在区块链技术不断成熟与生态日趋复杂的今天,MEV(最大可提取价值)原本被视为交易排序缺陷所引发的偶发漏洞,正逐步演变成一种高度复杂、系统性的利润收割机制。其中,三明治攻击因其利用交易排序权在目标交易前后插入自有交易,操控资产价格实现低买高卖套利而备受关注,已成为DeFi生态中最具争议且破坏性的攻击手法之一。
一、MEV与三明治攻击的基本概念MEV三明治攻击的演变与现状及案例
MEV的来源与技术演变:
MEV(Maximum Extractable Value)最初称为矿工可提取价值,是指矿工或验证者在区块构建过程中,利用对交易顺序、包含或排除权的操控,所能额外获得的经济收益。其理论基础在于区块链交易的公开性和内存池中交易排序的不确定性。随着闪电贷、交易打包(bundle)等工具的发展,原本零星的套利机会逐步被放大,形成了完整的利润收割链条。由最初偶发事件到如今系统化、工业化的套利模式,MEV不仅存在于以太坊,也在Solana、币安智能链等多条链上呈现出不同的特征。
三明治攻击的原理:
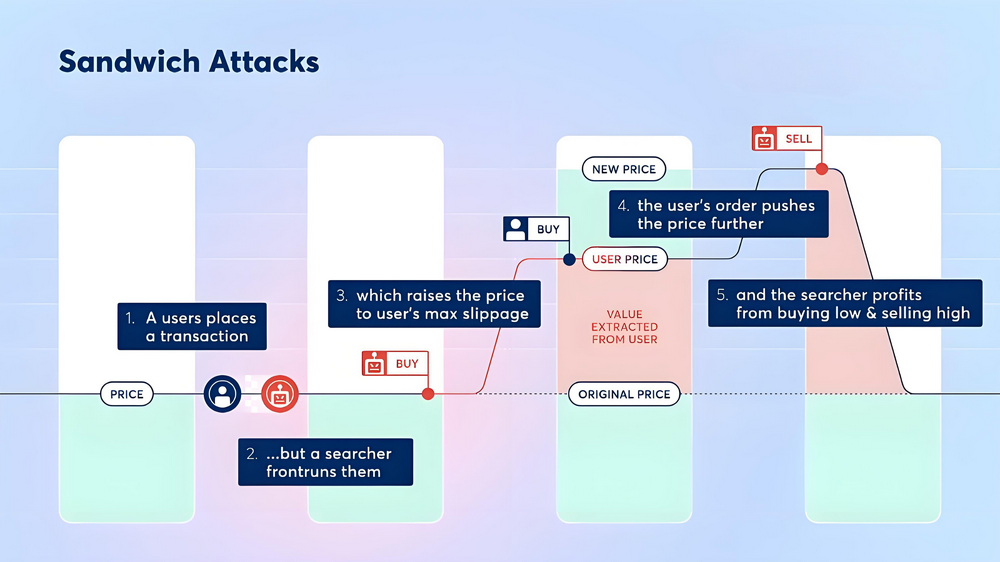
三明治攻击是MEV提取中一种典型的操作手段,攻击者利用对内存池交易的实时监控能力,在目标交易(Victim Transaction)前后分别提交交易,形成“前置(front-run)—目标交易—后置(back-run)”的交易顺序,进而通过价格操纵实现套利。其核心原理包括:
-
前置交易(Front-Run):当攻击者检测到一笔大额或滑点较高的交易时,立即提交自己的买单,以推高或压低市场价格。
-
目标交易夹击(Victim Transaction):目标交易在价格被操控后执行,因实际成交价格与预期价格存在明显偏差,使交易者承担额外成本。
-
后置交易(Back-Run):紧随目标交易之后,攻击者再提交反向交易,以高价卖出(或低价买入)先前获得的资产,从而锁定价差利润。
这种操作犹如将目标交易“夹”在自己两笔交易之间,故称为“三明治攻击”。
二、MEV三明治攻击的演变与现状及案例
(1) 从零星漏洞到系统性机制
最初,区块链网络中由于交易排序机制固有的不足,MEV攻击仅偶尔出现且规模较小。然而,随着DeFi生态交易量激增以及高频交易机器人和闪电贷等工具的不断发展,攻击者开始构建高度自动化的套利系统,将这种攻击方式从零星事件转变为系统化、工业化的套利模式。通过利用高速网络与精密算法,攻击者能够在极短时间内抢先部署前置与后置交易,利用闪电贷获得大额资金,并在同一交易中完成套利操作。当前,多个平台上已出现单笔交易即可获得数十万甚至上百万美元利润的案例,这一转变标志着MEV机制已经从偶发漏洞发展为成熟的利润收割体系。
