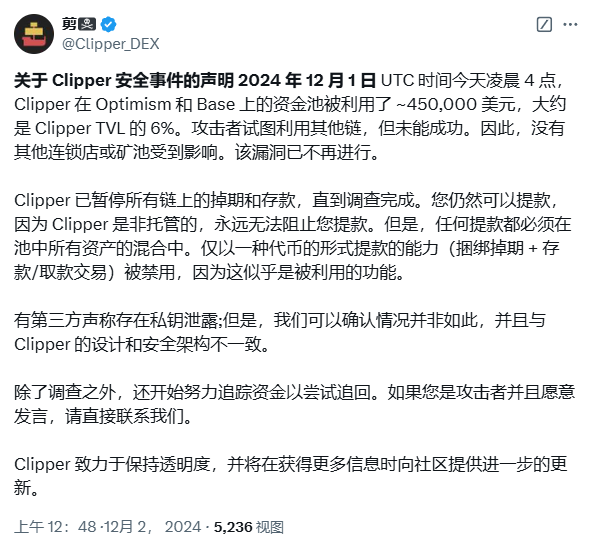
(1) 12月1日,安全机构 fuzzland 联创 @shoucccc 发推表示,去中心化交易平台 Clipper 因 API 漏洞(如私钥泄露)而遭到黑客攻击。目前损失超过 50 万美元,650 万美元面临风险,并建议用户立即提现。而第二天,去中心化交易所(DEX)Clipper 澄清称,其提款功能中存在漏洞,导致其协议最近遭到黑客攻击,损失金额达 45 万美元,而非“第三方”所说的私钥泄露。
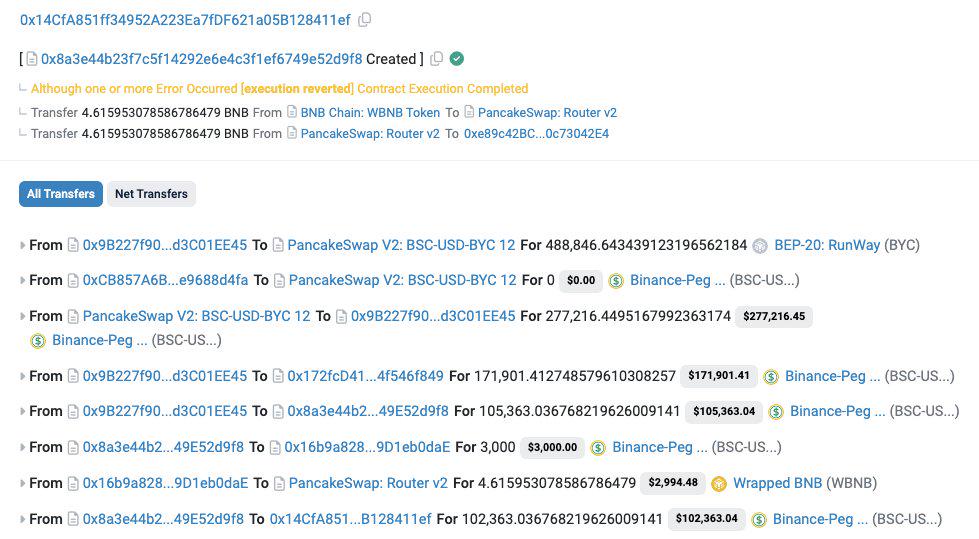
(2) 12月3日,据慢雾安全团队监测,RunWay (BYC) 疑似在 BSC 上遭攻击,损失约 10 万美元。
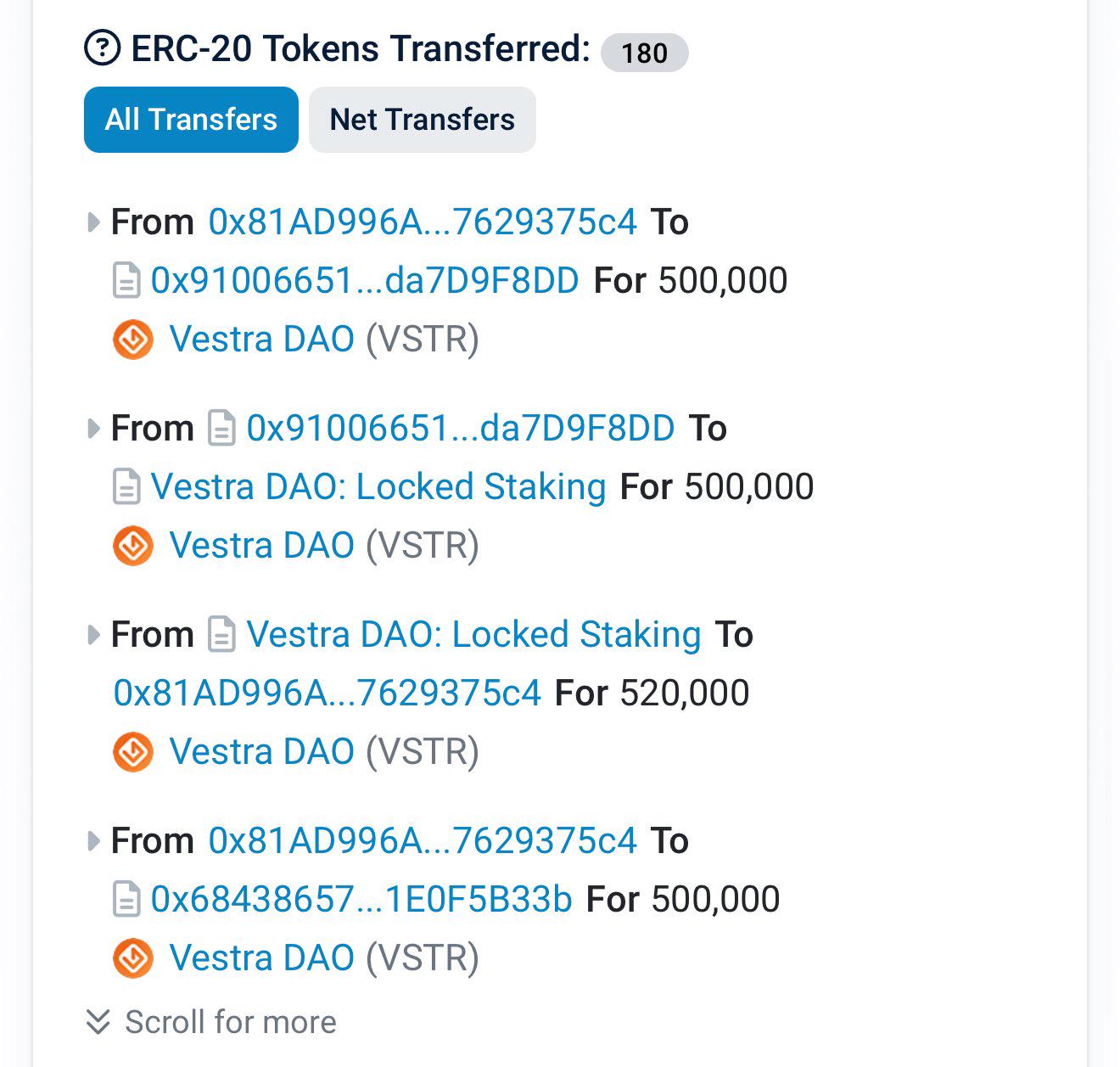
(3) 12月4日,安全公司Fuzzland联合创始人Chaofan Shou在X平台表示:“Vestra DAO刚刚遭到黑客攻击,目前仍在继续。已损失48万美元,未来可能还会损失更多。建议立即撤回质押并撤回流动性。”
(4) 12月10日,零时科技项目团队监控到一起针对 Base 上的项目 CloberDEX 的链上攻击事件,本次漏洞成因主要是因为 CloberDEX 项目方合约在获取销毁 LP Token 的代码中没有进行重入检测和防护,且更新状态变量在合约调用之后,最终导致攻击者利用该重入漏洞掏空项目方的WETH 。
详细攻击分析可点此链接:
https://mp.weixin.qq.com/s/ff0YJBuZiaVBIIUZlarXRQ