(2) 不同平台特性的攻击模式
不同的区块链网络由于其设计理念、交易处理机制以及验证者结构等方面的差异,使得三明治攻击呈现出不同的实施特点。如:
-
以太坊:公开透明的内存池使得所有待确认交易信息均可被监控,攻击者往往通过支付更高Gas费来抢占交易打包顺序。为应对这一问题,以太坊生态内已陆续引入MEV-Boost和提议者-建设者分离(PBS)等机制,以期降低单一节点操控交易排序的风险。
-
Solana:虽然Solana没有传统的内存池,但由于验证者节点相对集中,部分节点甚至可能与攻击者勾结,提前泄露交易数据,使得攻击者能够快速捕捉并利用目标交易,从而使三明治攻击在该生态中频繁发生且获利规模较大。
-
币安智能链(BSC):尽管BSC的生态成熟度与以太坊有所差异,但其较低的交易成本和较为简化的结构也为部分套利行为提供了空间,各类机器人在此环境中同样能采用类似策略实现利润提取。
这种跨链环境的差异,促使攻击方式和利润分布在不同平台上各具特色,同时也对防范策略提出了更高要求。
(3) 最新数据与案例
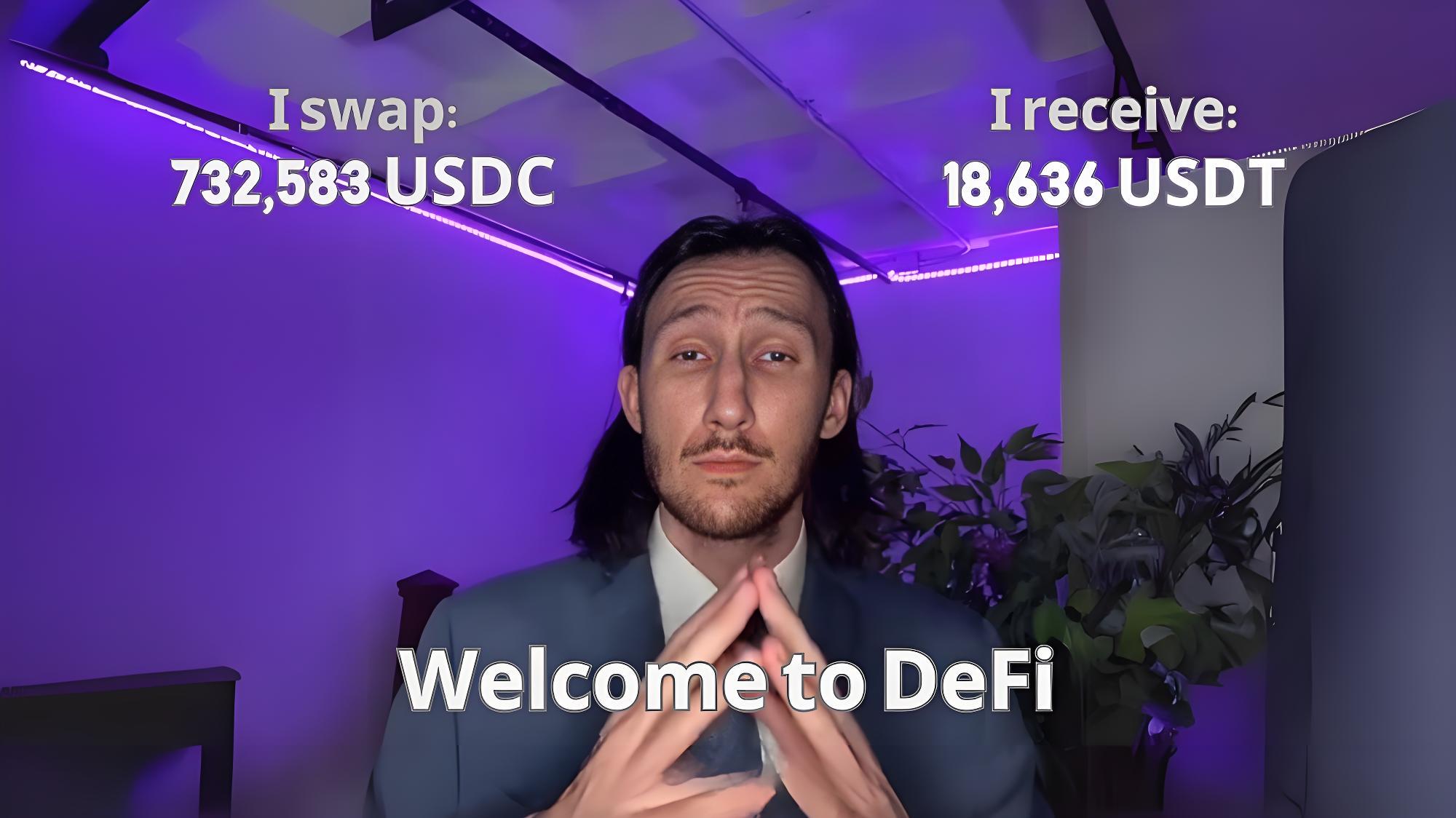
Uniswap平台案例:2025年3月13日,一笔发生在Uniswap V3上的交易中,一位交易者在进行价值约5个SOL的交易时,因遭遇三明治攻击导致资产损失高达73.2万美元。该事件显示,攻击者利用前置交易抢占区块打包权,在目标交易前后插入交易,致使受害者实际成交价格大幅偏离预期
Solana链上的持续演化:在Solana生态中,三明治攻击不仅频发,而且出现了新的攻击模式。部分验证者甚至疑似与攻击者勾结,通过泄露交易数据提前获知用户交易意图,进而实施精准夹击。这使得Solana链上部分攻击者的收益在短短几个月内就从数千万美元增长到上亿美元。
这些数据和案例表明,MEV三明治攻击不再是偶发事件,而是伴随着区块链网络日益增长的交易量和复杂性而呈现出系统化、工业化的特点。
三、三明治攻击的操作机制与技术挑战
随着整体市场交易量的持续扩大,MEV攻击的频率与单笔利润呈上升趋势,部分平台上三明治攻击的交易成本收入比甚至达到较高水平,以下为实施三明治攻击需要满足几个条件:
-
交易监听与捕捉:攻击者必须实时监控内存池中待确认的交易,识别出具有较大价格影响的交易。
-
优先打包权的竞争:利用更高的gas费或优先费,攻击者抢先将自己的交易打包入区块,确保在目标交易前后分别执行。
-
精确计算与滑点控制:在执行前置与后置交易时,必须精确计算交易量与预期滑点,既要推动价格波动,又要确保目标交易不会因超出设定滑点而失败。
实施这种攻击不仅需要高性能的交易机器人和快速的网络响应,还需要支付高额矿工贿赂费用(例如提高gas费),以确保交易优先级。这些成本构成了攻击者的主要支出,而在激烈竞争中,还可能出现多个机器人同时试图抢占同一目标交易,进一步压缩利润空间。这些技术与经济壁垒在激烈竞争的环境下不断促使攻击者更新算法与策略,同时也为防范机制的设计提供了理论依据。
四、行业应对与防范策略
针对普通用户的防范策略:
-
设置合理的滑点保护:在提交交易时应根据当前市场波动和预期流动性状况,合理设置滑点容忍度,避免因过低设置导致交易失败,也不因过高设置而被恶意夹击。
-
使用隐私交易工具:借助诸如私有RPC、订单打包拍卖等技术手段,将交易数据隐藏在公共内存池之外,降低被攻击的风险。
生态系统层面的技术改进建议:
-
交易排序与提议者-建设者分离(PBS):通过将区块构建与区块提议职责分离,限制单一节点对交易排序的控制权,从而降低验证者利用排序优势进行MEV提取的可能性。
-
MEV-Boost与透明化机制:引入第三方中继服务(Relay)和MEV-Boost等方案,使区块构建过程公开透明,减少对单一节点的依赖,提高整体竞争性。
-
链下订单流拍卖与外包机制:借助外包订单(例如CoW协议)与订单流拍卖机制,实现订单的批量撮合,既提升用户获得最佳价格的可能性,又使攻击者难以单独操作。
-
智能合约与算法升级:借助人工智能和机器学习技术,提高对链上数据异常波动的实时监控和预测能力,帮助用户提前规避风险;
随着DeFi生态系统的不断扩展,交易量与交易复杂性持续增加,MEV及其相关攻击手段将面临更多技术对抗和经济博弈。未来,除了技术手段的改进外,如何在确保去中心化特性与网络安全的同时合理分配经济激励,将成为业界共同关注的重要课题。
五、结语
MEV三明治攻击从最初的偶发漏洞演变为一种系统性利润收割机制,对DeFi生态和用户资产安全构成了严峻挑战。2025年的最新案例和数据表明,无论是在Uniswap还是Solana等主流平台上,三明治攻击的风险依然存在且不断升级。为保护用户资产与市场公平,区块链生态需要在技术创新、交易机制优化以及监管协同方面共同努力。只有这样,DeFi生态才能在创新与风险之间找到平衡,实现可持续发展。