(5) 12月15日,零时科技项目团队监控到一起针对 BnbSmartChain 上的项目 DCFToken 的链上攻击事件,被攻击的项目为 DCFToken ,攻击者通过此次攻击获利约为 8800 USD 。本次漏洞成因主要是因为 DCFToken 项目方合约在获取 DCFToken 的价格时,通过单一来源PancakeSwapV2 来计算,导致价格被攻击者操纵,最终利用价差套利。
详细攻击分析可点此链接:
https://mp.weixin.qq.com/s/DDadR1nOyYl-dPi5zwLLSQ
(6) 12月24日,据Scam Sniffer监测,一名受害者因假冒Zoom恶意软件损失了100万美元,与us04-zoom[.]us威胁行为者有关。目前私钥盗窃恶意软件案件上升,应严格验证来源,并在安装前进行安全扫描。此前,X平台用户Lsp(@lsp8940)发帖表示,“钱包被盗损失100万枚Usd0++,黑客伪装了一个推特,通过我的推特互动信息,伪装成我的朋友,然后对方说要对项目发展和我一起聊天开个会,发了zoom链接给我,我电脑本身有zoom,但是之前用zoom的时候老有问题,需要重新安装,所以网页提示需要重新安装的时候,我重新安装了,醒来发现已经被盗了。”
(7) 12月29日,FEG 项目遭攻击,损失约 100 万美元,据分析 ,此次事件的根本原因似乎是与底层 Wormhole 跨链桥集成时出现的可组合性问题,该桥用于跨链消息和代币的传输。
Rug Pull / 钓鱼诈骗
典型安全事件9 起
(1) 12月1日,0x32b8 开头地址在签署网络钓鱼“许可证”签名后损失了 $1.45M 的 Aave USDC。
(2) 12月3日,0x95d1 开头地址在签署网络钓鱼“批准”交易后损失了 $1.41M。
(3) 12月5日,0x30f8 开头地址因网络钓鱼攻击损失了 2.77 BTC ($284K+) 退出 MEXC不到 1 小时后落入“Increase Approval”网络钓鱼签名。
(4) 12月8日,0x16f5 开头地址且有$PEPE持有者通过签署恶意的 “increaseAllowance”交易损失了 135 美元。
(5) 12月9日,一名受害者在点击受感染的 WallStreetBets X 帐户的网络钓鱼链接后损失了 $2.2M。据分析显示,网络钓鱼网站中使用了一些网站的 XSS 漏洞。
(6) 12月11日,0x7a12 开头地址在签署网络钓鱼交易后损失了价值 $7.8M 的 SolvBTC。
(7) 12月18日,0xae4f 开头地址在签署“许可证”网络钓鱼签名后损失了价值 492K 美元的 aEthWETH 和 aPolWMATIC。
(8) 12月20日,0x8458 开头地址在签署“setApprovalForAll”网络钓鱼交易后,丢失了 1 Doodles。
(9) 12月20日,0x61ccc 开头地址在签署“increaseAllowance”网络钓鱼交易后损失了 $200K。
总结
2024年最后几个月,加密货币诈骗、漏洞和黑客攻击造成的损失逐渐减少,12月是全年黑客攻击最少的月份。而漏洞造成了大部分损失,12月份攻击者窃取了2670万美元。
零时科技安全团队建议项目方始终保持警惕,提醒广大用户谨防钓鱼攻击。建议用户在参与项目前充分了解项目的背景、团队,谨慎选择投资项目。此外也需做好内部安全培训和权限管理,在项目上线前寻找专业的安全公司进行审计并做好项目背景调查。






